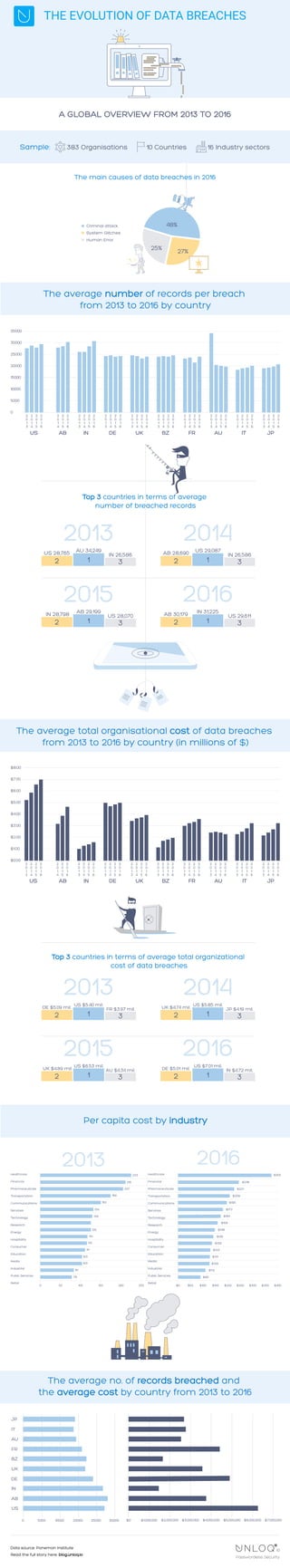
The Evolution Of Data Breaches From 2013 To 2016
- 1. A GLOBAL OVERVIEW FROM 2013 TO 2016 THE EVOLUTION OF DATA BREACHES Criminal attack System Glitches Human Error 48% 25% 27% 2 0 1 3 2 0 1 4 2 0 1 5 2 0 1 6 2 0 1 4 2 0 1 5 2 0 1 6 2 0 1 3 2 0 1 4 2 0 1 5 2 0 1 6 2 0 1 3 2 0 1 4 2 0 1 5 2 0 1 6 2 0 1 3 2 0 1 4 2 0 1 5 2 0 1 6 2 0 1 3 2 0 1 4 2 0 1 5 2 0 1 6 2 0 1 3 2 0 1 4 2 0 1 5 2 0 1 6 2 0 1 3 2 0 1 4 2 0 1 5 2 0 1 6 2 0 1 3 2 0 1 4 2 0 1 5 2 0 1 6 US AB IN DE UK BZ FR AU IT JP 2 0 1 3 2 0 1 4 2 0 1 5 2 0 1 6 AU 34,249US 28,765 IN 26,586 1 32 2013 AB 29,199IN 28,798 US 28,070 1 32 IN 31,225AB 30,179 US 29,611 1 32 2015 US 29,087AB 28,690 IN 26,586 1 32 2014 2016 US $5.40 mil. DE $5.09 mil. FR $3.97 mil. 1 32 2013 US $6.53 mil. UK $4.89 mil. AU $4.34 mil. 1 32 US $7.01 mil. DE $5.01 mil. IN $4.72 mil. 1 32 2015 US $5.85 mil. UK $4.74 mil. JP $4.19 mil. 1 32 2014 2016 2 0 1 3 2 0 1 4 2 0 1 5 2 0 1 6 2 0 1 4 2 0 1 5 2 0 1 6 2 0 1 3 2 0 1 4 2 0 1 5 2 0 1 6 2 0 1 3 2 0 1 4 2 0 1 5 2 0 1 6 2 0 1 3 2 0 1 4 2 0 1 5 2 0 1 6 2 0 1 3 2 0 1 4 2 0 1 5 2 0 1 6 2 0 1 3 2 0 1 4 2 0 1 5 2 0 1 6 2 0 1 3 2 0 1 4 2 0 1 5 2 0 1 6 2 0 1 3 2 0 1 4 2 0 1 5 2 0 1 6 2 0 1 3 2 0 1 4 2 0 1 5 2 0 1 6 Healthcare Financial Pharmaceuticals Transportation Communications Services Technology Research Energy Hospitality Consumer Education Media Industrial Public Services Retail 233 215 207 169 150 134 129 125 114 113 111 103 103 81 78 Healthcare Financial Pharmaceuticals Transportation Communications Services Technology Research Energy Hospitality Consumer Education Media Industrial Public Services Retail $8.00 $7.00 $6.00 $5.00 $4.00 $3.00 $2.00 $1.00 $0.00 35000 30000 25000 20000 15000 10000 5000 0 0 300005000 10000 20000 25000 $0 $5,000,000$1,000,000 $2,000,000 $3,000,000 $4,000,000 $7,000,000$6,000,000 2013 2016 0 25050 100 150 200 $0 $250 $300 $350 $400$50 $100 $150 $200 The main causes of data breaches in 2016 Sample: 383 Organisations 10 Countries 16 Industry sectors US AB IN DE UK BZ FR AU IT JP Passwordless Security
