What is Ransomware
•Télécharger en tant que PPTX, PDF•
0 j'aime•438 vues
what is malware what is Ransomeware
Signaler
Partager
Signaler
Partager
Contenu connexe
Tendances
Tendances (20)
Cybersecurity Attack Vectors: How to Protect Your Organization

Cybersecurity Attack Vectors: How to Protect Your Organization
Ethical Hacking n VAPT presentation by Suvrat jain

Ethical Hacking n VAPT presentation by Suvrat jain
Similaire à What is Ransomware
Ransomware : A cyber crime without solution ? by Prashant Mali

Ransomware : A cyber crime without solution ? by Prashant MaliAdv. Prashant Mali ♛ [Bsc(Phy),MSc(Comp Sci), CCFP,CISSA,LLM]
Similaire à What is Ransomware (20)
CyberSecurity presentation for basic knowledge about this topic

CyberSecurity presentation for basic knowledge about this topic
Ransomware : A cyber crime without solution ? by Prashant Mali

Ransomware : A cyber crime without solution ? by Prashant Mali
Get Smart about Ransomware: Protect Yourself and Organization

Get Smart about Ransomware: Protect Yourself and Organization
(Training) Malware - To the Realm of Malicious Code

(Training) Malware - To the Realm of Malicious Code
Malware detection how to spot infections early with alien vault usm

Malware detection how to spot infections early with alien vault usm
Plus de jeetendra mandal
Plus de jeetendra mandal (20)
Eventual consistency vs Strong consistency what is the difference

Eventual consistency vs Strong consistency what is the difference
Difference between Database vs Data Warehouse vs Data Lake

Difference between Database vs Data Warehouse vs Data Lake
Difference between Client Polling vs Server Push vs Websocket vs Long Polling

Difference between Client Polling vs Server Push vs Websocket vs Long Polling
Difference between TLS 1.2 vs TLS 1.3 and tutorial of TLS2 and TLS2 version c...

Difference between TLS 1.2 vs TLS 1.3 and tutorial of TLS2 and TLS2 version c...
Carrier Advice for a JAVA Developer How to Become a Java Programmer

Carrier Advice for a JAVA Developer How to Become a Java Programmer
How to become a Software Tester Carrier Path for Software Quality Tester

How to become a Software Tester Carrier Path for Software Quality Tester
How to become a Software Engineer Carrier Path for Software Developer

How to become a Software Engineer Carrier Path for Software Developer
Microservice Architecture Software Architecture Microservice Design Pattern

Microservice Architecture Software Architecture Microservice Design Pattern
Top 5 Software Architecture Pattern Event Driven SOA Microservice Serverless ...

Top 5 Software Architecture Pattern Event Driven SOA Microservice Serverless ...
Disaster Recovery vs Data Backup what is the difference

Disaster Recovery vs Data Backup what is the difference
Dernier
Dernier (20)
%in Hazyview+277-882-255-28 abortion pills for sale in Hazyview

%in Hazyview+277-882-255-28 abortion pills for sale in Hazyview
%in Lydenburg+277-882-255-28 abortion pills for sale in Lydenburg

%in Lydenburg+277-882-255-28 abortion pills for sale in Lydenburg
introduction-to-automotive Andoid os-csimmonds-ndctechtown-2021.pdf

introduction-to-automotive Andoid os-csimmonds-ndctechtown-2021.pdf
call girls in Vaishali (Ghaziabad) 🔝 >༒8448380779 🔝 genuine Escort Service 🔝✔️✔️

call girls in Vaishali (Ghaziabad) 🔝 >༒8448380779 🔝 genuine Escort Service 🔝✔️✔️
%in Harare+277-882-255-28 abortion pills for sale in Harare

%in Harare+277-882-255-28 abortion pills for sale in Harare
Payment Gateway Testing Simplified_ A Step-by-Step Guide for Beginners.pdf

Payment Gateway Testing Simplified_ A Step-by-Step Guide for Beginners.pdf
Crypto Cloud Review - How To Earn Up To $500 Per DAY Of Bitcoin 100% On AutoP...

Crypto Cloud Review - How To Earn Up To $500 Per DAY Of Bitcoin 100% On AutoP...
OpenChain - The Ramifications of ISO/IEC 5230 and ISO/IEC 18974 for Legal Pro...

OpenChain - The Ramifications of ISO/IEC 5230 and ISO/IEC 18974 for Legal Pro...
%+27788225528 love spells in Atlanta Psychic Readings, Attraction spells,Brin...

%+27788225528 love spells in Atlanta Psychic Readings, Attraction spells,Brin...
8257 interfacing 2 in microprocessor for btech students

8257 interfacing 2 in microprocessor for btech students
call girls in Vaishali (Ghaziabad) 🔝 >༒8448380779 🔝 genuine Escort Service 🔝✔️✔️

call girls in Vaishali (Ghaziabad) 🔝 >༒8448380779 🔝 genuine Escort Service 🔝✔️✔️
Architecture decision records - How not to get lost in the past

Architecture decision records - How not to get lost in the past
%in Midrand+277-882-255-28 abortion pills for sale in midrand

%in Midrand+277-882-255-28 abortion pills for sale in midrand
Right Money Management App For Your Financial Goals

Right Money Management App For Your Financial Goals
What is Ransomware
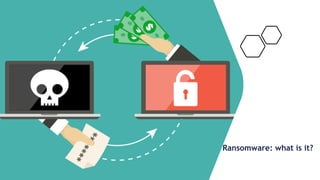
- 1. Ransomware: what is it?
- 4. What Is Ransomware? Before we get into what you can do to prepare for the inevitable, let’s clarify what ransomware actually is and how it works. Ransomware is malware that holds your data hostage and demands payment for its release. It typically infiltrates a system with a phishing email or website infection and exploits an existing endpoint vulnerability. Ransomware then establishes a foothold, expands to other endpoints, and moves to discover, collect, stage and encrypt target data. Once the damage is done, it covers its tracks and exfiltrates data for use or sale on the dark web. Ransomware is unique because once it is in your environment, there are very few remedies available — all recourse is costly and business interruption is inevitable.
- 5. What’s malware? The National Cyber Security Centre states: “Malicious software, also software or web content that can harm your organisation, such as the outbreak. The most well-known form of malware is viruses, which are infect legitimate software.” •Never pay the ransom demands. There is no guarantee that data or access to systems will be restored and victims who paid may be re- targeted. •Always install the latest software and app updates on all devices, and use ant-virus software wherever possible. •Beware of the warning signs of phishing and whaling. Do not open attachments or click on links within any unsolicited emails you receive. •Back up your data and keep it stored in a secure network.
- 7. Why is ransomware spreading? Ransomware attacks and their variants are rapidly evolving to counter preventive technologies for several reasons: •Easy availability of malware kits that can be used to create new malware samples on demand •Use of known good generic interpreters to create cross-platform ransomware (for example, Ransom32 uses Node.js with a JavaScript payload) •Use of new techniques, such as encrypting the complete disk instead of selected files Today’s thieves don’t even have to be tech savvy. Ransomware marketplaces have sprouted up online, offering malware strains for any would-be cybercrook and generating extra profit for the malware authors, who often ask for a cut in the ransom proceeds.
- 10. How to Protect Your Business From Ransomware The good news is that many flaws exploited in ransomware attacks are known vulnerabilities. This means that organizations have the opportunity to prevent most ransomware from being successful before an attack is ever launched. It is important to prepare your defense so you can respond quickly and effectively during an attack, and remediate and restore where necessary after an attack. The first and most cost-effective remedy is prevention.
- 11. THANK YOU Like the Video and Subscribe the Channel
