NIST 800-53 Controls
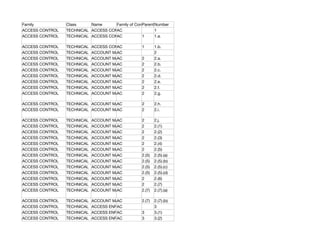
- 1. Family Class Name Family of Control Parent Number ACCESS CONTROL TECHNICAL ACCESS CONTROL POLICY AND 1 AC PROCEDURES ACCESS CONTROL TECHNICAL ACCESS CONTROL POLICY AND 1.a. AC 1 PROCEDURES ACCESS CONTROL TECHNICAL ACCESS CONTROL POLICY AND 1.b. AC 1 PROCEDURES ACCESS CONTROL TECHNICAL ACCOUNT MANAGEMENT AC 2 ACCESS CONTROL TECHNICAL ACCOUNT MANAGEMENT 2 AC 2.a. ACCESS CONTROL TECHNICAL ACCOUNT MANAGEMENT 2 AC 2.b. ACCESS CONTROL TECHNICAL ACCOUNT MANAGEMENT 2 AC 2.c. ACCESS CONTROL TECHNICAL ACCOUNT MANAGEMENT 2 AC 2.d. ACCESS CONTROL TECHNICAL ACCOUNT MANAGEMENT 2 AC 2.e. ACCESS CONTROL TECHNICAL ACCOUNT MANAGEMENT 2 AC 2.f. ACCESS CONTROL TECHNICAL ACCOUNT MANAGEMENT 2 AC 2.g. ACCESS CONTROL TECHNICAL ACCOUNT MANAGEMENT 2 AC 2.h. ACCESS CONTROL TECHNICAL ACCOUNT MANAGEMENT 2 AC 2.i. ACCESS CONTROL TECHNICAL ACCOUNT MANAGEMENT AC 2 2.j. ACCESS CONTROL TECHNICAL ACCOUNT MANAGEMENT AC 2 2.(1) ACCESS CONTROL TECHNICAL ACCOUNT MANAGEMENT AC 2 2.(2) ACCESS CONTROL TECHNICAL ACCOUNT MANAGEMENT AC 2 2.(3) ACCESS CONTROL TECHNICAL ACCOUNT MANAGEMENT AC 2 2.(4) ACCESS CONTROL TECHNICAL ACCOUNT MANAGEMENT AC 2 2.(5) ACCESS CONTROL TECHNICAL ACCOUNT MANAGEMENT AC 2.(5) 2.(5).(a) ACCESS CONTROL TECHNICAL ACCOUNT MANAGEMENT AC 2.(5) 2.(5).(b) ACCESS CONTROL TECHNICAL ACCOUNT MANAGEMENT AC 2.(5) 2.(5).(c) ACCESS CONTROL TECHNICAL ACCOUNT MANAGEMENT AC 2.(5) 2.(5).(d) ACCESS CONTROL TECHNICAL ACCOUNT MANAGEMENT AC 2 2.(6) ACCESS CONTROL TECHNICAL ACCOUNT MANAGEMENT AC 2 2.(7) ACCESS CONTROL TECHNICAL ACCOUNT MANAGEMENT AC 2.(7) 2.(7).(a) ACCESS CONTROL TECHNICAL ACCOUNT MANAGEMENT 2.(7) AC 2.(7).(b) ACCESS CONTROL TECHNICAL ACCESS ENFORCEMENT AC 3 ACCESS CONTROL TECHNICAL ACCESS ENFORCEMENT 3 AC 3.(1) ACCESS CONTROL TECHNICAL ACCESS ENFORCEMENT 3 AC 3.(2)
- 2. ACCESS CONTROL TECHNICAL ACCESS ENFORCEMENT 3 AC 3.(3) ACCESS CONTROL TECHNICAL ACCESS ENFORCEMENT 3.(3) AC 3.(3).(a) ACCESS CONTROL TECHNICAL ACCESS ENFORCEMENT 3.(3) AC 3.(3).(b) ACCESS CONTROL TECHNICAL ACCESS ENFORCEMENT 3 AC 3.(4) ACCESS CONTROL TECHNICAL ACCESS ENFORCEMENT 3.(4) 3.(4).(a) AC ACCESS CONTROL TECHNICAL ACCESS ENFORCEMENT 3.(4) 3.(4).(b) AC ACCESS CONTROL TECHNICAL ACCESS ENFORCEMENT 3.(4) 3.(4).(c) AC ACCESS CONTROL TECHNICAL ACCESS ENFORCEMENT 3 AC 3.(5) ACCESS CONTROL TECHNICAL ACCESS ENFORCEMENT 3 AC 3.(6) ACCESS CONTROL TECHNICAL INFORMATION FLOW ENFORCEMENT AC 4 ACCESS CONTROL TECHNICAL INFORMATION FLOW ENFORCEMENT AC 4 4.(1) ACCESS CONTROL TECHNICAL INFORMATION FLOW ENFORCEMENT AC 4 4.(2) ACCESS CONTROL TECHNICAL INFORMATION FLOW ENFORCEMENT AC 4 4.(3) ACCESS CONTROL TECHNICAL INFORMATION FLOW ENFORCEMENT AC 4 4.(4)
- 3. ACCESS CONTROL TECHNICAL INFORMATION FLOW ENFORCEMENT AC 4 4.(5) ACCESS CONTROL TECHNICAL INFORMATION FLOW ENFORCEMENT AC 4 4.(6) ACCESS CONTROL TECHNICAL INFORMATION FLOW ENFORCEMENT AC 4 4.(7) ACCESS CONTROL TECHNICAL INFORMATION FLOW ENFORCEMENT AC 4 4.(8) ACCESS CONTROL TECHNICAL INFORMATION FLOW ENFORCEMENT AC 4 4.(9) ACCESS CONTROL TECHNICAL INFORMATION FLOW ENFORCEMENT AC 4 4.(10) ACCESS CONTROL TECHNICAL INFORMATION FLOW ENFORCEMENT AC 4 4.(11) ACCESS CONTROL TECHNICAL INFORMATION FLOW ENFORCEMENT AC 4 4.(12) ACCESS CONTROL TECHNICAL INFORMATION FLOW ENFORCEMENT AC 4 4.(13) ACCESS CONTROL TECHNICAL INFORMATION FLOW ENFORCEMENT AC 4 4.(14) ACCESS CONTROL TECHNICAL INFORMATION FLOW ENFORCEMENT AC 4 4.(15) ACCESS CONTROL TECHNICAL INFORMATION FLOW ENFORCEMENT AC 4 4.(16) ACCESS CONTROL TECHNICAL INFORMATION FLOW ENFORCEMENT AC 4 4.(17) ACCESS CONTROL TECHNICAL INFORMATION FLOW ENFORCEMENT AC 4.(17) 4.(17).(a) ACCESS CONTROL TECHNICAL INFORMATION FLOW ENFORCEMENT AC 4.(17) 4.(17).(b) ACCESS CONTROL TECHNICAL INFORMATION FLOW ENFORCEMENT AC 4.(17) 4.(17).(c) ACCESS CONTROL TECHNICAL SEPARATION AC DUTIES OF 5 ACCESS CONTROL TECHNICAL SEPARATION AC DUTIES 5 OF 5.a. ACCESS CONTROL TECHNICAL SEPARATION AC DUTIES 5 OF 5.b. ACCESS CONTROL TECHNICAL SEPARATION AC DUTIES 5 OF 5.c. ACCESS CONTROL TECHNICAL LEAST PRIVILEGE AC 6 ACCESS CONTROL TECHNICAL LEAST PRIVILEGE AC 6 6.(1) ACCESS CONTROL TECHNICAL LEAST PRIVILEGE AC 6 6.(2) ACCESS CONTROL TECHNICAL LEAST PRIVILEGE AC 6 6.(3) ACCESS CONTROL TECHNICAL LEAST PRIVILEGE AC 6 6.(4) ACCESS CONTROL TECHNICAL LEAST PRIVILEGE AC 6 6.(5) ACCESS CONTROL TECHNICAL LEAST PRIVILEGE AC 6 6.(6)
- 4. ACCESS CONTROL TECHNICAL UNSUCCESSFUL LOGIN ATTEMPTS AC 7 ACCESS CONTROL TECHNICAL UNSUCCESSFUL LOGIN ATTEMPTS AC 7 7.a. ACCESS CONTROL TECHNICAL UNSUCCESSFUL LOGIN ATTEMPTS AC 7 7.b. ACCESS CONTROL TECHNICAL UNSUCCESSFUL LOGIN ATTEMPTS AC 7 7.(1) ACCESS CONTROL TECHNICAL UNSUCCESSFUL LOGIN ATTEMPTS AC 7 7.(2) ACCESS CONTROL TECHNICAL SYSTEM USEAC NOTIFICATION 8 ACCESS CONTROL TECHNICAL SYSTEM USEAC NOTIFICATION 8 8.a. ACCESS CONTROL TECHNICAL SYSTEM USEAC NOTIFICATION 8 8.b. ACCESS CONTROL TECHNICAL SYSTEM USEAC NOTIFICATION 8 8.c. ACCESS CONTROL TECHNICAL PREVIOUS LOGON (ACCESS) NOTIFICATION AC 9 ACCESS CONTROL TECHNICAL PREVIOUS LOGON (ACCESS) NOTIFICATION AC 9 9.(1) ACCESS CONTROL TECHNICAL PREVIOUS LOGON (ACCESS) NOTIFICATION AC 9 9.(2) ACCESS CONTROL TECHNICAL PREVIOUS LOGON (ACCESS) NOTIFICATION AC 9 9.(3) ACCESS CONTROL TECHNICAL CONCURRENT SESSION CONTROL AC 10 ACCESS CONTROL TECHNICAL SESSION LOCK AC 11 ACCESS CONTROL TECHNICAL SESSION LOCK AC 11 11.a. ACCESS CONTROL TECHNICAL SESSION LOCK AC 11 11.b. ACCESS CONTROL TECHNICAL SESSION LOCK AC 11 11.(1) ACCESS CONTROL TECHNICAL SESSION TERMINATION AC 12 ACCESS CONTROL TECHNICAL SUPERVISION AND REVIEW — ACCESS CONTROL AC 13 ACCESS CONTROL TECHNICAL PERMITTED ACTIONS WITHOUT IDENTIFICATION OR AUTHENTICATION AC 14 ACCESS CONTROL TECHNICAL PERMITTED ACTIONS WITHOUT IDENTIFICATION OR AUTHENTICATION AC 14 14.a. ACCESS CONTROL TECHNICAL PERMITTED ACTIONS WITHOUT IDENTIFICATION OR AUTHENTICATION AC 14 14.b. ACCESS CONTROL TECHNICAL PERMITTED ACTIONS WITHOUT IDENTIFICATION OR AUTHENTICATION AC 14 14.(1)
