Networks
- 2. What is a network? A network consists of two or more computers that are linked in order to: share resources (such as printers and CD-ROMs), exchange files, or allow electronic communications
- 3. How are they linked? Computers on a network may be linked through: cables, telephone lines, radio waves, satellites or wireless technologies
- 4. The two basic types of networks include: Local Area Networks LAN (LAN) Wide Area Networks (WAN) WAN
- 5. Local area networks LANs are confined to a relatively small area such as a school or a building LANs usually have one computer designated as the file server Other computers are connected to the network by cables connecting network interface cards in each computer
- 6. Wide Area Networks WANs connect larger areas, such as whole states, or even the world. Transoceanic cables and satellites are used to connect WANs
- 7. Protocol A protocol is a set of PROTOCOL = rules that governs the SET OF RULES ABOUT communications COMMUNICATION between computers S BETWEEN NETWORKS! on a network These rules include guidelines that regulate the method of access, types of cabling and speed of data transfer
- 8. The most common protocols are: Ethernet Local Talk Protocol = a formal Token Ring description of a set of rules and conventions FDDI that govern how ATM devices on a network exchange information Did you ever wonder what HTTP in web addresses was about? It stands for HyperText Transfer Protocol
- 9. Ethernet Most widely used Uses an access method called CSMA/CD (Carrier Sense Multiple Access/Collision Detection
- 10. What does that mean? Each computer in the network ‘listens’ to the A bit like waiting for cable before sending your younger sister to anything through the get off the telephone network. If the network perhaps? is clear, the computer will transmit. If another computer is already transmitting on the cable, the computer will wait and try again when the line is clear
- 11. Ethernet (continued) Sometimes, two computers attempt to transmit at the same instant. When this happens, a collision occurs. Each computer then backs off and waits a random amount of time before attempting to retransmit.It is normal to have collisions using this method, CSMA/CD =Carrier but the delays caused by Sense Multiple collisions and transmissions is Access /Collision small, and does not effect Detection speed of transmission on the network
- 12. Ethernet (continued) Ethernet protocol allows for data to be transmitted over twisted pair, coaxial or fiber optic cable at a speed of 10 Mbps (more on that later)
- 13. Fast Ethernet To allow for faster transmission, the Ethernet protocol has developed a new standard that supports 100 Mbps Fast Ethernet requires the use of more expensive equipment and network cards
- 14. Gigabit Ethernet The Ethernet protocol has also developed a new One gigabit per standard that allows second = one transmission of 1 thousand Gbps (gigabit per megabits per second) second
- 15. Local Talk Local Talk is a network protocol that was developed by Apple for Macintosh computers Local Talk uses the CSMA/CA method (Carrier Sense Multiple Access with Collision Avoidance) which works in a similar way to CSMA/CD It is a lot slower than Ethernet (only 230 Kbps)
- 16. Token Ring Token ring protocol involves ‘token-passing’. It is not as A single electronic ‘token’ popular as moves around the ring from one computer to the next. If a Ethernet protocol computer wishes to transit and receives an empty token, it attaches data to the token which then proceeds around the ring until it comes to the computer the data is meant for.
- 17. FDDI Stands for Fiber Distributed Data Interface Is used mainly to connect two or more LANs, often over large distances Can operate over fiber optic cable at 100 Mbps
- 18. ATM Stands for Asynchronous Transfer Mode Transmit data at a speed of 155 Mbps and higher Works by transmitting all data in small packets of fixed size (other protocols transfer variable size packets) Like FDDI , is most often used to connect two or more LANs
- 19. Where does TCP/IP fit into all this??? TCP/IP is the protocol that is used for the transmission of information over the Internet IP (Internet Protocol) - the main delivery system for information over the Internet TCP (Transport Control Protocol) - used to break apart and rebuild information that travels over the Internet
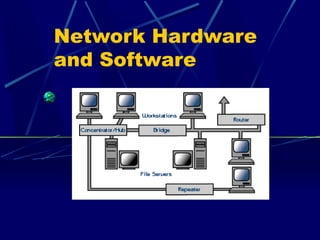
- 20. Network Hardware Network hardware includes: Computers Peripherals Interface cards and Other equipment needed to perform data processing and communications within the network
- 21. File servers A very fast computer with a large amount of RAM and storage space along with a fast network interface card The network operating system software resides on this computer
- 22. Workstations All computers connected to the file server on a network are called workstations
- 23. Network interface cards The network interface card (NIC) provides the physical connection between the network and the computer workstation. Most NICs are internal with the card fitting into an expansion slot in the computer. Three common network interface connections are Ethernet cards, Local Talk connectors and Token Ring cards
- 24. Ethernet cards The most common Network Interface Co-axial Cards are Ethernet cable cards They contain connections for either coaxial or twisted pair cables, Twisted pair cable or both
- 25. Concentrators / Hubs A concentrator is a device that provides a central connection point for cables from workstations, servers and peripherals Hubs are multi-slot concentrators
- 26. Switches While hubs provide an easy way to scale up and shorten the distance that the packets must travel to get from one node to another, they do not break up the actual network into discrete segments. That is where switches come in.
