Recommandé
É possível unir a agilidade das metodologias ágeis com a burocracia do MPS.Br...

É possível unir a agilidade das metodologias ágeis com a burocracia do MPS.Br...Thielle Cathia D'Paula
Contenu connexe
En vedette
É possível unir a agilidade das metodologias ágeis com a burocracia do MPS.Br...

É possível unir a agilidade das metodologias ágeis com a burocracia do MPS.Br...Thielle Cathia D'Paula
En vedette (16)
É possível unir a agilidade das metodologias ágeis com a burocracia do MPS.Br...

É possível unir a agilidade das metodologias ágeis com a burocracia do MPS.Br...
Similaire à Digital signature
Similaire à Digital signature (20)
How to offer a trustworhty environment on the web?

How to offer a trustworhty environment on the web?
InfoSecurity Europe 2015 - Identities Exposed by David Johansson

InfoSecurity Europe 2015 - Identities Exposed by David Johansson
Certificate fundamental from avaya smgr perspective

Certificate fundamental from avaya smgr perspective
Digital signature
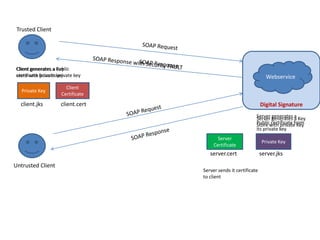
- 1. Digital Signature Webservice Trusted Client Untrusted Client Server generates a Key Store with private Key Private Key server.jks Client generates a key store with private key Private Key client.jks Server generates a Public certificate from its private key Server Certificate server.cert Client generates a Public certificate from its private key Client Certificate client.cert Server sends it certificate to client
- 2. Trusted Client Untrusted Client Private Key client.jks Digital Signature Webservice Private Key server.jks Client Certificate client.cert Server Certificate server.cert Client imports the server certificate into its keystore client.jks Server imports the client certificate into its keystore
- 3. Private Key Server Certificate Digital Signature Webservice Private Key server.jks Client Certificate client.jks Client Digital signs the input SOAP message using server’s certificate Trusted Client Untrusted Client Digitally signed SOAP Message