- 5. ACCESS CONTROL TECHNICAL AUTOMATED AC MARKING 15 ACCESS CONTROL TECHNICAL SECURITY ATTRIBUTES AC 16 ACCESS CONTROL TECHNICAL SECURITY ATTRIBUTES AC 16 16.(1) ACCESS CONTROL TECHNICAL SECURITY ATTRIBUTES AC 16 16.(2) ACCESS CONTROL TECHNICAL SECURITY ATTRIBUTES AC 16 16.(3) ACCESS CONTROL TECHNICAL SECURITY ATTRIBUTES AC 16 16.(4) ACCESS CONTROL TECHNICAL SECURITY ATTRIBUTES AC 16 16.(5) ACCESS CONTROL TECHNICAL REMOTE ACCESS AC 17 ACCESS CONTROL TECHNICAL REMOTE ACCESS AC 17 17.a. ACCESS CONTROL TECHNICAL REMOTE ACCESS AC 17 17.b. ACCESS CONTROL TECHNICAL REMOTE ACCESS AC 17 17.c. ACCESS CONTROL TECHNICAL REMOTE ACCESS AC 17 17.d. ACCESS CONTROL TECHNICAL REMOTE ACCESS AC 17 17.e. ACCESS CONTROL TECHNICAL REMOTE ACCESS AC 17 17.(1) ACCESS CONTROL TECHNICAL REMOTE ACCESS AC 17 17.(2) ACCESS CONTROL TECHNICAL REMOTE ACCESS AC 17 17.(3) ACCESS CONTROL TECHNICAL REMOTE ACCESS AC 17 17.(4) ACCESS CONTROL TECHNICAL REMOTE ACCESS AC 17 17.(5) ACCESS CONTROL TECHNICAL REMOTE ACCESS AC 17 17.(6) ACCESS CONTROL TECHNICAL REMOTE ACCESS AC 17 17.(7) ACCESS CONTROL TECHNICAL REMOTE ACCESS AC 17 17.(8) ACCESS CONTROL TECHNICAL WIRELESS ACCESS AC 18 ACCESS CONTROL TECHNICAL WIRELESS ACCESS AC 18 18.a. ACCESS CONTROL TECHNICAL WIRELESS ACCESS AC 18 18.b. ACCESS CONTROL TECHNICAL WIRELESS ACCESS AC 18 18.c. ACCESS CONTROL TECHNICAL WIRELESS ACCESS AC 18 18.d. ACCESS CONTROL TECHNICAL WIRELESS ACCESS AC 18 18.(1) ACCESS CONTROL TECHNICAL WIRELESS ACCESS AC 18 18.(2)
- 6. ACCESS CONTROL TECHNICAL WIRELESS ACCESS AC 18 18.(3) ACCESS CONTROL TECHNICAL WIRELESS ACCESS AC 18 18.(4) ACCESS CONTROL TECHNICAL WIRELESS ACCESS AC 18 18.(5) ACCESS CONTROL TECHNICAL ACCESS CONTROL FOR MOBILE 19 AC DEVICES ACCESS CONTROL TECHNICAL ACCESS CONTROL FOR MOBILE 19.a. AC 19 DEVICES ACCESS CONTROL TECHNICAL ACCESS CONTROL FOR MOBILE 19.b. AC 19 DEVICES
- 7. ACCESS CONTROL TECHNICAL ACCESS CONTROL FOR MOBILE 19.c. AC 19 DEVICES ACCESS CONTROL TECHNICAL ACCESS CONTROL FOR MOBILE 19.d. AC 19 DEVICES ACCESS CONTROL TECHNICAL ACCESS CONTROL FOR MOBILE 19.e. AC 19 DEVICES
- 8. ACCESS CONTROL TECHNICAL ACCESS CONTROL FOR MOBILE 19.g. AC 19 DEVICES ACCESS CONTROL TECHNICAL ACCESS CONTROL FOR MOBILE 19.(1) AC 19 DEVICES ACCESS CONTROL TECHNICAL ACCESS CONTROL FOR MOBILE 19.(2) AC 19 DEVICES ACCESS CONTROL TECHNICAL ACCESS CONTROL FOR MOBILE 19.(3) AC 19 DEVICES ACCESS CONTROL TECHNICAL ACCESS CONTROL FOR MOBILE 19.(4).(a) AC 19.(4) DEVICES ACCESS CONTROL TECHNICAL ACCESS CONTROL FOR MOBILE 19.(4).(b) AC 19.(4) DEVICES ACCESS CONTROL TECHNICAL USE OF EXTERNAL INFORMATION SYSTEMS AC 20
- 9. ACCESS CONTROL TECHNICAL USE OF EXTERNAL INFORMATION SYSTEMS AC 20 20.a. ACCESS CONTROL TECHNICAL USE OF EXTERNAL INFORMATION SYSTEMS AC 20 20.b. ACCESS CONTROL TECHNICAL USE OF EXTERNAL INFORMATION SYSTEMS AC 20 20.(1) ACCESS CONTROL TECHNICAL USE OF EXTERNAL INFORMATION SYSTEMS AC 20.(1) 20.(1).(a) ACCESS CONTROL TECHNICAL USE OF EXTERNAL INFORMATION SYSTEMS AC 20.(1) 20.(1).(b) ACCESS CONTROL TECHNICAL USE OF EXTERNAL INFORMATION SYSTEMS AC 20 20.(2) ACCESS CONTROL TECHNICAL USER-BASEDACCOLLABORATION AND INFORMATION SHARING 21 ACCESS CONTROL TECHNICAL USER-BASEDACCOLLABORATION AND INFORMATION SHARING 21 21.a. ACCESS CONTROL TECHNICAL USER-BASEDAC COLLABORATION AND INFORMATION SHARING 21 21.b. ACCESS CONTROL TECHNICAL USER-BASEDAC COLLABORATION AND INFORMATION SHARING 21 21.(1) ACCESS CONTROL TECHNICAL PUBLICLY ACCESSIBLE CONTENT AC 22 ACCESS CONTROL TECHNICAL PUBLICLY ACCESSIBLE CONTENT AC 22 22.a. ACCESS CONTROL TECHNICAL PUBLICLY ACCESSIBLE CONTENT AC 22 22.b. ACCESS CONTROL TECHNICAL PUBLICLY ACCESSIBLE CONTENT AC 22 22.c.
- 10. ACCESS CONTROL TECHNICAL PUBLICLY ACCESSIBLE CONTENT AC 22 22.d. ACCESS CONTROL TECHNICAL PUBLICLY ACCESSIBLE CONTENT AC 22 22.e. AWARENESS AND TRAINING OPERATIONALECURITY AWARENESS AND TRAINING POLICY AND PROCEDURES S AT 1 AWARENESS AND TRAINING OPERATIONALECURITY AWARENESS AND TRAINING POLICY AND PROCEDURES S AT 1 1.a. AWARENESS AND TRAINING OPERATIONALECURITY AWARENESS AND TRAINING POLICY AND PROCEDURES S AT 1 1.b. AWARENESS AND TRAINING OPERATIONALECURITY AWARENESS S AT 2 AWARENESS AND TRAINING OPERATIONALECURITY AWARENESS S AT 2 2.(1) AWARENESS AND TRAINING OPERATIONALECURITY TRAINING S AT 3 AWARENESS AND TRAINING OPERATIONALECURITY TRAINING S AT 3 3.(1) AWARENESS AND TRAINING OPERATIONALECURITY TRAINING S AT 3 3.(2) AWARENESS AND TRAINING OPERATIONALECURITY TRAINING RECORDS 4 S AT AWARENESS AND TRAINING OPERATIONALECURITY TRAINING RECORDS 4.a. S AT 4 AWARENESS AND TRAINING OPERATIONALECURITY TRAINING RECORDS 4.b. S AT 4 AWARENESS AND TRAINING OPERATIONAL ONTACTS WITH SECURITY GROUPS AND ASSOCIATIONS C AT 5 AUDIT AND ACCOUNTABILITY TECHNICAL AUDIT AND ACCOUNTABILITY POLICY AND PROCEDURES AU 1 AUDIT AND ACCOUNTABILITY TECHNICAL AUDIT AND ACCOUNTABILITY POLICY AND PROCEDURES AU 1 1.a. AUDIT AND ACCOUNTABILITY TECHNICAL AUDIT AND ACCOUNTABILITY POLICY AND PROCEDURES AU 1 1.b. AUDIT AND ACCOUNTABILITY TECHNICAL AUDITABLE EVENTS AU 2 AUDIT AND ACCOUNTABILITY TECHNICAL AUDITABLE EVENTS AU 2 2.a. AUDIT AND ACCOUNTABILITY TECHNICAL AUDITABLE EVENTS AU 2 2.b. AUDIT AND ACCOUNTABILITY TECHNICAL AUDITABLE EVENTS AU 2 2.c. AUDIT AND ACCOUNTABILITY TECHNICAL AUDITABLE EVENTS AU 2 2.d.
