Implementing File Systems-R.D.Sivakumar
•
1 j'aime•335 vues
Implementing File Systems-R.D.Sivakumar
Signaler
Partager
Signaler
Partager
Recommandé
Contenu connexe
En vedette (8)
Alternatives to layer-based image distribution: using CERN filesystem for images

Alternatives to layer-based image distribution: using CERN filesystem for images
Similaire à Implementing File Systems-R.D.Sivakumar
Similaire à Implementing File Systems-R.D.Sivakumar (20)
what are the five major activities of an operating system in regard .pdf

what are the five major activities of an operating system in regard .pdf
Plus de Sivakumar R D .
Plus de Sivakumar R D . (20)
Internet Connections and Its Protocols - R D Sivakumar

Internet Connections and Its Protocols - R D Sivakumar
Different Kinds of Internet Protocols - R.D.Sivakumar

Different Kinds of Internet Protocols - R.D.Sivakumar
Electronic Publishing Tools for E-Learning - R.D.Sivakumar

Electronic Publishing Tools for E-Learning - R.D.Sivakumar
Cognitive and Personal Dimensions of Cyber Learning - R.D.Sivakumar

Cognitive and Personal Dimensions of Cyber Learning - R.D.Sivakumar
Dernier
Mattingly "AI & Prompt Design: The Basics of Prompt Design"

Mattingly "AI & Prompt Design: The Basics of Prompt Design"National Information Standards Organization (NISO)
APM Welcome, APM North West Network Conference, Synergies Across Sectors

APM Welcome, APM North West Network Conference, Synergies Across SectorsAssociation for Project Management
Dernier (20)
A Critique of the Proposed National Education Policy Reform

A Critique of the Proposed National Education Policy Reform
The byproduct of sericulture in different industries.pptx

The byproduct of sericulture in different industries.pptx
Mattingly "AI & Prompt Design: The Basics of Prompt Design"

Mattingly "AI & Prompt Design: The Basics of Prompt Design"
APM Welcome, APM North West Network Conference, Synergies Across Sectors

APM Welcome, APM North West Network Conference, Synergies Across Sectors
Beyond the EU: DORA and NIS 2 Directive's Global Impact

Beyond the EU: DORA and NIS 2 Directive's Global Impact
Russian Call Girls in Andheri Airport Mumbai WhatsApp 9167673311 💞 Full Nigh...

Russian Call Girls in Andheri Airport Mumbai WhatsApp 9167673311 💞 Full Nigh...
Measures of Dispersion and Variability: Range, QD, AD and SD

Measures of Dispersion and Variability: Range, QD, AD and SD
Measures of Central Tendency: Mean, Median and Mode

Measures of Central Tendency: Mean, Median and Mode
BAG TECHNIQUE Bag technique-a tool making use of public health bag through wh...

BAG TECHNIQUE Bag technique-a tool making use of public health bag through wh...
social pharmacy d-pharm 1st year by Pragati K. Mahajan

social pharmacy d-pharm 1st year by Pragati K. Mahajan
Implementing File Systems-R.D.Sivakumar
- 1. Video Lecture and E-Content Created by R.D.SIVAKUMAR,M.Sc.,M.Phil.,M.Tech., Assistant Professor of Computer Science & Assistant Professor and Head, Department of M.Com.(CA), Ayya Nadar Janaki Ammal College, Sivakasi – 626 124. Mobile: 099440-42243 e-mail : sivamsccsit@gmail.com website: www.rdsivakumar.blogspot.in IMPLEMENTING FILE SYSTEMS
- 2. In computing, a file system (or file system) is used to control how information is stored and retrieved. Without a file system, information placed in a storage area would be one large body of information with no way to tell where one piece of information stops and the next begins. DEFINITION OF FILE SYSTEM
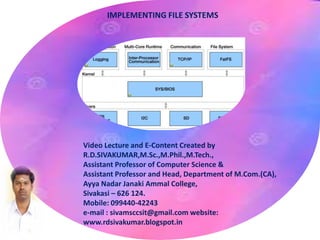
- 3. Hard disks have two important properties that make them suitable for secondary storage of files in file systems Blocks of data can be rewritten in place, They are direct access, allowing any block of data to be accessed with only (relatively) minor movements of the disk heads and rotational latency. FILE SYSTEM STRUCTURE
- 4. At the lowest layer are the physical devices, consisting of the magnetic media, motors & controls, and the electronics connected to them and controlling them. I/O Control consists of device drivers, special software programs ( often written in assembly ) which communicate with the devices by reading and writing special codes directly to and from memory addresses corresponding to the controller card's registers LAYERED DESIGN
- 5. The basic file system level works directly with the device drivers in terms of retrieving and storing raw blocks of data, without any consideration for what is in each block. The file organization module knows about files and their logical blocks, and how they map to physical blocks on the disk. The logical file system deals with all of the meta data associated with a file ( UID, GID, mode, dates, etc ), i.e. everything about the file except the data itself. LAYERED DESIGN (Conti..)
