Unit III IPV6 UDP
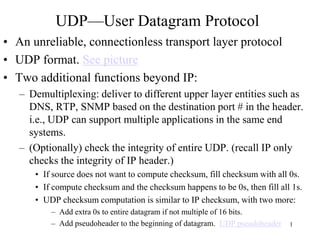
- 1. UDP—User Datagram Protocol • An unreliable, connectionless transport layer protocol • UDP format. See picture • Two additional functions beyond IP: – Demultiplexing: deliver to different upper layer entities such as DNS, RTP, SNMP based on the destination port # in the header. i.e., UDP can support multiple applications in the same end systems. – (Optionally) check the integrity of entire UDP. (recall IP only checks the integrity of IP header.) • If source does not want to compute checksum, fill checksum with all 0s. • If compute checksum and the checksum happens to be 0s, then fill all 1s. • UDP checksum computation is similar to IP checksum, with two more: – Add extra 0s to entire datagram if not multiple of 16 bits. – Add pseudoheader to the beginning of datagram. UDP pseudoheader 1
- 2. UDP datagram 0 16 31 Source Port Destination Port UDP Length UDP Checksum Data Back to UDP—User Datagram Protocol 2 Figure 8.16
- 3. Back to UDP—User Datagram Protocol UDP pseudoheader 0 8 16 31 Source IP Address Destination IP Address 00000000 Protocol = 17 UDP Length 1.Pseudoheader is to ensure that the datagram has indeed reached the correct destination host and port. 2. The padding of 0s and pseudoheader is only for the computation of checksum and not be transmitted. 3 Figure 8.17
- 4. TCP—transmission control protocol • TCP functionality – Provides connection-oriented, reliable, in-sequence, byte-stream service – Provides a logical full-duplex (two way) connection – Provides flow-control by advertised window. – Provides congestion control by congestion window. – Support multiple applications in the same end systems. • TCP establishes connection by setting up variables that are used in two peer TCP entities. Most important variables are initial sequence numbers. • TCP uses Selective Repeat ARQ. • TCP terminates each direction of connection independently, allowing data to continue flowing in one direction after closing the other direction. • TCP does not keep messages boundaries and treats data as byte stream. e.g, when source sends out two chunks of data with length 400 and 600 bytes, the receiver may receive data in chunks of 300, 400, and 300 bytes, or 100 and 900 bytes. 4
- 5. TCP operations 1. TCP delivers byte stream.See picture 2. TCP deals with old packets from old connections by several methods. See picture 3. TCP uses sliding-window to implement reliable transfer of byte stream. See picture 4. TCP uses advertised window for flow control. 5. Adaptive timer: 1. tout = tRTT+4dRTT , 2. tRTT(new) = tRTT(old) +(1- ) n , dRTT(new)= dRTT(old) + (1- )( n-tRTT) 3. Where n is the time from transmitting a segment until receiving its ACK. , are in 0 to 1 with being 7/8 and being ¼ typically. tRTT is mean round- trip-time, dRTT is average of deviation. 6. TCP uses congestion window for congestion control. See picture 5
- 6. TCP byte stream Application Application byte stream byte stream segments Transmitter Receiver Send buffer Receive buffer ACKs 6 Figure 8.18
- 7. An old segment could not be distinguished from current ones Host A Host B Delayed segment with Seq_no = n+2 will be accepted Question: How does TCP prevent old packets of old connections? –Using long (32 bit) sequence number –Random initial sequence number -- set a timer at the end of a connection to clear all lost packets from this connection. As a result, that an old packet from an old connection conflicts with packets in current connection is very low!! 7 Back to TCP operations Figure 8.23
- 8. TCP uses Selective-Repeat ARQ Transmitter Receiver Receive Window Send Window Slast+WS- Rlast Rlast+WR+1 ... ... 1 ... … … … Octets Rnext Rnew transmitted Slast Srecent Slast+WA-1 and ACKed Advertised window Rlast highest-numbered octet not yet read Slast oldest unacknowledged octet by the application Srecent highest-numbered transmitted octet Rnext next expected octet Slast+WA-1 highest-numbered octet that Rnew highest numbered octet received can be transmitted correctly Slast+WS-1 highest-numbered octet that Rlast+WR-1 highest-numbered octet that can be accepted from the application can be accommodated in receive buffer Note: 1. Rnew highest bytes received correctly, which are out-of sequence bytes. 2. Advertised window WA: Srecent – Slast WA =WR – ( Rnew – Rlast) 8 Back to TCP operations Figure 8.19