- 11. AUDIT AND ACCOUNTABILITY TECHNICAL AUDITABLE EVENTS AU 2 2.(1) AUDIT AND ACCOUNTABILITY TECHNICAL AUDITABLE EVENTS AU 2 2.(2) AUDIT AND ACCOUNTABILITY TECHNICAL AUDITABLE EVENTS AU 2 2.(3) AUDIT AND ACCOUNTABILITY TECHNICAL AUDITABLE EVENTS AU 2 2.(4) AUDIT AND ACCOUNTABILITY TECHNICAL CONTENT OFAU AUDIT RECORDS 3 AUDIT AND ACCOUNTABILITY TECHNICAL CONTENT OFAU AUDIT RECORDS 3.(1) 3 AUDIT AND ACCOUNTABILITY TECHNICAL CONTENT OFAU AUDIT RECORDS 3.(2) 3 AUDIT AND ACCOUNTABILITY TECHNICAL AUDIT STORAGE CAPACITY AU 4 AUDIT AND ACCOUNTABILITY TECHNICAL RESPONSE TO AUDIT PROCESSING FAILURES AU 5 AUDIT AND ACCOUNTABILITY TECHNICAL RESPONSE TO AUDIT PROCESSING FAILURES AU 5 5.a. AUDIT AND ACCOUNTABILITY TECHNICAL RESPONSE TO AUDIT PROCESSING FAILURES AU 5 5.b. AUDIT AND ACCOUNTABILITY TECHNICAL RESPONSE TO AUDIT PROCESSING FAILURES AU 5 5.(1) AUDIT AND ACCOUNTABILITY TECHNICAL RESPONSE TO AUDIT PROCESSING FAILURES AU 5 5.(2) AUDIT AND ACCOUNTABILITY TECHNICAL RESPONSE TO AUDIT PROCESSING FAILURES AU 5 5.(3) AUDIT AND ACCOUNTABILITY TECHNICAL RESPONSE TO AUDIT PROCESSING FAILURES AU 5 5.(4) AUDIT AND ACCOUNTABILITY TECHNICAL AUDIT REVIEW, ANALYSIS, AND REPORTING AU 6 AUDIT AND ACCOUNTABILITY TECHNICAL AUDIT REVIEW, ANALYSIS,6 AU AND REPORTING 6.a. AUDIT AND ACCOUNTABILITY TECHNICAL AUDIT REVIEW, ANALYSIS,6 AU AND REPORTING 6.b. AUDIT AND ACCOUNTABILITY TECHNICAL AUDIT REVIEW, ANALYSIS,6 AU AND REPORTING 6.(1) AUDIT AND ACCOUNTABILITY TECHNICAL AUDIT REVIEW, ANALYSIS,6 AU AND REPORTING 6.(2) AUDIT AND ACCOUNTABILITY TECHNICAL AUDIT REVIEW, ANALYSIS,6 AU AND REPORTING 6.(3) AUDIT AND ACCOUNTABILITY TECHNICAL AUDIT REVIEW, ANALYSIS,6 AU AND REPORTING 6.(4) AUDIT AND ACCOUNTABILITY TECHNICAL AUDIT REVIEW, ANALYSIS,6 AU AND REPORTING 6.(5) AUDIT AND ACCOUNTABILITY TECHNICAL AUDIT REVIEW, ANALYSIS,6 AU AND REPORTING 6.(6) AUDIT AND ACCOUNTABILITY TECHNICAL AUDIT REVIEW, ANALYSIS,6 AU AND REPORTING 6.(7)
- 12. AUDIT AND ACCOUNTABILITY TECHNICAL AUDIT REVIEW, ANALYSIS,6 AU AND REPORTING 6.(8) AUDIT AND ACCOUNTABILITY TECHNICAL AUDIT REVIEW, ANALYSIS,6 AU AND REPORTING 6.(9) AUDIT AND ACCOUNTABILITY TECHNICAL AUDIT REDUCTION AND REPORT7 AU GENERATION AUDIT AND ACCOUNTABILITY TECHNICAL AUDIT REDUCTION AND REPORT7.(1) AU 7 GENERATION AUDIT AND ACCOUNTABILITY TECHNICAL TIME STAMPSAU 8 AUDIT AND ACCOUNTABILITY TECHNICAL TIME STAMPSAU 8 8.(1) AUDIT AND ACCOUNTABILITY TECHNICAL PROTECTIONAU AUDIT INFORMATION OF 9 AUDIT AND ACCOUNTABILITY TECHNICAL PROTECTIONAU AUDIT INFORMATION OF 9 9.(1) AUDIT AND ACCOUNTABILITY TECHNICAL PROTECTIONAU AUDIT INFORMATION OF 9 9.(2) AUDIT AND ACCOUNTABILITY TECHNICAL PROTECTIONAU AUDIT INFORMATION OF 9 9.(3) AUDIT AND ACCOUNTABILITY TECHNICAL PROTECTIONAU AUDIT INFORMATION OF 9 9.(4) AUDIT AND ACCOUNTABILITY TECHNICAL PROTECTIONAU AUDIT INFORMATION OF 9.(4) 9.(4).(a) AUDIT AND ACCOUNTABILITY TECHNICAL PROTECTIONAU AUDIT INFORMATION OF 9.(4) 9.(4).(b) AUDIT AND ACCOUNTABILITY TECHNICAL NON-REPUDIATION AU 10 AUDIT AND ACCOUNTABILITY TECHNICAL NON-REPUDIATION AU 10 10.(1) AUDIT AND ACCOUNTABILITY TECHNICAL NON-REPUDIATION AU 10 10.(2) AUDIT AND ACCOUNTABILITY TECHNICAL NON-REPUDIATION AU 10 10.(3) AUDIT AND ACCOUNTABILITY TECHNICAL NON-REPUDIATION AU 10 10.(4) AUDIT AND ACCOUNTABILITY TECHNICAL NON-REPUDIATION AU 10 10.(5) AUDIT AND ACCOUNTABILITY TECHNICAL AUDIT RECORD RETENTION AU 11 AUDIT AND ACCOUNTABILITY TECHNICAL AUDIT GENERATION AU 12 AUDIT AND ACCOUNTABILITY TECHNICAL AUDIT GENERATION AU 12 12.a. AUDIT AND ACCOUNTABILITY TECHNICAL AUDIT GENERATION AU 12 12.b. AUDIT AND ACCOUNTABILITY TECHNICAL AUDIT GENERATION AU 12 12.c. AUDIT AND ACCOUNTABILITY TECHNICAL AUDIT GENERATION AU 12 12.(1) AUDIT AND ACCOUNTABILITY TECHNICAL AUDIT GENERATION AU 12 12.(2) AUDIT AND ACCOUNTABILITY TECHNICAL MONITORINGAU INFORMATION DISCLOSURE FOR 13 AUDIT AND ACCOUNTABILITY TECHNICAL SESSION AUDIT AU 14 AUDIT AND ACCOUNTABILITY TECHNICAL SESSION AUDIT AU 14 14.a. AUDIT AND ACCOUNTABILITY TECHNICAL SESSION AUDIT AU 14 14.b.
- 13. AUDIT AND ACCOUNTABILITY TECHNICAL SESSION AUDIT AU 14 14.(1) SECURITY ASSESSMENT AND AUTHORIZATIONASSESSMENT AND AUTHORIZATION POLICIES AND PROCEDURES MANAGEMENTSECURITY CA 1 SECURITY ASSESSMENT AND AUTHORIZATIONASSESSMENT AND AUTHORIZATION POLICIES AND PROCEDURES MANAGEMENTSECURITY CA 1 1.a. SECURITY ASSESSMENT AND AUTHORIZATIONASSESSMENT AND AUTHORIZATION POLICIES AND PROCEDURES MANAGEMENTSECURITY CA 1 1.b. SECURITY ASSESSMENT AND AUTHORIZATIONASSESSMENTS MANAGEMENTSECURITY CA 2 SECURITY ASSESSMENT AND AUTHORIZATIONASSESSMENTS 2 MANAGEMENTSECURITY CA 2.a. SECURITY ASSESSMENT AND AUTHORIZATIONASSESSMENTS 2 MANAGEMENTSECURITY CA 2.b.
- 14. SECURITY ASSESSMENT AND AUTHORIZATIONASSESSMENTS 2 MANAGEMENTSECURITY CA 2.c. SECURITY ASSESSMENT AND AUTHORIZATIONASSESSMENTS 2 MANAGEMENTSECURITY CA 2.d. SECURITY ASSESSMENT AND AUTHORIZATIONASSESSMENTS 2 MANAGEMENTSECURITY CA 2.(1) SECURITY ASSESSMENT AND AUTHORIZATIONASSESSMENTS 2 MANAGEMENTSECURITY CA 2.(2) SECURITY ASSESSMENT AND AUTHORIZATION CA MANAGEMENTINFORMATION SYSTEM CONNECTIONS 3 SECURITY ASSESSMENT AND AUTHORIZATION CA MANAGEMENTINFORMATION SYSTEM CONNECTIONS 3 3.a. SECURITY ASSESSMENT AND AUTHORIZATION CA MANAGEMENTINFORMATION SYSTEM CONNECTIONS 3 3.b. SECURITY ASSESSMENT AND AUTHORIZATION CA MANAGEMENTINFORMATION SYSTEM CONNECTIONS 3 3.c. SECURITY ASSESSMENT AND AUTHORIZATION CA MANAGEMENTINFORMATION SYSTEM CONNECTIONS 3 3.(1) SECURITY ASSESSMENT AND AUTHORIZATION CA MANAGEMENTINFORMATION SYSTEM CONNECTIONS 3 3.(2) SECURITY ASSESSMENT AND AUTHORIZATIONCERTIFICATION MANAGEMENTSECURITY CA 4 SECURITY ASSESSMENT AND AUTHORIZATION CA AND MILESTONES MANAGEMENTPLAN OF ACTION 5 SECURITY ASSESSMENT AND AUTHORIZATION CA AND MILESTONES MANAGEMENTPLAN OF ACTION 5 5.a. SECURITY ASSESSMENT AND AUTHORIZATION CA AND MILESTONES MANAGEMENTPLAN OF ACTION 5 5.b.
- 15. SECURITY ASSESSMENT AND AUTHORIZATION CA AND MILESTONES MANAGEMENTPLAN OF ACTION 5 5.(1) SECURITY ASSESSMENT AND AUTHORIZATIONAUTHORIZATION MANAGEMENTSECURITY CA 6 SECURITY ASSESSMENT AND AUTHORIZATIONAUTHORIZATION MANAGEMENTSECURITY CA 6 6.a. SECURITY ASSESSMENT AND AUTHORIZATIONAUTHORIZATION MANAGEMENTSECURITY CA 6 6.b. SECURITY ASSESSMENT AND AUTHORIZATIONAUTHORIZATION MANAGEMENTSECURITY CA 6 6.c. SECURITY ASSESSMENT AND AUTHORIZATION CA MANAGEMENTCONTINUOUS MONITORING 7 SECURITY ASSESSMENT AND AUTHORIZATION CA MANAGEMENTCONTINUOUS MONITORING7 7.a. SECURITY ASSESSMENT AND AUTHORIZATION CA MANAGEMENTCONTINUOUS MONITORING7 7.b. SECURITY ASSESSMENT AND AUTHORIZATION CA MANAGEMENTCONTINUOUS MONITORING7 7.c. SECURITY ASSESSMENT AND AUTHORIZATION CA MANAGEMENTCONTINUOUS MONITORING7 7.d. SECURITY ASSESSMENT AND AUTHORIZATION CA MANAGEMENTCONTINUOUS MONITORING7 7.(1) SECURITY ASSESSMENT AND AUTHORIZATION CA MANAGEMENTCONTINUOUS MONITORING7 7.(2) CONFIGURATION MANAGEMENT OPERATIONAL ONFIGURATION MANAGEMENT 1 C CM POLICY AND PROCEDURES CONFIGURATION MANAGEMENT OPERATIONAL ONFIGURATION MANAGEMENT 1.a. C CM 1 POLICY AND PROCEDURES CONFIGURATION MANAGEMENT OPERATIONAL ONFIGURATION MANAGEMENT 1.b. C CM 1 POLICY AND PROCEDURES CONFIGURATION MANAGEMENT OPERATIONAL ASELINE CONFIGURATION B CM 2 CONFIGURATION MANAGEMENT OPERATIONAL ASELINE CONFIGURATION B CM 2 2.(1) CONFIGURATION MANAGEMENT OPERATIONAL ASELINE CONFIGURATION B CM 2.(1) 2.(1).(a) CONFIGURATION MANAGEMENT OPERATIONAL ASELINE CONFIGURATION B CM 2.(1) 2.(1).(b) CONFIGURATION MANAGEMENT OPERATIONAL ASELINE CONFIGURATION B CM 2.(1) 2.(1).(c) CONFIGURATION MANAGEMENT OPERATIONAL ASELINE CONFIGURATION B CM 2 2.(2) CONFIGURATION MANAGEMENT OPERATIONAL ASELINE CONFIGURATION B CM 2 2.(3) CONFIGURATION MANAGEMENT OPERATIONAL ASELINE CONFIGURATION B CM 2 2.(4) CONFIGURATION MANAGEMENT OPERATIONAL ASELINE CONFIGURATION B CM 2.(4) 2.(4).(a) CONFIGURATION MANAGEMENT OPERATIONAL ASELINE CONFIGURATION B CM 2.(4) 2.(4).(b) CONFIGURATION MANAGEMENT OPERATIONAL ASELINE CONFIGURATION B CM 2 2.(5) CONFIGURATION MANAGEMENT OPERATIONAL ASELINE CONFIGURATION B CM 2.(5) 2.(5).(a) CONFIGURATION MANAGEMENT OPERATIONAL ASELINE CONFIGURATION B CM 2.(5) 2.(5).(b) CONFIGURATION MANAGEMENT OPERATIONAL ASELINE CONFIGURATION B CM 2 2.(6) CONFIGURATION MANAGEMENT OPERATIONAL ONFIGURATION CHANGE CONTROL C CM 3 CONFIGURATION MANAGEMENT OPERATIONAL ONFIGURATION CHANGE3CONTROL C CM 3.a.
