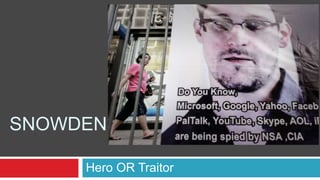
Snowden -Hero OR Traitor
•Télécharger en tant que PPTX, PDF•
5 j'aime•6,508 vues
Signaler
Partager
Signaler
Partager
Recommandé
Contenu connexe
Tendances
Tendances (20)
analysis of russia ukrain war class 9th final ppt.pptx

analysis of russia ukrain war class 9th final ppt.pptx
Aarushi Talvar Murder Case | Legal Aspects of Business

Aarushi Talvar Murder Case | Legal Aspects of Business
Similaire à Snowden -Hero OR Traitor
Similaire à Snowden -Hero OR Traitor (12)
Reply to below posting in a paragraph of at least five sentences by.docx

Reply to below posting in a paragraph of at least five sentences by.docx
Edward J. Snowden, the thirty-year-old former National Security Agen.docx

Edward J. Snowden, the thirty-year-old former National Security Agen.docx
Article CritiqueThis assignment provides you with an opportunity t.docx

Article CritiqueThis assignment provides you with an opportunity t.docx
Securing our libertyCommonweal. 140.12 (July 12, 2013) p5.Cop.docx

Securing our libertyCommonweal. 140.12 (July 12, 2013) p5.Cop.docx
Krempley 1POL 300GoogleMulti-National Corporations, Inter.docx

Krempley 1POL 300GoogleMulti-National Corporations, Inter.docx
Edward Snowden was a whistleblower and former NSA contractor, in the.docx

Edward Snowden was a whistleblower and former NSA contractor, in the.docx
Dernier
+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...

+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...?#DUbAI#??##{{(☎️+971_581248768%)**%*]'#abortion pills for sale in dubai@
Dernier (20)
Repurposing LNG terminals for Hydrogen Ammonia: Feasibility and Cost Saving

Repurposing LNG terminals for Hydrogen Ammonia: Feasibility and Cost Saving
DEV meet-up UiPath Document Understanding May 7 2024 Amsterdam

DEV meet-up UiPath Document Understanding May 7 2024 Amsterdam
Strategize a Smooth Tenant-to-tenant Migration and Copilot Takeoff

Strategize a Smooth Tenant-to-tenant Migration and Copilot Takeoff
Finding Java's Hidden Performance Traps @ DevoxxUK 2024

Finding Java's Hidden Performance Traps @ DevoxxUK 2024
CNIC Information System with Pakdata Cf In Pakistan

CNIC Information System with Pakdata Cf In Pakistan
Apidays New York 2024 - The value of a flexible API Management solution for O...

Apidays New York 2024 - The value of a flexible API Management solution for O...
AWS Community Day CPH - Three problems of Terraform

AWS Community Day CPH - Three problems of Terraform
+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...

+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...
Apidays New York 2024 - APIs in 2030: The Risk of Technological Sleepwalk by ...

Apidays New York 2024 - APIs in 2030: The Risk of Technological Sleepwalk by ...
Cloud Frontiers: A Deep Dive into Serverless Spatial Data and FME

Cloud Frontiers: A Deep Dive into Serverless Spatial Data and FME
Exploring the Future Potential of AI-Enabled Smartphone Processors

Exploring the Future Potential of AI-Enabled Smartphone Processors
Cloud Frontiers: A Deep Dive into Serverless Spatial Data and FME

Cloud Frontiers: A Deep Dive into Serverless Spatial Data and FME
Spring Boot vs Quarkus the ultimate battle - DevoxxUK

Spring Boot vs Quarkus the ultimate battle - DevoxxUK
Boost Fertility New Invention Ups Success Rates.pdf

Boost Fertility New Invention Ups Success Rates.pdf
Connector Corner: Accelerate revenue generation using UiPath API-centric busi...

Connector Corner: Accelerate revenue generation using UiPath API-centric busi...
Snowden -Hero OR Traitor
- 2. Who is Edward Snowden Edward Joseph Snowden, June 21, 1983 (age 30), Wilmington, North Carolina Residence: Russia (temporary asylum) Nationality: American Occupation: System administrator Known for :Revealing details of classified United States government surveillance programs Criminal charge :Theft of government property, unauthorized communication of national defence information, and wilful communication of classified intelligence to an unauthorized person (June 2013). Awards :Sam Adams Award
- 3. How NSA Works? The NSA plays "three degrees of Kevin Bacon." e.g. With a phone with 260 contacts , 4,569,760,000 other people can be monitored Real Time Access to Phone and Internet Traffic The NSA asks for information companies already have The NSA sifts through everything that crosses the border. The NSA assumes you're foreign until proven otherwise
- 4. Issue? Guardian started publishing a series of exposes revealing NSA operated a major web of spying programs in May 2013. Snowden identity was revealed on 9th June.
- 5. Correctness of his actions NSA Claims wiretapping was not intrusion to US citizens Privacy but legitimate way to intercept terrorist activities or communications “ he wasn’t blowing the whistle on anything illegal; he was exposing something that failed to meet his own standards of propriety. The question, of course, is whether the government can function when all of its employees (and contractors) can take it upon themselves to sabotage the programs they don’t like. That’s what Snowden has done.”
- 6. Correctness of his actions Snowden contends that he simply wanted the public to know that government was watching and recording people who were doing no wrong. “to inform the public as to that which is done in their name and that which is done against them”
- 7. The NSA view of Americans What People Think Polls between June and August 2013
- 9. Discussions 1.What is the NSA mission? How deep is the involvement of corporate America in this whole scheme? Is Security of country is more important than Privacy? Credit:Mapsofworld
- 10. Widescreen Test Pattern (16:9) Aspect Ratio Test (Should appear circular) 4x3 16x9