- 9. Dynamics of TCP congestion window Congestion Congestion occurs 20 avoidance 15 Congestion window Threshold 10 Slow start 5 0 Round-trip times Back to TCP operations 9 Figure 7.63
- 10. TCP protocol • TCP segment See Segment format – TCP pseudoheader. See pseudoheader • TCP connection establishment. See establishment – Client-server application See socket • TCP Data transfer – Sliding window with window sliding on byte basis – Flow control and piggybacking See flow control • TCP connection termination – After receiving ACK for previous data, but no more data to send, the TCP will terminate the connection in its direction by issuing an FIN segment. Graceful termination • TCP state transition diagram 10
- 11. Back to TCP protocol TCP segment format 0 4 10 16 24 31 Source Port Destination Port Sequence Number Acknowledgement Number Header U A P R S F Length Reserved R C S S Y I (Advertised) Window Size GKH T N N Checksum Urgent Pointer Options Padding Data 1.SYN: request to set a connection. 2. RST: tell the receiver to abort the connection. 3. FIN: tell receiver this is the final segment, no more data, i.e, close the connection in this direction 4. ACK: tell the receiver (or sender) that the value is the field of acknowledgment number is valid 5. PSH: tell the receiving TCP entity to pass the data to the application immediately. 6. URG: tell the receiver that the Urgent Pointer is valid. Urgent Pointer: this pointer added to the sequence number points to the last byte of the 11 ―Urgent Data‖, (the data that needs immediately delivery). Figure 8.20
- 12. Back to TCP protocol TCP pseudoheader 0 8 16 31 Source IP Address Destination IP Address 00000000 Protocol = 6 TCP Segment Length The padding of 0s and pseudoheader is only used in computation of checksum but not be transmitted, as in UDP checksum. 12 Figure 8.21
- 13. Back to TCP protocol Host A Host B 1. Random initial SN 2. Initial SNs in two directions are different 3. Initial SNs for two connections are different. 4. It should be clear here that what setting up connection means: both A and B know that they will exchange data, and go into ready state to send and receive data. Most important is that they agree upon the initial SNs. Three-way handshake to set up connection 13 Figure 8.22
- 14. Back to TCP protocol Host A (Client) Host B (Server) socket bind socket listen connect (blocks) accept (blocks) connect returns write read (blocks) accept returns read (blocks) read returns write read (blocks) read returns 14 Figure 8.24
- 15. TCP window flow control Host A Host B t0 t1 t2 t3 t4 15 Back to TCP protocol Figure 8.25
- 16. Back to TCP protocol TCP graceful termination Host A Host B Question: is termination easier than establishment? Or to say, is it possible that a connection is closed when both of two parties confirm with each other? No, Saying goodbye is hard to do. Famous blue-red armies problem. 16 Figure 8.27
- 17. Thick lines: normal client states Dashed lines: normal server states CLOSED passive open, applic. create TCB close LISTEN applic. close or timeout, SYN_RCVD receive SYN, SYN_SENT delete TCB send ACK applic. close, ESTABLISHED send FIN CLOSE_WAIT FIN_WAIT_1 CLOSING LAST_ACK TIME_WAIT 2MSL timeout FIN_WAIT_2 delete TCB 17 Back to TCP protocol Figure 8.28
- 18. Sequence number wraparound and timestamps • Original TCP specification for MSL (Maximum Segment Lifetime) is 2 minutes. • How long will it take to wrap around 32 bit sequence number when 232=4,294,967,296 bytes have been sent (maximum window size=231) – T-1 line, (232 8)/(1.544 106) = 6 hours – T-3 line, (232 8)/(45 106) = 12 minutes – OC-48 line, (232 8)/(2.4 109) = 14 seconds !!! • When sequence number wrap around, the wraparounded sequence number will confuse with previous sequence number. • Solution: optional timestamp field (32 bits) in TCP header, thus, 232 232=264 is big enough right now. 18