- 16. CONFIGURATION MANAGEMENT OPERATIONAL ONFIGURATION CHANGE3CONTROL C CM 3.b. CONFIGURATION MANAGEMENT OPERATIONAL ONFIGURATION CHANGE3CONTROL C CM 3.c. CONFIGURATION MANAGEMENT OPERATIONAL ONFIGURATION CHANGE3CONTROL C CM 3.d. CONFIGURATION MANAGEMENT OPERATIONAL ONFIGURATION CHANGE3CONTROL C CM 3.e. CONFIGURATION MANAGEMENT OPERATIONAL ONFIGURATION CHANGE3CONTROL C CM 3.f. CONFIGURATION MANAGEMENT OPERATIONAL ONFIGURATION CHANGE3CONTROL C CM 3.(1) CONFIGURATION MANAGEMENT OPERATIONAL ONFIGURATION CHANGE3.(1) 3.(1).(a) C CM CONTROL CONFIGURATION MANAGEMENT OPERATIONAL ONFIGURATION CHANGE3.(1) 3.(1).(b) C CM CONTROL CONFIGURATION MANAGEMENT OPERATIONAL ONFIGURATION CHANGE3.(1) 3.(1).(c) C CM CONTROL CONFIGURATION MANAGEMENT OPERATIONAL ONFIGURATION CHANGE3.(1) 3.(1).(d) C CM CONTROL CONFIGURATION MANAGEMENT OPERATIONAL ONFIGURATION CHANGE3.(1) 3.(1).(e) C CM CONTROL CONFIGURATION MANAGEMENT OPERATIONAL ONFIGURATION CHANGE3CONTROL C CM 3.(2) CONFIGURATION MANAGEMENT OPERATIONAL ONFIGURATION CHANGE3CONTROL C CM 3.(3) CONFIGURATION MANAGEMENT OPERATIONAL ONFIGURATION CHANGE3CONTROL C CM 3.(4) CONFIGURATION MANAGEMENT OPERATIONALECURITY IMPACT ANALYSIS S CM 4 CONFIGURATION MANAGEMENT OPERATIONALECURITY IMPACT ANALYSIS S CM 4 4.(1) CONFIGURATION MANAGEMENT OPERATIONALECURITY IMPACT ANALYSIS S CM 4 4.(2) CONFIGURATION MANAGEMENT OPERATIONALCCESS RESTRICTIONS FOR CHANGE A CM 5 CONFIGURATION MANAGEMENT OPERATIONALCCESS RESTRICTIONS FOR CHANGE A CM 5 5.(1) CONFIGURATION MANAGEMENT OPERATIONALCCESS RESTRICTIONS FOR CHANGE A CM 5 5.(2) CONFIGURATION MANAGEMENT OPERATIONALCCESS RESTRICTIONS FOR CHANGE A CM 5 5.(3) CONFIGURATION MANAGEMENT OPERATIONALCCESS RESTRICTIONS FOR CHANGE A CM 5 5.(4) CONFIGURATION MANAGEMENT OPERATIONALCCESS RESTRICTIONS FOR CHANGE A CM 5 5.(5) CONFIGURATION MANAGEMENT OPERATIONALCCESS RESTRICTIONS FOR CHANGE A CM 5.(5) 5.(5).(a) CONFIGURATION MANAGEMENT OPERATIONALCCESS RESTRICTIONS FOR CHANGE A CM 5.(5) 5.(5).(b) CONFIGURATION MANAGEMENT OPERATIONALCCESS RESTRICTIONS FOR CHANGE A CM 5 5.(6) CONFIGURATION MANAGEMENT OPERATIONALCCESS RESTRICTIONS FOR CHANGE A CM 5 5.(7)
- 17. CONFIGURATION MANAGEMENT OPERATIONAL ONFIGURATION SETTINGS C CM 6 CONFIGURATION MANAGEMENT OPERATIONAL ONFIGURATION SETTINGS C CM 6 6.a. CONFIGURATION MANAGEMENT OPERATIONAL ONFIGURATION SETTINGS C CM 6 6.b. CONFIGURATION MANAGEMENT OPERATIONAL ONFIGURATION SETTINGS C CM 6 6.c. CONFIGURATION MANAGEMENT OPERATIONAL ONFIGURATION SETTINGS C CM 6 6.d. CONFIGURATION MANAGEMENT OPERATIONAL ONFIGURATION SETTINGS C CM 6 6.(1) CONFIGURATION MANAGEMENT OPERATIONAL ONFIGURATION SETTINGS C CM 6 6.(2) CONFIGURATION MANAGEMENT OPERATIONAL ONFIGURATION SETTINGS C CM 6 6.(3) CONFIGURATION MANAGEMENT OPERATIONAL ONFIGURATION SETTINGS C CM 6 6.(4) CONFIGURATION MANAGEMENT OPERATIONALEAST FUNCTIONALITY L CM 7 CONFIGURATION MANAGEMENT OPERATIONALEAST FUNCTIONALITY L CM 7 7.(1) CONFIGURATION MANAGEMENT OPERATIONALEAST FUNCTIONALITY L CM 7 7.(2) CONFIGURATION MANAGEMENT OPERATIONALEAST FUNCTIONALITY 7 L CM 7.(3) CONFIGURATION MANAGEMENT OPERATIONAL INFORMATION SYSTEM COMPONENT INVENTORY CM 8 CONFIGURATION MANAGEMENT OPERATIONAL INFORMATION SYSTEM COMPONENT INVENTORY CM 8 8.a. CONFIGURATION MANAGEMENT OPERATIONAL INFORMATION SYSTEM COMPONENT INVENTORY CM 8 8.b. CONFIGURATION MANAGEMENT OPERATIONAL INFORMATION SYSTEM COMPONENT INVENTORY CM 8 8.c. CONFIGURATION MANAGEMENT OPERATIONAL INFORMATION SYSTEM COMPONENT INVENTORY CM 8 8.d. CONFIGURATION MANAGEMENT OPERATIONAL INFORMATION SYSTEM COMPONENT INVENTORY CM 8 8.e. CONFIGURATION MANAGEMENT OPERATIONAL INFORMATION SYSTEM COMPONENT INVENTORY CM 8 8.(1) CONFIGURATION MANAGEMENT OPERATIONAL INFORMATION SYSTEM COMPONENT INVENTORY CM 8 8.(2) CONFIGURATION MANAGEMENT OPERATIONAL INFORMATION SYSTEM COMPONENT INVENTORY CM 8 8.(3) CONFIGURATION MANAGEMENT OPERATIONAL INFORMATION SYSTEM COMPONENT INVENTORY CM 8.(3) 8.(3).(a) CONFIGURATION MANAGEMENT OPERATIONAL INFORMATION SYSTEM COMPONENT INVENTORY CM 8.(3) 8.(3).(b) CONFIGURATION MANAGEMENT OPERATIONAL INFORMATION SYSTEM COMPONENT INVENTORY CM 8 8.(4) CONFIGURATION MANAGEMENT OPERATIONAL INFORMATION SYSTEM COMPONENT INVENTORY CM 8 8.(5)
- 18. CONFIGURATION MANAGEMENT OPERATIONAL INFORMATION SYSTEM COMPONENT INVENTORY CM 8 8.(6) CONFIGURATION MANAGEMENT OPERATIONAL ONFIGURATION MANAGEMENT 9 C CM PLAN CONFIGURATION MANAGEMENT OPERATIONAL ONFIGURATION MANAGEMENT 9.a. C CM 9 PLAN CONFIGURATION MANAGEMENT OPERATIONAL ONFIGURATION MANAGEMENT 9.b. C CM 9 PLAN CONFIGURATION MANAGEMENT OPERATIONAL ONFIGURATION MANAGEMENT 9.c. C CM 9 PLAN CONFIGURATION MANAGEMENT OPERATIONAL ONFIGURATION MANAGEMENT 9.(1) C CM 9 PLAN CONTINGENCY PLANNING OPERATIONAL ONTINGENCY PLANNING POLICY AND PROCEDURES C CP 1 CONTINGENCY PLANNING OPERATIONAL ONTINGENCY PLANNING1 C CP POLICY AND PROCEDURES 1.a. CONTINGENCY PLANNING OPERATIONAL ONTINGENCY PLANNING1 C CP POLICY AND PROCEDURES 1.b. CONTINGENCY PLANNING OPERATIONAL ONTINGENCY PLAN C CP 2 2.a. CONTINGENCY PLANNING OPERATIONAL ONTINGENCY PLAN C CP 2 2.b. CONTINGENCY PLANNING OPERATIONAL ONTINGENCY PLAN C CP 2 2.c. CONTINGENCY PLANNING OPERATIONAL ONTINGENCY PLAN C CP 2 2.d. CONTINGENCY PLANNING OPERATIONAL ONTINGENCY PLAN C CP 2 2.e. CONTINGENCY PLANNING OPERATIONAL ONTINGENCY PLAN C CP 2 2.f. CONTINGENCY PLANNING OPERATIONAL ONTINGENCY PLAN C CP 2 2.(1) CONTINGENCY PLANNING OPERATIONAL ONTINGENCY PLAN C CP 2 2.(2) CONTINGENCY PLANNING OPERATIONAL ONTINGENCY PLAN C CP 2 2.(3) CONTINGENCY PLANNING OPERATIONAL ONTINGENCY PLAN C CP 2 2.(4) CONTINGENCY PLANNING OPERATIONAL ONTINGENCY PLAN C CP 2 2.(5)