- 27. Switches (continued) A vital difference between a hub and a switch is that all the nodes connected to a hub share the bandwidth among themselves, while a device connected to a switch port has the full bandwidth all to itself. Think of a switch as a ‘clever’ hub
- 28. Repeaters A signal loses strength as it passes along a cable, so it is often necessary to boost the signal with a device called a repeater A repeater might be a separate device, or might be part of a concentrator
- 29. Bridges A bridge is a device that allows you to segment a large network into two smaller, more efficient networks
- 30. Routers A router translates information from one network to another The router directs traffic to prevent “head-on” collisions If you have a LAN that you want to connect to the Internet, you will need a router to serve as the translator between information on your LAN and the Internet
- 32. Cabling Network cabling is the medium through which information usually moves from one network device to another There are several different types of cable commonly used in LANS Some networks use a variety of cable types within the one network
- 33. Unshielded Twisted Pair (UTP) Cable Twisted pair cables come in two varieties: shielded and unshielded. Unshielded (UTP) is the most popular Shielded twisted pair is used only in environments where there may be electrical interference
- 34. UTP (continued) UTP has four pairs of wires inside the jacket Each pair is twisted with a different number of twists per inch to help eliminate interference from adjacent pairs
- 35. UTP Connector The standard connector for UTP cabling is an RJ-45. It looks like a telephone style connection
- 36. Coaxial cable Coaxial cable has a single copper conductor at its centre with a plastic layer between the centre conductor and the braided metal shield Although coaxial cabling is difficult to install, it is highly resistant to signal interference
- 37. Coaxial cable connectors The most common type of connector used with coaxial cables is the BNC connector
- 38. Fiber Optic Cable Fiber optic cabling consists of a center glass core surrounded by several layers of protective materials It transmits light rather than electronic signals It is the standard for connecting networks between buildings, due to its immunity to the effects of moisture and light
- 39. Fiber Optic (continued) Fiber optic cable has the ability to transmit signals over much longer distances than coaxial or twisted pair It can also carry information at vastly greater speeds Fiber optic cable is more difficult to install than other cabling
- 40. Wireless LANS Wireless networks use high frequency radio signals to communicate between the workstations and the fileserver or hubs. Disadvantages of wireless networks are: they are expensive (relatively), provide poor security, are susceptible to interference and are slower than cabled networks
- 41. Network Operating Software Network operating systems co-ordinate the activities of multiple computers across a network The two major types of network OS are: Peer-to-peer Client/server
- 42. Peer to peer network OS In peer to peer network OS, there is no file server or central management source; all computers are considered equal Peer to peer networks are design primarily for small to medium LANS AppleShare and Windows for Workgroups are examples of programs that can function as peer to peer
- 43. Client/Server network OS Client/server network OS centralise functions and applications in one or more dedicated file servers. The file server provides access to resources and provides security Novelle Netware and Windows NT Server are examples of client/server network operating systems
- 44. Topology The physical topology of a network refers to the configuration of cables, computers and other peripherals. The main types of network topologies are: Linear Bus Star Ring Tree or Hybrid
- 45. Linear Bus A linear bus topology consists of a main run of cable with a terminator at each end. All servers workstations and peripherals are connected to the linear cable
- 46. Star A star network is designed with each node (file server, workstation, peripheral) connected directly to a central network hub or server
- 47. Ring A ring network is one where all workstations and other devices are connected in a continuous loop. There is no central server
- 48. Tree or hybrid A tree or hybrid topology combines characteristics of linear bus and star and/or ring topologies. It consists of groups of star-configured workstations connected to a linear bus backbone cable