- 19. Internet routing protocols • Autonomous system (AS) – A set of routers or networks technically administrated by a single organization. – No restriction that an AS must run a single routing protocol – Only requirement is that from outside, an AS presents a consistent picture of which ASs are reachable through it. • Three types of ASs: – Stub AS: has only a single connection to outside. – Multihomed AS: has multiple connections to outside, but refuses to carry out transit traffic – Transit AS: multiple connections to outside and carry transit traffic. • ASs need to be assigned globally unique AS number (ASN) 19
- 20. Classification of Internet routing protocols • IGP (Interior Gateway Protocol): – For routers to communicate within an AS and relies on IP address to construct paths. – Provides a map of a county dealing with how to reach each building. – RIP (Routing Information Protocol): distance vector – OSPF (Open Shortest Path First): link state • EGP (Exterior Gateway Protocol): – For routers to communicate among different ASs and relies on AS numbers to construct AS paths. – Provides a map of a country, connecting each county. – BGP (Border Gateway Protocol): (distance) path vector 20
- 21. RIP—Routing Information Protocol • Distance vector • On top of UDP with port #520 • Metric is number of hops – Maximum number of hops is 15, 16 stands for infinity – Using split-horizon with poisoned reverse. – May speed up convergence by triggered updates. • Routers exchange distance vector every 30 seconds – If a router does not receive distance vector from its neighbor X within 180 seconds, the link to X is considered broken and the router sets the cost to X is 16 (infinity). • RIP-2 contains more information: subnet mask, next hop, routing domain, authentication, CIDR 21
- 22. RIP message format 0 8 16 31 Command Version Zero Address Family Identifier Zero IP Address Zero Zero Metric ... 1. Command: 1: request other routers to send routing information 2: a response containing its routing information 2. Version: 1 or 2 3. Up to 25 routing information message 3.1 Family identifier: only 2 for IP address 3.2 IP address: can be a host address or a network address 3.3 Metric: 1—15. 16 indicates infinity Problems of RIP: not scalable, slow convergence, counting-to-infinity 22 therefore replaced By OSPF in 1979. Figure 8.32
- 23. Internet multicast • A packet is to be sent to multiple hosts with the same multicast address • Class D multicast addresses: e.g., – 224.0.0.1 all systems on a LAN – 224.0.0.2 all routers on a LAN – 224.0.0.5 all OSPF routers on a LAN – 224.0.0.6 all designated OSPF routers on a LAN • It is not efficient to implement multicast by unicast, i.e., the source sends a separate copy for every destination. • Reverse-path broadcasting / multicasting, each packet is transmitted once per link • IGMP (Internet Group Management Protocol): allow a user to join a multicast group and let routers collect multicast group membership information. 23
- 24. Multicasting G1 G1 1 3 7 2 2 4 2 4 2 3 1 1 5 5 2 3 3 G1 2 4 1 8 S 1 1 3 4 G1 5 4 2 2 4 1 2 1 3 6 3 1 3 4 G2 3 G3 G3 • Source S sends packets to multicast group G1 24
- 25. Multicast Routing • Multicast routing useful when a source wants to transmit its packets to several destinations simultaneously • Relying on unicast routing by transmitting each copy of packet separately works, but can be very inefficient if number of destinations is large • Typical applications is multi-party conferencing over the Internet • Example: Multicast Backbone (MBONE) uses reverse path multicasting 25
- 26. Reverse-Path Broadcasting (RPB) • Fact: Set of shortest paths to the source node S forms a tree that spans the network – Approach: Follow paths in reverse direction • Assume each router knows current shortest path to S – Upon receipt of a multicast packet, router records the packet’s source address and the port it arrives on – If shortest path to source is through same port (―parent port‖), router forwards the packet to all other ports – Else, drops the packet • Loops are suppressed; each packet forwarded by a router exactly once • Implicitly assume shortest path to source S is same as shortest path from source – If paths asymmetric, need to use link state info to compute shortest paths from S 26