- 19. CONTINGENCY PLANNING OPERATIONAL ONTINGENCY PLAN C CP 2 2.(6) CONTINGENCY PLANNING OPERATIONAL ONTINGENCY TRAINING C CP 3 CONTINGENCY PLANNING OPERATIONAL ONTINGENCY TRAINING 3 C CP 3.(1) CONTINGENCY PLANNING OPERATIONAL ONTINGENCY TRAINING 3 C CP 3.(2) CONTINGENCY PLANNING OPERATIONAL ONTINGENCY PLAN TESTING AND EXERCISES C CP 4 CONTINGENCY PLANNING OPERATIONAL ONTINGENCY PLAN TESTING AND EXERCISES C CP 4 4.a. CONTINGENCY PLANNING OPERATIONAL ONTINGENCY PLAN TESTING AND EXERCISES C CP 4 4.b. CONTINGENCY PLANNING OPERATIONAL ONTINGENCY PLAN TESTING AND EXERCISES C CP 4 4.(1) CONTINGENCY PLANNING OPERATIONAL ONTINGENCY PLAN TESTING AND EXERCISES C CP 4 4.(2) CONTINGENCY PLANNING OPERATIONAL ONTINGENCY PLAN TESTING AND EXERCISES C CP 4 4.(3) CONTINGENCY PLANNING OPERATIONAL ONTINGENCY PLAN TESTING AND EXERCISES C CP 4 4.(4) CONTINGENCY PLANNING OPERATIONAL ONTINGENCY PLAN UPDATE 5 C CP CONTINGENCY PLANNING OPERATIONALLTERNATE STORAGE SITE A CP 6 CONTINGENCY PLANNING OPERATIONALLTERNATE STORAGE SITE A CP 6 6.(1) CONTINGENCY PLANNING OPERATIONALLTERNATE STORAGE SITE A CP 6 6.(2) CONTINGENCY PLANNING OPERATIONALLTERNATE STORAGE SITE A CP 6 6.(3) CONTINGENCY PLANNING OPERATIONALLTERNATE PROCESSING SITE 7 A CP CONTINGENCY PLANNING OPERATIONALLTERNATE PROCESSING 7 A CP SITE 7.a. CONTINGENCY PLANNING OPERATIONALLTERNATE PROCESSING 7 A CP SITE 7.b. CONTINGENCY PLANNING OPERATIONALLTERNATE PROCESSING 7 A CP SITE 7.(1) CONTINGENCY PLANNING OPERATIONALLTERNATE PROCESSING 7 A CP SITE 7.(2) CONTINGENCY PLANNING OPERATIONALLTERNATE PROCESSING 7 A CP SITE 7.(3) CONTINGENCY PLANNING OPERATIONALLTERNATE PROCESSING 7 A CP SITE 7.(4) CONTINGENCY PLANNING OPERATIONALLTERNATE PROCESSING 7 A CP SITE 7.(5) CONTINGENCY PLANNING OPERATIONALELECOMMUNICATIONS SERVICES T CP 8
- 20. CONTINGENCY PLANNING OPERATIONALELECOMMUNICATIONS SERVICES T CP 8 8.(1) CONTINGENCY PLANNING OPERATIONALELECOMMUNICATIONS SERVICES T CP 8.(1) 8.(1).(a) CONTINGENCY PLANNING OPERATIONALELECOMMUNICATIONS SERVICES T CP 8.(1) 8.(1).(b) CONTINGENCY PLANNING OPERATIONALELECOMMUNICATIONS SERVICES T CP 8 8.(2) CONTINGENCY PLANNING OPERATIONALELECOMMUNICATIONS SERVICES T CP 8 8.(3) CONTINGENCY PLANNING OPERATIONALELECOMMUNICATIONS SERVICES T CP 8 8.(4) CONTINGENCY PLANNING OPERATIONAL INFORMATION SYSTEM BACKUP 9 CP CONTINGENCY PLANNING OPERATIONAL INFORMATION SYSTEM BACKUP 9.a. CP 9 CONTINGENCY PLANNING OPERATIONAL INFORMATION SYSTEM BACKUP 9.b. CP 9 CONTINGENCY PLANNING OPERATIONAL INFORMATION SYSTEM BACKUP 9.c. CP 9 CONTINGENCY PLANNING OPERATIONAL INFORMATION SYSTEM BACKUP 9.d. CP 9 CONTINGENCY PLANNING OPERATIONAL INFORMATION SYSTEM BACKUP 9.(1) CP 9 CONTINGENCY PLANNING OPERATIONAL INFORMATION SYSTEM BACKUP 9.(2) CP 9 CONTINGENCY PLANNING OPERATIONAL INFORMATION SYSTEM BACKUP 9.(3) CP 9 CONTINGENCY PLANNING OPERATIONAL INFORMATION SYSTEM BACKUP 9.(4) CP 9 CONTINGENCY PLANNING OPERATIONAL INFORMATION SYSTEM BACKUP 9.(5) CP 9 CONTINGENCY PLANNING OPERATIONAL INFORMATION SYSTEM BACKUP 9.(6) CP 9 CONTINGENCY PLANNING OPERATIONAL INFORMATION SYSTEM RECOVERY AND RECONSTITUTION CP 10 CONTINGENCY PLANNING OPERATIONAL INFORMATION SYSTEM RECOVERY AND RECONSTITUTION CP 10 10.(1) CONTINGENCY PLANNING OPERATIONAL INFORMATION SYSTEM RECOVERY AND RECONSTITUTION CP 10 10.(2) CONTINGENCY PLANNING OPERATIONAL INFORMATION SYSTEM RECOVERY AND RECONSTITUTION CP 10 10.(3) CONTINGENCY PLANNING OPERATIONAL INFORMATION SYSTEM RECOVERY AND RECONSTITUTION CP 10 10.(4) CONTINGENCY PLANNINGOPERATIONALINFORMATION SYSTEM RECOVERY AND RECONSTITUTION CP 10 10.(5) CONTINGENCY PLANNINGOPERATIONALINFORMATION SYSTEM RECOVERY AND RECONSTITUTION CP 10 10.(6) IDENTIFICATION AND AUTHENTICATION TECHNICAL IDENTIFICATION AND AUTHENTICATION POLICY AND PROCEDURES IA 1
- 21. IDENTIFICATION AND AUTHENTICATION TECHNICAL IDENTIFICATION AND AUTHENTICATION POLICY AND PROCEDURES IA 1 1.a. IDENTIFICATION AND AUTHENTICATION TECHNICAL IDENTIFICATION AND AUTHENTICATION POLICY AND PROCEDURES IA 1 1.b. IDENTIFICATION AND AUTHENTICATION TECHNICAL IDENTIFICATION AND AUTHENTICATION (ORGANIZATIONAL USERS) IA 2 IDENTIFICATION AND AUTHENTICATION TECHNICAL IDENTIFICATION AND AUTHENTICATION (ORGANIZATIONAL USERS) IA 2 2.(1) IDENTIFICATION AND AUTHENTICATION TECHNICAL IDENTIFICATION AND AUTHENTICATION (ORGANIZATIONAL USERS) IA 2 2.(2) IDENTIFICATION AND AUTHENTICATION TECHNICAL IDENTIFICATION AND AUTHENTICATION (ORGANIZATIONAL USERS) IA 2 2.(3) IDENTIFICATION AND AUTHENTICATION TECHNICAL IDENTIFICATION AND AUTHENTICATION (ORGANIZATIONAL USERS) IA 2 2.(4) IDENTIFICATION AND AUTHENTICATION TECHNICAL IDENTIFICATION AND AUTHENTICATION (ORGANIZATIONAL USERS) IA 2 2.(5) IDENTIFICATION AND AUTHENTICATION TECHNICAL IDENTIFICATION AND AUTHENTICATION (ORGANIZATIONAL USERS) IA 2.(5) 2.(5).(a) IDENTIFICATION AND AUTHENTICATION TECHNICAL IDENTIFICATION AND AUTHENTICATION (ORGANIZATIONAL USERS) IA 2.(5) 2.(5).(b) IDENTIFICATION AND AUTHENTICATION TECHNICAL IDENTIFICATION AND AUTHENTICATION (ORGANIZATIONAL USERS) IA 2 2.(6) IDENTIFICATION AND AUTHENTICATION TECHNICAL IDENTIFICATION AND AUTHENTICATION (ORGANIZATIONAL USERS) IA 2 2.(7) IDENTIFICATION AND AUTHENTICATION TECHNICAL IDENTIFICATION AND AUTHENTICATION (ORGANIZATIONAL USERS) IA 2 2.(8) IDENTIFICATION AND AUTHENTICATION TECHNICAL IDENTIFICATION AND AUTHENTICATION (ORGANIZATIONAL USERS) IA 2 2.(9) IDENTIFICATION AND AUTHENTICATION TECHNICAL DEVICE IDENTIFICATION AND AUTHENTICATION IA 3 IDENTIFICATION AND AUTHENTICATION TECHNICAL DEVICE IDENTIFICATION AND AUTHENTICATION IA 3 3.(1) IDENTIFICATION AND AUTHENTICATION TECHNICAL DEVICE IDENTIFICATION AND AUTHENTICATION IA 3 3.(2) IDENTIFICATION AND AUTHENTICATION TECHNICAL DEVICE IDENTIFICATION AND AUTHENTICATION IA 3 3.(3) IDENTIFICATION AND AUTHENTICATION TECHNICAL IDENTIFIER MANAGEMENT IA 4 IDENTIFICATION AND AUTHENTICATION TECHNICAL IDENTIFIER MANAGEMENT4 IA 4.a. IDENTIFICATION AND AUTHENTICATION TECHNICAL IDENTIFIER MANAGEMENT4 IA 4.b. IDENTIFICATION AND AUTHENTICATION TECHNICAL IDENTIFIER MANAGEMENT4 IA 4.c.
