XOR Cipher
•Télécharger en tant que PPTX, PDF•
1 j'aime•985 vues
XOR Cipher
Signaler
Partager
Signaler
Partager
Recommandé
Contenu connexe
Tendances
Tendances (20)
The Factoring Dead: Preparing for the Cryptopocalypse

The Factoring Dead: Preparing for the Cryptopocalypse
Plus de Garmian
Plus de Garmian (20)
Artificial intelligence and environmental development.pptx

Artificial intelligence and environmental development.pptx
Artificial intelligence and environmental development.pptx

Artificial intelligence and environmental development.pptx
Dernier
Dernier (20)
The Role of Taxonomy and Ontology in Semantic Layers - Heather Hedden.pdf

The Role of Taxonomy and Ontology in Semantic Layers - Heather Hedden.pdf
Automating Google Workspace (GWS) & more with Apps Script

Automating Google Workspace (GWS) & more with Apps Script
How to Troubleshoot Apps for the Modern Connected Worker

How to Troubleshoot Apps for the Modern Connected Worker
Strategize a Smooth Tenant-to-tenant Migration and Copilot Takeoff

Strategize a Smooth Tenant-to-tenant Migration and Copilot Takeoff
From Event to Action: Accelerate Your Decision Making with Real-Time Automation

From Event to Action: Accelerate Your Decision Making with Real-Time Automation
How to Troubleshoot Apps for the Modern Connected Worker

How to Troubleshoot Apps for the Modern Connected Worker
Axa Assurance Maroc - Insurer Innovation Award 2024

Axa Assurance Maroc - Insurer Innovation Award 2024
Bajaj Allianz Life Insurance Company - Insurer Innovation Award 2024

Bajaj Allianz Life Insurance Company - Insurer Innovation Award 2024
Scaling API-first – The story of a global engineering organization

Scaling API-first – The story of a global engineering organization
Handwritten Text Recognition for manuscripts and early printed texts

Handwritten Text Recognition for manuscripts and early printed texts
IAC 2024 - IA Fast Track to Search Focused AI Solutions

IAC 2024 - IA Fast Track to Search Focused AI Solutions
[2024]Digital Global Overview Report 2024 Meltwater.pdf![[2024]Digital Global Overview Report 2024 Meltwater.pdf](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[2024]Digital Global Overview Report 2024 Meltwater.pdf](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
[2024]Digital Global Overview Report 2024 Meltwater.pdf
Strategies for Unlocking Knowledge Management in Microsoft 365 in the Copilot...

Strategies for Unlocking Knowledge Management in Microsoft 365 in the Copilot...
XOR Cipher
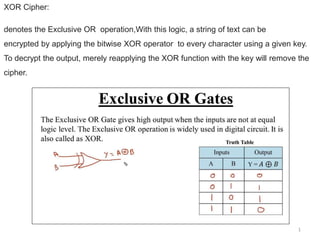
- 1. 1 XOR Cipher: denotes the Exclusive OR operation,With this logic, a string of text can be encrypted by applying the bitwise XOR operator to every character using a given key. To decrypt the output, merely reapplying the XOR function with the key will remove the cipher.
- 2. 2
- 3. 3
- 4. 4 Binary 128 64 32 16 8 4 2 1 Plain text = Z 0 1 0 1 1 0 1 0 Key = 3 0 0 0 0 0 0 1 1 Cipher text= Y 0 1 0 1 1 0 0 1
- 5. 5 Example 2:
