Email providers, encryption, anonymity and operational security guide
•
1 j'aime•161 vues
This document provides steps and recommendations for conducting anonymous and secure online activities. It recommends using Tor-based email providers and PGP encryption. It also discusses using VPNs and virtual private servers (VPS) accessed via Remote Desktop Protocol (RDP). It recommends anonymizing payments with cryptocurrencies like Bitcoin and Monero. It provides links for encrypting devices and data, spoofing hostnames, and using the Tails operating system to conduct activities privately from a USB drive.
Signaler
Partager
Signaler
Partager
Télécharger pour lire hors ligne
Recommandé
Contenu connexe
Similaire à Email providers, encryption, anonymity and operational security guide
Similaire à Email providers, encryption, anonymity and operational security guide (20)
Ransomware - what is it, how to protect against it

Ransomware - what is it, how to protect against it
The JavaScript toolset for development on Ethereum

The JavaScript toolset for development on Ethereum
Javascript toolset for Ethereum Smart Contract development

Javascript toolset for Ethereum Smart Contract development
DEF CON 27 - DANIEL ROMERO and MARIO RIVAS - why you should fear your mundane...

DEF CON 27 - DANIEL ROMERO and MARIO RIVAS - why you should fear your mundane...
BSides London 2015 - Proprietary network protocols - risky business on the wire.

BSides London 2015 - Proprietary network protocols - risky business on the wire.
Securing Network Access with Open Source solutions

Securing Network Access with Open Source solutions
Dernier
Driving Behavioral Change for Information Management through Data-Driven Gree...

Driving Behavioral Change for Information Management through Data-Driven Gree...Enterprise Knowledge
Dernier (20)
08448380779 Call Girls In Diplomatic Enclave Women Seeking Men

08448380779 Call Girls In Diplomatic Enclave Women Seeking Men
Advantages of Hiring UIUX Design Service Providers for Your Business

Advantages of Hiring UIUX Design Service Providers for Your Business
Raspberry Pi 5: Challenges and Solutions in Bringing up an OpenGL/Vulkan Driv...

Raspberry Pi 5: Challenges and Solutions in Bringing up an OpenGL/Vulkan Driv...
The Role of Taxonomy and Ontology in Semantic Layers - Heather Hedden.pdf

The Role of Taxonomy and Ontology in Semantic Layers - Heather Hedden.pdf
Apidays Singapore 2024 - Building Digital Trust in a Digital Economy by Veron...

Apidays Singapore 2024 - Building Digital Trust in a Digital Economy by Veron...
Automating Google Workspace (GWS) & more with Apps Script

Automating Google Workspace (GWS) & more with Apps Script
Mastering MySQL Database Architecture: Deep Dive into MySQL Shell and MySQL R...

Mastering MySQL Database Architecture: Deep Dive into MySQL Shell and MySQL R...
Breaking the Kubernetes Kill Chain: Host Path Mount

Breaking the Kubernetes Kill Chain: Host Path Mount
Strategies for Unlocking Knowledge Management in Microsoft 365 in the Copilot...

Strategies for Unlocking Knowledge Management in Microsoft 365 in the Copilot...
Driving Behavioral Change for Information Management through Data-Driven Gree...

Driving Behavioral Change for Information Management through Data-Driven Gree...
Exploring the Future Potential of AI-Enabled Smartphone Processors

Exploring the Future Potential of AI-Enabled Smartphone Processors
Understanding Discord NSFW Servers A Guide for Responsible Users.pdf

Understanding Discord NSFW Servers A Guide for Responsible Users.pdf
[2024]Digital Global Overview Report 2024 Meltwater.pdf![[2024]Digital Global Overview Report 2024 Meltwater.pdf](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[2024]Digital Global Overview Report 2024 Meltwater.pdf](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
[2024]Digital Global Overview Report 2024 Meltwater.pdf
How to Troubleshoot Apps for the Modern Connected Worker

How to Troubleshoot Apps for the Modern Connected Worker
Email providers, encryption, anonymity and operational security guide
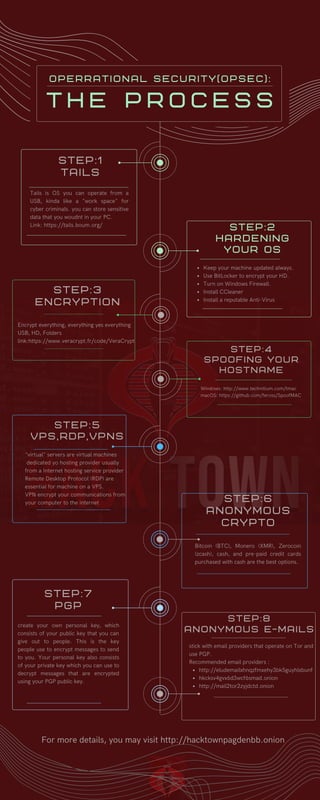
- 1. Recommended email providers : http://eludemailxhnqzfmxehy3bk5guyhlxbunf hkcksv4gvx6d3wcf6smad.onion http://mail2tor2zyjdctd.onion stick with email providers that operate on Tor and use PGP. S T E P : 7 P G P "virtual" servers are virtual machines dedicated yo hosting provider usually from a Internet hosting service provider . Remote Desktop Protocol (RDP) are essential for machine on a VPS. VPN encrypt your communications from your computer to the internet S T E P : 5 V P S , R D P , V P N S Bitcoin (BTC), Monero (XMR), Zerocoin (zcash), cash, and pre-paid credit cards purchased with cash are the best options. S T E P : 6 A N O N Y M O U S C R Y P T O For more details, you may visit http://hacktownpagdenbb.onion Keep your machine updated always. Use BitLocker to encrypt your HD. Turn on Windows Firewall. Install CCleaner Install a reputable Anti-Virus S T E P : 2 H A R D E N I N G Y O U R O S S T E P : 8 A N O N Y M O U S E - M A I L S create your own personal key, which consists of your public key that you can give out to people. This is the key people use to encrypt messages to send to you. Your personal key also consists of your private key which you can use to decrypt messages that are encrypted using your PGP public key. Tails is OS you can operate from a USB, kinda like a "work space" for cyber criminals. you can store sensitive data that you woudnt in your PC. Link: https://tails.boum.org/ S T E P : 1 T A I L S S T E P : 4 S P O O F I N G Y O U R H O S T N A M E Windows: http://www.technitium.com/tmac macOS: https://github.com/feross/SpoofMAC S T E P : 3 E N C R Y P T I O N Encrypt everything, everything yes everything USB, HD, Folders link:https://www.veracrypt.fr/code/VeraCrypt T h e P r o c e s s o p e r r a t i o n a l s e c u r i t y ( o p s e c ) :