- 22. IDENTIFICATION AND AUTHENTICATION TECHNICAL IDENTIFIER MANAGEMENT4 IA 4.d. IDENTIFICATION AND AUTHENTICATION TECHNICAL IDENTIFIER MANAGEMENT4 IA 4.e. IDENTIFICATION AND AUTHENTICATION TECHNICAL IDENTIFIER MANAGEMENT4 IA 4.(1) IDENTIFICATION AND AUTHENTICATION TECHNICAL IDENTIFIER MANAGEMENT4 IA 4.(2) IDENTIFICATION AND AUTHENTICATION TECHNICAL IDENTIFIER MANAGEMENT4 IA 4.(3) IDENTIFICATION AND AUTHENTICATION TECHNICAL IDENTIFIER MANAGEMENT4 IA 4.(4) IDENTIFICATION AND AUTHENTICATION TECHNICAL IDENTIFIER MANAGEMENT4 IA 4.(5) IDENTIFICATION AND AUTHENTICATION TECHNICAL AUTHENTICATOR MANAGEMENT5 IA IDENTIFICATION AND AUTHENTICATION TECHNICAL AUTHENTICATOR MANAGEMENT5.a. IA 5 IDENTIFICATION AND AUTHENTICATION TECHNICAL AUTHENTICATOR MANAGEMENT5.b. IA 5 IDENTIFICATION AND AUTHENTICATION TECHNICAL AUTHENTICATOR MANAGEMENT5.c. IA 5 IDENTIFICATION AND AUTHENTICATION TECHNICAL AUTHENTICATOR MANAGEMENT5.d. IA 5 IDENTIFICATION AND AUTHENTICATION TECHNICAL AUTHENTICATOR MANAGEMENT5.e. IA 5 IDENTIFICATION AND AUTHENTICATION TECHNICAL AUTHENTICATOR MANAGEMENT5.f. IA 5 IDENTIFICATION AND AUTHENTICATION TECHNICAL AUTHENTICATOR MANAGEMENT5.g. IA 5 IDENTIFICATION AND AUTHENTICATION TECHNICAL AUTHENTICATOR MANAGEMENT5.h. IA 5 IDENTIFICATION AND AUTHENTICATION TECHNICAL AUTHENTICATOR MANAGEMENT5.i. IA 5 IDENTIFICATION AND AUTHENTICATION TECHNICAL AUTHENTICATOR MANAGEMENT5.(1) IA 5 IDENTIFICATION AND AUTHENTICATION TECHNICAL AUTHENTICATOR MANAGEMENT5.(1).(a) IA 5.(1) IDENTIFICATION AND AUTHENTICATION TECHNICAL AUTHENTICATOR MANAGEMENT5.(1).(b) IA 5.(1) IDENTIFICATION AND AUTHENTICATION TECHNICAL AUTHENTICATOR MANAGEMENT5.(1).(c) IA 5.(1) IDENTIFICATION AND AUTHENTICATION TECHNICAL AUTHENTICATOR MANAGEMENT5.(1).(d) IA 5.(1) IDENTIFICATION AND AUTHENTICATION TECHNICAL AUTHENTICATOR MANAGEMENT5.(1).(e) IA 5.(1) IDENTIFICATION AND AUTHENTICATION TECHNICAL AUTHENTICATOR MANAGEMENT5.(2) IA 5 IDENTIFICATION AND AUTHENTICATION TECHNICAL AUTHENTICATOR MANAGEMENT5.(2).(a) IA 5.(2) IDENTIFICATION AND AUTHENTICATION TECHNICAL AUTHENTICATOR MANAGEMENT5.(2).(b) IA 5.(2) IDENTIFICATION AND AUTHENTICATION TECHNICAL AUTHENTICATOR MANAGEMENT5.(2).(c) IA 5.(2) IDENTIFICATION AND AUTHENTICATION TECHNICAL AUTHENTICATOR MANAGEMENT5.(3) IA 5 IDENTIFICATION AND AUTHENTICATION TECHNICAL AUTHENTICATOR MANAGEMENT5.(4) IA 5
- 23. IDENTIFICATION AND AUTHENTICATION TECHNICAL AUTHENTICATOR MANAGEMENT5.(5) IA 5 IDENTIFICATION AND AUTHENTICATION TECHNICAL AUTHENTICATOR MANAGEMENT5.(6) IA 5 IDENTIFICATION AND AUTHENTICATION TECHNICAL AUTHENTICATOR MANAGEMENT5.(7) IA 5 IDENTIFICATION AND AUTHENTICATION TECHNICAL AUTHENTICATOR MANAGEMENT5.(8) IA 5 IDENTIFICATION AND AUTHENTICATION TECHNICAL AUTHENTICATOR FEEDBACK IA 6 IDENTIFICATION AND AUTHENTICATION TECHNICAL CRYPTOGRAPHIC MODULE AUTHENTICATION IA 7 IDENTIFICATION AND AUTHENTICATION TECHNICAL IDENTIFICATION AND AUTHENTICATION (NON-ORGANIZATIONAL USERS) IA 8 INCIDENT RESPONSE OPERATIONAL INCIDENT RESPONSE POLICY AND PROCEDURES IR 1 INCIDENT RESPONSE OPERATIONAL INCIDENT RESPONSE POLICY AND PROCEDURES IR 1 1.a. INCIDENT RESPONSE OPERATIONAL INCIDENT RESPONSE POLICY AND PROCEDURES IR 1 1.b. INCIDENT RESPONSE OPERATIONAL INCIDENT RESPONSE TRAINING 2 IR INCIDENT RESPONSE OPERATIONAL INCIDENT RESPONSE TRAINING 2.a. IR 2 INCIDENT RESPONSE OPERATIONAL INCIDENT RESPONSE TRAINING 2.b. IR 2 INCIDENT RESPONSE OPERATIONAL INCIDENT RESPONSE TRAINING 2.(1) IR 2 INCIDENT RESPONSE OPERATIONAL INCIDENT RESPONSE TRAINING 2.(2) IR 2 INCIDENT RESPONSE OPERATIONAL INCIDENT RESPONSE TESTING AND EXERCISES IR 3 INCIDENT RESPONSE OPERATIONAL INCIDENT RESPONSE TESTING AND EXERCISES IR 3 3.(1) INCIDENT RESPONSE OPERATIONAL INCIDENT HANDLING IR 4 INCIDENT RESPONSE OPERATIONAL INCIDENT HANDLING IR 4 4.a. INCIDENT RESPONSE OPERATIONAL INCIDENT HANDLING IR 4 4.b. INCIDENT RESPONSE OPERATIONAL INCIDENT HANDLING IR 4 4.c. INCIDENT RESPONSE OPERATIONAL INCIDENT HANDLING IR 4 4.(1) INCIDENT RESPONSE OPERATIONAL INCIDENT HANDLING IR 4 4.(2) INCIDENT RESPONSE OPERATIONAL INCIDENT HANDLING IR 4 4.(3) INCIDENT RESPONSE OPERATIONAL INCIDENT HANDLING IR 4 4.(4) INCIDENT RESPONSE OPERATIONAL INCIDENT HANDLING IR 4 4.(5) INCIDENT RESPONSE OPERATIONAL INCIDENT MONITORING IR 5 INCIDENT RESPONSE OPERATIONAL INCIDENT MONITORING IR 5 5.(1)
- 24. INCIDENT RESPONSE OPERATIONAL INCIDENT REPORTING IR 6 INCIDENT RESPONSE OPERATIONAL INCIDENT REPORTING IR 6 6.a. INCIDENT RESPONSE OPERATIONAL INCIDENT REPORTING IR 6 6.b. INCIDENT RESPONSE OPERATIONAL INCIDENT REPORTING IR 6 6.(1) INCIDENT RESPONSE OPERATIONAL INCIDENT REPORTING IR 6 6.(2) INCIDENT RESPONSE OPERATIONAL INCIDENT RESPONSE ASSISTANCE IR 7 INCIDENT RESPONSE OPERATIONAL INCIDENT RESPONSE ASSISTANCE IR 7 7.(1) INCIDENT RESPONSE OPERATIONAL INCIDENT RESPONSE ASSISTANCE IR 7 7.(2) INCIDENT RESPONSE OPERATIONAL INCIDENT RESPONSE ASSISTANCE IR 7.(2) 7.(2).(a) INCIDENT RESPONSE OPERATIONAL INCIDENT RESPONSE ASSISTANCE IR 7.(2) 7.(2).(b) INCIDENT RESPONSE OPERATIONAL INCIDENT RESPONSE PLAN IR 8 INCIDENT RESPONSE OPERATIONAL INCIDENT RESPONSE PLAN IR 8 8.a. INCIDENT RESPONSE OPERATIONAL INCIDENT RESPONSE PLAN IR 8 8.b. INCIDENT RESPONSE OPERATIONAL INCIDENT RESPONSE PLAN IR 8 8.c. INCIDENT RESPONSE OPERATIONAL INCIDENT RESPONSE PLAN IR 8 8.d. INCIDENT RESPONSE OPERATIONAL INCIDENT RESPONSE PLAN IR 8 8.e. MAINTENANCE OPERATIONALYSTEM MAINTENANCE POLICY 1 S MA AND PROCEDURES MAINTENANCE OPERATIONALYSTEM MAINTENANCE POLICY 1.a. PROCEDURES S MA 1 AND MAINTENANCE OPERATIONALYSTEM MAINTENANCE POLICY 1.b. PROCEDURES S MA 1 AND MAINTENANCE OPERATIONAL ONTROLLED MAINTENANCE C MA 2 MAINTENANCE OPERATIONAL ONTROLLED MAINTENANCE C MA 2 2.a. MAINTENANCE OPERATIONAL ONTROLLED MAINTENANCE C MA 2 2.b.
- 25. MAINTENANCE OPERATIONAL ONTROLLED MAINTENANCE C MA 2 2.c. MAINTENANCE OPERATIONAL ONTROLLED MAINTENANCE C MA 2 2.d. MAINTENANCE OPERATIONAL ONTROLLED MAINTENANCE C MA 2 2.e. MAINTENANCE OPERATIONAL ONTROLLED MAINTENANCE C MA 2 2.(1) MAINTENANCE OPERATIONAL ONTROLLED MAINTENANCE C MA 2.(1) 2.(1).(a) MAINTENANCE OPERATIONAL ONTROLLED MAINTENANCE C MA 2.(1) 2.(1).(b) MAINTENANCE OPERATIONAL ONTROLLED MAINTENANCE C MA 2.(1) 2.(1).(c) MAINTENANCE OPERATIONAL ONTROLLED MAINTENANCE C MA 2.(1) 2.(1).(d) MAINTENANCE OPERATIONAL ONTROLLED MAINTENANCE C MA 2.(1) 2.(1).(e) MAINTENANCE OPERATIONAL ONTROLLED MAINTENANCE C MA 2 2.(2) MAINTENANCE OPERATIONAL AINTENANCE TOOLS M MA 3 MAINTENANCE OPERATIONAL AINTENANCE TOOLS M MA 3 3.(1) MAINTENANCE OPERATIONAL AINTENANCE TOOLS M MA 3 3.(2) MAINTENANCE OPERATIONAL AINTENANCE TOOLS M MA 3 3.(3) MAINTENANCE OPERATIONAL AINTENANCE TOOLS M MA 3 3.(4) MAINTENANCE OPERATIONAL ON-LOCAL MAINTENANCE N MA 4 MAINTENANCE OPERATIONAL ON-LOCAL MAINTENANCE N MA 4 4.a. MAINTENANCE OPERATIONAL ON-LOCAL MAINTENANCE N MA 4 4.b. MAINTENANCE OPERATIONAL ON-LOCAL MAINTENANCE N MA 4 4.c. MAINTENANCE OPERATIONAL ON-LOCAL MAINTENANCE N MA 4 4.d. MAINTENANCE OPERATIONAL ON-LOCAL MAINTENANCE N MA 4 4.e. MAINTENANCE OPERATIONAL ON-LOCAL MAINTENANCE N MA 4 4.(1) MAINTENANCE OPERATIONAL ON-LOCAL MAINTENANCE N MA 4 4.(2) MAINTENANCE OPERATIONAL ON-LOCAL MAINTENANCE N MA 4 4.(3)
- 26. MAINTENANCE OPERATIONAL ON-LOCAL MAINTENANCE N MA 4.(3) 4.(3).(a) MAINTENANCE OPERATIONAL ON-LOCAL MAINTENANCE N MA 4.(3) 4.(3).(b) MAINTENANCE OPERATIONAL ON-LOCAL MAINTENANCE N MA 4 4.(4) MAINTENANCE OPERATIONAL ON-LOCAL MAINTENANCE N MA 4.(4) 4.(4).(a) MAINTENANCE OPERATIONAL ON-LOCAL MAINTENANCE N MA 4.(4) 4.(4).(b) MAINTENANCE OPERATIONAL ON-LOCAL MAINTENANCE N MA 4 4.(5) MAINTENANCE OPERATIONAL ON-LOCAL MAINTENANCE N MA 4.(5) 4.(5).(a) MAINTENANCE OPERATIONAL ON-LOCAL MAINTENANCE N MA 4.(5) 4.(5).(b) MAINTENANCE OPERATIONAL ON-LOCAL MAINTENANCE N MA 4 4.(6) MAINTENANCE OPERATIONAL ON-LOCAL MAINTENANCE N MA 4 4.(7) MAINTENANCE OPERATIONAL AINTENANCE PERSONNEL M MA 5 MAINTENANCE OPERATIONAL AINTENANCE PERSONNEL M MA 5 5.a. MAINTENANCE OPERATIONAL AINTENANCE PERSONNEL M MA 5 5.b. MAINTENANCE OPERATIONAL AINTENANCE PERSONNEL M MA 5 5.(1) MAINTENANCE OPERATIONAL AINTENANCE PERSONNEL M MA 5.(1) 5.(1).(a) MAINTENANCE OPERATIONAL AINTENANCE PERSONNEL M MA 5.(1) 5.(1).(b) MAINTENANCE OPERATIONAL AINTENANCE PERSONNEL M MA 5.(1) 5.(1).(c) MAINTENANCE OPERATIONAL AINTENANCE PERSONNEL M MA 5 5.(2) MAINTENANCE OPERATIONAL AINTENANCE PERSONNEL M MA 5 5.(3) MAINTENANCE OPERATIONAL AINTENANCE PERSONNEL M MA 5 5.(4) MAINTENANCE OPERATIONAL AINTENANCE PERSONNEL M MA 5.(4) 5.(4).(a) MAINTENANCE OPERATIONAL AINTENANCE PERSONNEL M MA 5.(4) 5.(4).(b)
- 27. MAINTENANCE OPERATIONALIMELY MAINTENANCE T MA 6 MEDIA PROTECTION OPERATIONAL EDIA PROTECTION POLICY AND PROCEDURES M MP 1 MEDIA PROTECTION OPERATIONAL EDIA PROTECTION POLICY AND PROCEDURES M MP 1 1.a. MEDIA PROTECTION OPERATIONAL EDIA PROTECTION POLICY AND PROCEDURES M MP 1 1.b. MEDIA PROTECTION OPERATIONAL EDIA ACCESS M MP 2 MEDIA PROTECTION OPERATIONAL EDIA ACCESS M MP 2 2.(1) MEDIA PROTECTION OPERATIONAL EDIA ACCESS M MP 2 2.(2) MEDIA PROTECTION OPERATIONAL EDIA MARKING M MP 3 MEDIA PROTECTION OPERATIONAL EDIA MARKING M MP 3 3.a. MEDIA PROTECTION OPERATIONAL EDIA MARKING M MP 3 3.b. MEDIA PROTECTION OPERATIONAL EDIA STORAGE M MP 4 MEDIA PROTECTION OPERATIONAL EDIA STORAGE M MP 4 4.a.