- 27. Example: Shortest Paths from S G1 G1 1 3 7 2 2 4 2 4 2 3 1 1 5 2 5 3 3 G1 2 4 1 8 S 1 4 G1 1 3 5 4 2 2 4 1 2 1 3 6 3 1 3 4 G2 3 G3 G3 • Spanning tree of shortest paths to node S and parent ports are shown in blue 27
- 28. Example: S sends a packet G1 G1 1 3 7 2 2 4 2 4 2 3 1 1 5 2 5 3 3 G1 2 4 1 8 S 1 4 G1 1 3 5 4 2 2 4 1 2 1 3 6 3 1 3 4 G2 3 G3 G3 • S sends a packet to node 1 28 • Node 1 forwards to all ports, except parent port
- 29. Example: Hop 1 nodes broadcast G1 G1 1 3 7 2 2 4 2 4 2 3 1 1 5 5 3 2 3 G1 2 4 1 8 1 S 1 3 4 G1 5 4 2 2 4 1 2 1 3 6 3 1 3 4 G2 3 G3 G3 • Nodes 2, 3, 4, and 5 broadcast, except on parent ports 29 • All nodes, not only G1, receive packets
- 30. Example: Broadcast continues G1 G1 1 3 7 2 2 4 2 4 2 3 1 1 5 2 5 3 3 G1 2 4 1 8 S 1 4 G1 1 3 5 4 2 2 4 1 2 1 3 6 3 1 3 4 G2 3 G3 G3 • Truncated RPB (TRPB): Leaf routers do not broadcast if none of its attached hosts belong to packet’s multicast group 30
- 31. Internet Group Management Protocol (IGMP) • Internet Group Management Protocol: – Host can join a multicast group by sending an IGMP message to its router • Each multicast router periodically sends an IGMP query message to check whether there are hosts belonging to multicast groups – Hosts respond with list of multicast groups they belong to – Hosts randomize response time; cancel response if other hosts reply with same membership • Routers determine which multicast groups are associated with a certain port • Routers only forward packets on ports that have hosts belonging to the multicast group 31
- 32. Multicast programming • 2.1 Multicast addresses. – 224.0.0.0---247.255.255.255 • 2.2 Levels of conformance. – 0: no, 1: sending, 2: receiving • 2.3 Sending Multicast Datagrams. – Open UDP socket, and send to multicast address – TTL • 0 Restricted to the same host. • 1 Restricted to the same subnet. • <32 Restricted to the same site, organization or department. • <64 Restricted to the same region. • <128 Restricted to the same continent. • <255 Unrestricted in scope. Global. • 2.4 Receiving Multicast Datagrams. – Joining multicast group – Drop multicast group • Mapping of IP Multicast Addresses to Ethernet/FDDI addresses. 32
- 33. Multicast functions • int getsockopt(int s, int level, int optname, void* optval, int* optlen); • int setsockopt(int s, int level, int optname, const void* optval, int optlen); • setsockopt() getsockopt() • IP_MULTICAST_LOOP yes yes • IP_MULTICAST_TTL yes yes • IP_MULTICAST_IF yes yes • IP_ADD_MEMBERSHIP yes no • IP_DROP_MEMBERSHIP yes no • http://www.ibiblio.org/pub/Linux/docs/HOWTO/o ther-formats/html_single/Multicast- HOWTO.html#ss2.1 33
- 34. IPv6 (IPng): IPv4 is very successful but the victim of its own success. • Longer address field: – 128 bits can support up to 3.4 x 1038 hosts • Simplified header format: – Simpler format to speed up processing of each header – All fields are of fixed size – IPv4 vs IPv6 fields: • Same: Version • Dropped: Header length, ID/flags/frag offset, header checksum • Replaced: – Datagram length by Payload length – Protocol type by Next header – TTL by Hop limit – TOS by traffic class • New: Flow label 34
- 35. Other IPv6 Features • Flexible support for options: more efficient and flexible options encoded in optional extension headers • Flow label capability: ―flow label‖ to identify a packet flow that requires a certain QoS • Security: built-in authentication and confidentiality • Large packets: supports payloads that are longer than 64 K bytes, called jumbo payloads. • Fragmentation at source only: source should check the minimum MTU along the path • No checksum field: removed to reduce packet 35 processing time in a router
- 36. IPv6 Header Format 0 4 12 16 24 31 Version Traffic Class Flow Label Payload Length Next Header Hop Limit Source Address Destination Address • Version field same size, same location • Traffic class to support differentiated services • Flow: sequence of packets from particular source to particular 36 destination for which source requires special handling
