How to Stay Safe at Conferences
•
0 j'aime•3,539 vues
By following these instructions you can decrease your vulnerability to numerous risks faced while attending security conferences. Proceed with caution, and recognize that this landscape is constantly evolving. A major takeaway from these events is that no security measure is ever one hundred percent safe.
Signaler
Partager
Signaler
Partager
Télécharger pour lire hors ligne
Recommandé
Contenu connexe
Plus de Digital Shadows
Plus de Digital Shadows (20)
Mapping the ASD Essential 8 to the Mitre ATTACK™ framework

Mapping the ASD Essential 8 to the Mitre ATTACK™ framework
Mitre ATT&CK and the Mueller GRU Indictment: Lessons for Organizations

Mitre ATT&CK and the Mueller GRU Indictment: Lessons for Organizations
Mitre ATTACK and the North Korean Regime-Backed Programmer

Mitre ATTACK and the North Korean Regime-Backed Programmer
Digital Shadows and Demisto Enterprise Integration Datasheet

Digital Shadows and Demisto Enterprise Integration Datasheet
Digital Shadows and Palo Alto Networks Integration Datasheet

Digital Shadows and Palo Alto Networks Integration Datasheet
Energy and Utilities Firm Increases Productivity by Reducing False Positives

Energy and Utilities Firm Increases Productivity by Reducing False Positives
Source Code and Admin Password Shared on Public Site by Developer

Source Code and Admin Password Shared on Public Site by Developer
Mobile Application Detected Impersonating Company Brand

Mobile Application Detected Impersonating Company Brand
Digital Shadows Helps Large Retailer Navigate Extortion Attempt

Digital Shadows Helps Large Retailer Navigate Extortion Attempt
Company Named on Target List for Hacktivist Campaign

Company Named on Target List for Hacktivist Campaign
Dernier
+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...

+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...?#DUbAI#??##{{(☎️+971_581248768%)**%*]'#abortion pills for sale in dubai@
Dernier (20)
HTML Injection Attacks: Impact and Mitigation Strategies

HTML Injection Attacks: Impact and Mitigation Strategies
Powerful Google developer tools for immediate impact! (2023-24 C)

Powerful Google developer tools for immediate impact! (2023-24 C)
AWS Community Day CPH - Three problems of Terraform

AWS Community Day CPH - Three problems of Terraform
Polkadot JAM Slides - Token2049 - By Dr. Gavin Wood

Polkadot JAM Slides - Token2049 - By Dr. Gavin Wood
Boost PC performance: How more available memory can improve productivity

Boost PC performance: How more available memory can improve productivity
How to Troubleshoot Apps for the Modern Connected Worker

How to Troubleshoot Apps for the Modern Connected Worker
Apidays Singapore 2024 - Building Digital Trust in a Digital Economy by Veron...

Apidays Singapore 2024 - Building Digital Trust in a Digital Economy by Veron...
+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...

+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...
Mastering MySQL Database Architecture: Deep Dive into MySQL Shell and MySQL R...

Mastering MySQL Database Architecture: Deep Dive into MySQL Shell and MySQL R...
Exploring the Future Potential of AI-Enabled Smartphone Processors

Exploring the Future Potential of AI-Enabled Smartphone Processors
Connector Corner: Accelerate revenue generation using UiPath API-centric busi...

Connector Corner: Accelerate revenue generation using UiPath API-centric busi...
Why Teams call analytics are critical to your entire business

Why Teams call analytics are critical to your entire business
From Event to Action: Accelerate Your Decision Making with Real-Time Automation

From Event to Action: Accelerate Your Decision Making with Real-Time Automation
Strategies for Landing an Oracle DBA Job as a Fresher

Strategies for Landing an Oracle DBA Job as a Fresher
Apidays New York 2024 - The value of a flexible API Management solution for O...

Apidays New York 2024 - The value of a flexible API Management solution for O...
The 7 Things I Know About Cyber Security After 25 Years | April 2024

The 7 Things I Know About Cyber Security After 25 Years | April 2024
Scaling API-first – The story of a global engineering organization

Scaling API-first – The story of a global engineering organization
How to Stay Safe at Conferences
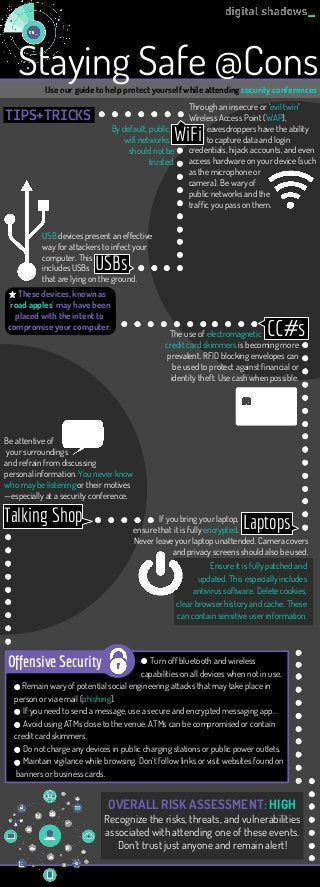
- 1. Staying Safe @ConsUse our guide to help protect yourself while attending security conferences TIPS TRI S WiFi Through an insecure or ‘evil twin’ Wireless Access Point (WAP), eavesdroppers have the ability to capture data and login credentials, hijack accounts, and even access hardware on your device (such as the microphone or camera). Be wary of public networks and the traffic you pass on them. USBs By default, public . wifi networks . should not be trusted. USB devices present an effective way for attackers to infect your computer. This includes USBs that are lying on the ground. These devices, known as ‘road apples’ may have been placed with the intent to compromise your computer. CC#sThe use of electromagnetic . credit card skimmers is becoming more prevalent. RFID blocking envelopes can be used to protect against financial or identity theft. Use cash when possible. LaptopsIf you bring your laptop, . ensure that it is fully encrypted. . Never leave your laptop unattended. Camera covers and privacy screens should also be used. Ensure it is fully patched and updated. This especially includes antivirus software. Delete cookies, clear browser history and cache. These can contain sensitive user information. Talking Shop Be attentive of your surroundings and refrain from discussing personal information. You never know who may be listening or their motives —especially at a security conference. Turn off bluetooth and wireless capabilities on all devices when not in use. Remain wary of potential social engineering attacks that may take place in person or via email (phishing). If you need to send a message, use a secure and encrypted messaging app. Avoid using ATMs close to the venue. ATMs can be compromised or contain credit card skimmers. Do not charge any devices in public charging stations or public power outlets. Maintain vigilance while browsing. Don’t follow links or visit websites found on banners or business cards. Offensive Security OVERALL RISK ASSESSMENT: HIGH Recognize the risks, threats, and vulnerabilities associated with attending one of these events. Don’t trust just anyone and remain alert!