- 28. MEDIA PROTECTION OPERATIONAL EDIA STORAGE M MP 4 4.b. MEDIA PROTECTION OPERATIONAL EDIA STORAGE M MP 4 4.(1) MEDIA PROTECTION OPERATIONAL EDIA TRANSPORT M MP 5 MEDIA PROTECTION OPERATIONAL EDIA TRANSPORT M MP 5 5.a. MEDIA PROTECTION OPERATIONAL EDIA TRANSPORT M MP 5 5.b.
- 29. MEDIA PROTECTION OPERATIONAL EDIA TRANSPORT M MP 5 5.c. MEDIA PROTECTION OPERATIONAL EDIA TRANSPORT M MP 5 5.(1) MEDIA PROTECTION OPERATIONAL EDIA TRANSPORT M MP 5 5.(2) MEDIA PROTECTION OPERATIONAL EDIA TRANSPORT M MP 5 5.(3) MEDIA PROTECTION OPERATIONAL EDIA TRANSPORT M MP 5 5.(4) MEDIA PROTECTION OPERATIONAL EDIA SANITIZATION M MP 6 MEDIA PROTECTION OPERATIONAL EDIA SANITIZATION M MP 6 6.(1) MEDIA PROTECTION OPERATIONAL EDIA SANITIZATION M MP 6 6.(2) MEDIA PROTECTION OPERATIONAL EDIA SANITIZATION M MP 6 6.(3) MEDIA PROTECTION OPERATIONAL EDIA SANITIZATION M MP 6 6.(4) MEDIA PROTECTION OPERATIONAL EDIA SANITIZATION M MP 6 6.(5) MEDIA PROTECTION OPERATIONAL EDIA SANITIZATION M MP 6 6.(6) PHYSICAL AND ENVIRONMENTAL PROTECTIONAND ENVIRONMENTAL PROTECTION POLICY AND PROCEDURES OPERATIONALHYSICAL PE P 1 PHYSICAL AND ENVIRONMENTAL PROTECTIONAND ENVIRONMENTAL PROTECTION POLICY AND PROCEDURES OPERATIONALHYSICAL PE P 1 1.a. PHYSICAL AND ENVIRONMENTAL PROTECTIONAND ENVIRONMENTAL PROTECTION POLICY AND PROCEDURES OPERATIONALHYSICAL PE P 1 1.b. PHYSICAL AND ENVIRONMENTAL PROTECTIONACCESS AUTHORIZATIONS OPERATIONALHYSICAL PE P 2 PHYSICAL AND ENVIRONMENTAL PROTECTIONACCESS AUTHORIZATIONS OPERATIONALHYSICAL PE P 2 2.a. PHYSICAL AND ENVIRONMENTAL PROTECTIONACCESS AUTHORIZATIONS OPERATIONALHYSICAL PE P 2 2.b. PHYSICAL AND ENVIRONMENTAL PROTECTIONACCESS AUTHORIZATIONS OPERATIONALHYSICAL PE P 2 2.c. PHYSICAL AND ENVIRONMENTAL PROTECTIONACCESS AUTHORIZATIONS OPERATIONALHYSICAL PE P 2 2.(1) PHYSICAL AND ENVIRONMENTAL PROTECTIONACCESS AUTHORIZATIONS OPERATIONALHYSICAL PE P 2 2.(2) PHYSICAL AND ENVIRONMENTAL PROTECTIONACCESS AUTHORIZATIONS OPERATIONALHYSICAL PE P 2 2.(3)
- 30. PHYSICAL AND ENVIRONMENTAL PROTECTIONACCESS CONTROL OPERATIONALHYSICAL PE P 3 PHYSICAL AND ENVIRONMENTAL PROTECTIONACCESS CONTROL OPERATIONALHYSICAL PE P 3 3.a. PHYSICAL AND ENVIRONMENTAL PROTECTIONACCESS CONTROL OPERATIONALHYSICAL PE P 3 3.b. PHYSICAL AND ENVIRONMENTAL PROTECTIONACCESS CONTROL OPERATIONALHYSICAL PE P 3 3.c. PHYSICAL AND ENVIRONMENTAL PROTECTIONACCESS CONTROL OPERATIONALHYSICAL PE P 3 3.d. PHYSICAL AND ENVIRONMENTAL PROTECTIONACCESS CONTROL OPERATIONALHYSICAL PE P 3 3.e. PHYSICAL AND ENVIRONMENTAL PROTECTIONACCESS CONTROL OPERATIONALHYSICAL PE P 3 3.f. PHYSICAL AND ENVIRONMENTAL PROTECTIONACCESS CONTROL OPERATIONALHYSICAL PE P 3 3.g. PHYSICAL AND ENVIRONMENTAL PROTECTIONACCESS CONTROL OPERATIONALHYSICAL PE P 3 3.(1) PHYSICAL AND ENVIRONMENTAL PROTECTIONACCESS CONTROL OPERATIONALHYSICAL PE P 3 3.(2) PHYSICAL AND ENVIRONMENTAL PROTECTIONACCESS CONTROL OPERATIONALHYSICAL PE P 3 3.(3) PHYSICAL AND ENVIRONMENTAL PROTECTIONACCESS CONTROL OPERATIONALHYSICAL PE P 3 3.(4) PHYSICAL AND ENVIRONMENTAL PROTECTIONACCESS CONTROL OPERATIONALHYSICAL PE P 3 3.(5) PHYSICAL AND ENVIRONMENTAL PROTECTIONACCESS CONTROL OPERATIONALHYSICAL PE P 3 3.(6) PHYSICAL AND ENVIRONMENTAL PROTECTION PE OPERATIONALCCESS CONTROL FOR TRANSMISSION MEDIUM A 4 PHYSICAL AND ENVIRONMENTAL PROTECTION PE OPERATIONALCCESS CONTROL FOR OUTPUT5DEVICES A PHYSICAL AND ENVIRONMENTAL PROTECTION PE OPERATIONAL ONITORING PHYSICAL ACCESS M 6 PHYSICAL AND ENVIRONMENTAL PROTECTION PE OPERATIONAL ONITORING PHYSICAL ACCESS M 6 6.a. PHYSICAL AND ENVIRONMENTAL PROTECTION PE OPERATIONAL ONITORING PHYSICAL ACCESS M 6 6.b. PHYSICAL AND ENVIRONMENTAL PROTECTION PE OPERATIONAL ONITORING PHYSICAL ACCESS M 6 6.c. PHYSICAL AND ENVIRONMENTAL PROTECTION PE OPERATIONAL ONITORING PHYSICAL ACCESS M 6 6.(1) PHYSICAL AND ENVIRONMENTAL PROTECTION PE OPERATIONAL ONITORING PHYSICAL ACCESS M 6 6.(2) PHYSICAL AND ENVIRONMENTAL PROTECTION PE OPERATIONALISITOR CONTROL V 7 PHYSICAL AND ENVIRONMENTAL PROTECTION PE OPERATIONALISITOR CONTROL V 7 7.(1) PHYSICAL AND ENVIRONMENTAL PROTECTION PE OPERATIONALISITOR CONTROL V 7 7.(2) PHYSICAL AND ENVIRONMENTAL PROTECTION PE OPERATIONALCCESS RECORDS A 8 PHYSICAL AND ENVIRONMENTAL PROTECTION PE OPERATIONALCCESS RECORDS A 8 8.a. PHYSICAL AND ENVIRONMENTAL PROTECTION PE OPERATIONALCCESS RECORDS A 8 8.b. PHYSICAL AND ENVIRONMENTAL PROTECTION PE OPERATIONALCCESS RECORDS A 8 8.(1) PHYSICAL AND ENVIRONMENTAL PROTECTION PE OPERATIONALCCESS RECORDS A 8 8.(2) PHYSICAL AND ENVIRONMENTAL PROTECTION PE OPERATIONALOWER EQUIPMENT AND POWER CABLING P 9
- 31. PHYSICAL AND ENVIRONMENTAL PROTECTION PE OPERATIONALOWER EQUIPMENT AND POWER CABLING P 9 9.(1) PHYSICAL AND ENVIRONMENTAL PROTECTION PE OPERATIONALOWER EQUIPMENT AND POWER CABLING P 9 9.(2) PHYSICAL AND ENVIRONMENTAL PROTECTION PE OPERATIONALMERGENCY SHUTOFF E 10 PHYSICAL AND ENVIRONMENTAL PROTECTION PE OPERATIONALMERGENCY SHUTOFF 10 E 10.a. PHYSICAL AND ENVIRONMENTAL PROTECTION PE OPERATIONALMERGENCY SHUTOFF 10 E 10.b. PHYSICAL AND ENVIRONMENTAL PROTECTION PE OPERATIONALMERGENCY SHUTOFF E 10 10.c. PHYSICAL AND ENVIRONMENTAL PROTECTION PE OPERATIONALMERGENCY SHUTOFF E 10 10.(1) PHYSICAL AND ENVIRONMENTAL PROTECTION PE OPERATIONALMERGENCY POWER E 11 PHYSICAL AND ENVIRONMENTAL PROTECTION PE OPERATIONALMERGENCY POWER E 11 11.(1) PHYSICAL AND ENVIRONMENTAL PROTECTION PE OPERATIONALMERGENCY POWER E 11 11.(2) PHYSICAL AND ENVIRONMENTAL PROTECTION PE OPERATIONALMERGENCY LIGHTING E 12 PHYSICAL AND ENVIRONMENTAL PROTECTION PE OPERATIONALMERGENCY LIGHTING E 12 12.(1) PHYSICAL AND ENVIRONMENTAL PROTECTION PE OPERATIONALIRE PROTECTION F 13 PHYSICAL AND ENVIRONMENTAL PROTECTION PE OPERATIONALIRE PROTECTION F 13 13.(1) PHYSICAL AND ENVIRONMENTAL PROTECTION PE OPERATIONALIRE PROTECTION F 13 13.(2) PHYSICAL AND ENVIRONMENTAL PROTECTION PE OPERATIONALIRE PROTECTION F 13 13.(3) PHYSICAL AND ENVIRONMENTAL PROTECTION PE OPERATIONALIRE PROTECTION F 13 13.(4) PHYSICAL AND ENVIRONMENTAL PROTECTION PEAND HUMIDITY CONTROLS OPERATIONALEMPERATURE T 14 PHYSICAL AND ENVIRONMENTAL PROTECTION PEAND HUMIDITY CONTROLS OPERATIONALEMPERATURE T 14 14.a. PHYSICAL AND ENVIRONMENTAL PROTECTION PEAND HUMIDITY CONTROLS OPERATIONALEMPERATURE T 14 14.b. PHYSICAL AND ENVIRONMENTAL PROTECTION PEAND HUMIDITY CONTROLS OPERATIONALEMPERATURE T 14 14.(1) PHYSICAL AND ENVIRONMENTAL PROTECTION PEAND HUMIDITY CONTROLS OPERATIONALEMPERATURE T 14 14.(2) PHYSICAL AND ENVIRONMENTAL PROTECTION PE PROTECTION 15 OPERATIONAL ATER DAMAGE W PHYSICAL AND ENVIRONMENTAL PROTECTION PE PROTECTION 15.(1) OPERATIONAL ATER DAMAGE W 15 PHYSICAL AND ENVIRONMENTAL PROTECTION PEREMOVAL OPERATIONAL ELIVERY AND D 16 PHYSICAL AND ENVIRONMENTAL PROTECTION WORK SITE OPERATIONALLTERNATE PE A 17 PHYSICAL AND ENVIRONMENTAL PROTECTION WORK SITE OPERATIONALLTERNATE PE A 17 17.a.