- 37. IPv6 Header Format 0 4 12 16 24 31 Version Traffic Class Flow Label Payload Length Next Header Hop Limit Source Address Destination Address • Payload length: length of data excluding header, up to 65535 B • Next header: type of extension header that follows basic header • Hop limit: # hops packet can travel before being dropped by a router 37
- 38. IPv6 Addressing • Address Categories – Unicast: single network interface – Multicast: group of network interfaces, typically at different locations. Packet sent to all. – Anycast: group of network interfaces. Packet sent to only one interface in group, e.g. nearest. • Hexadecimal notation – Groups of 16 bits represented by 4 hex digits – Separated by colons • 4BF5:AA12:0216:FEBC:BA5F:039A:BE9A:2176 – Shortened forms: • 4BF5:0000:0000:0000:BA5F:039A:000A:2176 • To 4BF5:0:0:0:BA5F:39A:A:2176 • To 4BF5::BA5F:39A:A:2176 – Mixed notation: 38 • ::FFFF:128.155.12.198
- 39. Example 39
- 40. Address Types based on Prefixes Binary prefix Types Percentage of address space 0000 0000 Reserved 0.39 0000 0001 Unassigned 0.39 0000 001 ISO network addresses 0.78 0000 010 IPX network addresses 0.78 0000 011 Unassigned 0.78 0000 1 Unassigned 3.12 0001 Unassigned 6.25 001 Unassigned 12.5 010 Provider-based unicast addresses 12.5 011 Unassigned 12.5 100 Geographic-based unicast addresses 12.5 101 Unassigned 12.5 110 Unassigned 12.5 1110 Unassigned 6.25 1111 0 Unassigned 3.12 1111 10 Unassigned 1.56 1111 110 Unassigned 0.78 1111 1110 0 Unassigned 0.2 1111 1110 10 Link local use addresses 0.098 40 1111 1110 11 Site local use addresses 0.098
- 41. Special Purpose Addresses n bits m bits o bits p bits (125-m-n-o-p) bits 010 Registry ID Provider ID Subscriber ID Subnet ID Interface ID • Provider-based Addresses: 010 prefix – Assigned by providers to their customers – Hierarchical structure promotes aggregation • Registry ID: ARIN, RIPE, APNIC • ISP • Subscriber ID: subnet ID & interface ID • Local Addresses: do not connect to global Internet – Link-local: for single link – Site-local: for single site – Designed to facilitate transition to connection to Internet 41
- 42. Special Purpose Addresses • Unspecified Address: 0::0 – Used by source station to learn own address • Loopback Address: ::1 • IPv4-compatible addresses: 96 0’s + IPv4 – For tunneling by IPv6 routers connected to IPv4 networks – ::135.150.10.247 • IP-mapped addresses: 80 0’s + 16 1’s + IPv4 – Denote IPv4 hosts & routers that do not support IPv6 42
- 43. Migration from IPv4 to IPv6 • Gradual transition from IPv4 to IPv6 • Dual IP stacks: routers run IPv4 & IPv6 – Type field used to direct packet to IP version • IPv6 islands can tunnel across IPv4 networks – Encapsulate user packet insider IPv4 packet – Tunnel endpoint at source host, intermediate router, or destination host – Tunneling can be recursive 43
- 44. Migration from IPv4 to IPv6 Tunnel head-end Tunnel tail-end Destination Source Tunnel (a) IPv6 header IPv6 network IPv4 header IPv6 network IPv4 network Source Destination Link (b) IPv6 network IPv6 network 44
- 45. DHCP (Dynamic Host Configuration Protocol) • A host broadcasts a DHCP discovery message in its physical network for an IP address. • Server(s) reply with DHCP offer message • The host selects one IP address and broadcasts a DHCP request message including the IP address • The selected server allocates the IP address and sends back a DHCP ACK message with a lease time T, two thresholds T1 (=0.5T), T2(=0.875T) – when T1 expires, the host asks the server for extension. – If T2 expire, the host broadcasts DHCP request to any server on the network – If T expires, the host relinquishes the IP address and reapply from scratch. 45
- 46. Mobile IP • Mobile host, home agent, foreign agent • If mobile host is currently at the same network with HA (home agent), the packet to the mobile host will be broadcast to it. • If mobile host moves to another network, the mobile host will register itself with FA (foreign agent) and gets a new care-of IP address. Then packet is sent to HA, which will forward to the FA and FA continues to forward to destination. 46
- 47. Deliver packets to mobile host through home agent and foreign agent Foreign network Home Foreign network agent Mobile host 2 Home agent Internet 3 1 Correspondent host 47 Figure 8.29