- 32. PHYSICAL AND ENVIRONMENTAL PROTECTION WORK SITE 17 OPERATIONALLTERNATE PE A 17.b. PHYSICAL AND ENVIRONMENTAL PROTECTION WORK SITE 17 OPERATIONALLTERNATE PE A 17.c. PHYSICAL AND ENVIRONMENTAL PROTECTION OF INFORMATION SYSTEM COMPONENTS OPERATIONALOCATION PE L 18 PHYSICAL AND ENVIRONMENTAL PROTECTION OF INFORMATION SYSTEM COMPONENTS OPERATIONALOCATION PE L 18 18.(1) PHYSICAL AND ENVIRONMENTAL PROTECTION PE OPERATIONAL INFORMATION LEAKAGE 19 PHYSICAL AND ENVIRONMENTAL PROTECTION PE OPERATIONAL INFORMATION LEAKAGE 19 19.(1) PLANNING MANAGEMENT SECURITY PLANNING POLICY AND PROCEDURES PL 1 PLANNING MANAGEMENT SECURITY PLANNING POLICY AND PROCEDURES PL 1 1.a. PLANNING MANAGEMENT SECURITY PLANNING POLICY AND PROCEDURES PL 1 1.b. PLANNING MANAGEMENT SYSTEM SECURITY PLAN PL 2 PLANNING MANAGEMENT SYSTEM SECURITY PLAN 2 PL 2.a. PLANNING MANAGEMENT SYSTEM SECURITY PLAN 2 PL 2.b. PLANNING MANAGEMENT SYSTEM SECURITY PLAN 2 PL 2.c. PLANNING MANAGEMENT SYSTEM SECURITY PLAN 2 PL 2.(1) PLANNING MANAGEMENT SYSTEM SECURITY PLAN 2.(1) PL 2.(1).(a) PLANNING MANAGEMENT SYSTEM SECURITY PLAN PL 2.(1) 2.(1).(b) PLANNING MANAGEMENT SYSTEM SECURITY PLAN PL 2 2.(2) PLANNING MANAGEMENT SYSTEM SECURITY PLAN PL 2.(2) 2.(2).(a) PLANNING MANAGEMENT SYSTEM SECURITY PLAN PL 2.(2) 2.(2).(b) PLANNING MANAGEMENT SYSTEM SECURITY PLAN PL 2.(2) 2.(2).(c) PLANNING MANAGEMENT SYSTEM SECURITY PLAN PL 2.(2) 2.(2).(d) PLANNING MANAGEMENT SYSTEM SECURITY PLAN 2.(2) PL 2.(2).(e)
- 33. PLANNING MANAGEMENT SYSTEM SECURITY PLAN UPDATE PL 3 PLANNING MANAGEMENT RULES OF BEHAVIOR PL 4 PLANNING MANAGEMENT RULES OF BEHAVIOR PL 4 4.a. PLANNING MANAGEMENT RULES OF BEHAVIOR PL 4 4.b. PLANNING MANAGEMENT RULES OF BEHAVIOR PL 4 4.(1) PLANNING MANAGEMENT PRIVACY IMPACT ASSESSMENT 5 PL PLANNING MANAGEMENT SECURITY-RELATED ACTIVITY PLANNING PL 6 PROGRAM MANAGEMENT MANAGEMENT INFORMATION SECURITY PROGRAM PLAN PM 1 PROGRAM MANAGEMENT MANAGEMENT INFORMATION SECURITY PROGRAM PLAN PM 1 1.a. PROGRAM MANAGEMENT MANAGEMENT INFORMATION SECURITY PROGRAM PLAN PM 1 1.b.
- 34. PROGRAM MANAGEMENT MANAGEMENT INFORMATION SECURITY PROGRAM PLAN PM 1 1.c. PROGRAM MANAGEMENT MANAGEMENT SENIOR INFORMATION SECURITY OFFICER PM 2 PROGRAM MANAGEMENT MANAGEMENT INFORMATION SECURITY RESOURCES PM 3 PROGRAM MANAGEMENT MANAGEMENT INFORMATION SECURITY RESOURCES PM 3 3.a. PROGRAM MANAGEMENT MANAGEMENT INFORMATION SECURITY RESOURCES PM 3 3.b. PROGRAM MANAGEMENT MANAGEMENT INFORMATION SECURITY RESOURCES PM 3 3.c. PROGRAM MANAGEMENT MANAGEMENT PLAN OF ACTION AND MILESTONES PROCESS PM 4 PROGRAM MANAGEMENT MANAGEMENT INFORMATION SYSTEM INVENTORY PM 5 PROGRAM MANAGEMENT MANAGEMENT INFORMATION SECURITY MEASURES OF PERFORMANCE PM 6 PROGRAM MANAGEMENT MANAGEMENT ENTERPRISE PM ARCHITECTURE 7 PROGRAM MANAGEMENT MANAGEMENT CRITICAL INFRASTRUCTURE PLAN PM 8 PROGRAM MANAGEMENT MANAGEMENT RISK MANAGEMENT STRATEGY 9 PM PROGRAM MANAGEMENT MANAGEMENT RISK MANAGEMENT STRATEGY 9.a. PM 9 PROGRAM MANAGEMENT MANAGEMENT RISK MANAGEMENT STRATEGY 9.b. PM 9 PROGRAM MANAGEMENT MANAGEMENT SECURITY AUTHORIZATION PROCESS PM 10 PROGRAM MANAGEMENT MANAGEMENT SECURITY AUTHORIZATION PROCESS PM 10 10.a. PROGRAM MANAGEMENT MANAGEMENT SECURITY AUTHORIZATION PROCESS PM 10 10.b. PROGRAM MANAGEMENT MANAGEMENT SECURITY AUTHORIZATION PROCESS PM 10 10.c. PROGRAM MANAGEMENT MANAGEMENT MISSION/BUSINESS PROCESS DEFINITION PM 11 PROGRAM MANAGEMENT MANAGEMENT MISSION/BUSINESS PROCESS DEFINITION PM 11 11.a. PROGRAM MANAGEMENT MANAGEMENT MISSION/BUSINESS PROCESS DEFINITION PM 11 11.b. PERSONNEL SECURITYOPERATIONALERSONNEL PS P SECURITY POLICY AND PROCEDURES 1
- 35. PERSONNEL SECURITYOPERATIONALERSONNEL PS P SECURITY POLICY AND PROCEDURES 1 1.a. PERSONNEL SECURITYOPERATIONALERSONNEL PS P SECURITY POLICY AND PROCEDURES 1 1.b. PERSONNEL SECURITYOPERATIONALOSITION CATEGORIZATION P PS 2 PERSONNEL SECURITYOPERATIONALOSITION CATEGORIZATION P PS 2 2.a. PERSONNEL SECURITYOPERATIONALOSITION CATEGORIZATION P PS 2 2.b. PERSONNEL SECURITYOPERATIONALOSITION CATEGORIZATION P PS 2 2.c. PERSONNEL SECURITYOPERATIONALERSONNEL PS P SCREENING 3 PERSONNEL SECURITYOPERATIONALERSONNEL PS P SCREENING 3 3.a. PERSONNEL SECURITYOPERATIONALERSONNEL PS P SCREENING 3 3.b. PERSONNEL SECURITYOPERATIONALERSONNEL PS P SCREENING 3 3.(1) PERSONNEL SECURITYOPERATIONALERSONNEL PS P SCREENING 3 3.(2) PERSONNEL SECURITYOPERATIONALERSONNEL PS P TERMINATION 4 PERSONNEL SECURITYOPERATIONALERSONNEL PS P TERMINATION 4 4.a. PERSONNEL SECURITYOPERATIONALERSONNEL PS P TERMINATION 4 4.b. PERSONNEL SECURITYOPERATIONALERSONNEL PS P TERMINATION 4 4.c. PERSONNEL SECURITYOPERATIONALERSONNEL PS P TERMINATION 4 4.d. PERSONNEL SECURITYOPERATIONALERSONNEL PS P TRANSFER 5 PERSONNEL SECURITYOPERATIONALCCESS AGREEMENTS A PS 6 PERSONNEL SECURITYOPERATIONALCCESS AGREEMENTS A PS 6 6.a. PERSONNEL SECURITYOPERATIONALCCESS AGREEMENTS A PS 6 6.b. PERSONNEL SECURITYOPERATIONALCCESS AGREEMENTS A PS 6 6.(1) PERSONNEL SECURITYOPERATIONALCCESS AGREEMENTS A PS 6.(1) 6.(1).(a) PERSONNEL SECURITYOPERATIONALCCESS AGREEMENTS A PS 6.(1) 6.(1).(b) PERSONNEL SECURITYOPERATIONALCCESS AGREEMENTS A PS 6 6.(2) PERSONNEL SECURITYOPERATIONALCCESS AGREEMENTS A PS 6.(2) 6.(2).(a) PERSONNEL SECURITYOPERATIONALCCESS AGREEMENTS A PS 6.(2) 6.(2).(b) PERSONNEL SECURITYOPERATIONALCCESS AGREEMENTS 6.(2) 6.(2).(c) A PS PERSONNEL SECURITYOPERATIONALHIRD-PARTY PERSONNEL SECURITY T PS 7 PERSONNEL SECURITYOPERATIONALHIRD-PARTY PERSONNEL SECURITY T PS 7 7.a.