Web Threat Spotlight: IRS Spam Conceals Backdoor Component (Jan 18, 2010)
•
0 j'aime•2,869 vues
Cybercriminals have already begun abusing the 2010 tax season with spam purporting to be from the IRS. These spam emails contain malicious attachments looking to download malware onto your PC.
Signaler
Partager
Signaler
Partager
Télécharger pour lire hors ligne
Recommandé
Recommandé
Contenu connexe
Plus de Trend Micro
Plus de Trend Micro (20)
AIS Exposed: New vulnerabilities and attacks. (HITB AMS 2014)

AIS Exposed: New vulnerabilities and attacks. (HITB AMS 2014)
Captain, Where Is Your Ship – Compromising Vessel Tracking Systems

Captain, Where Is Your Ship – Compromising Vessel Tracking Systems
Countering the Advanced Persistent Threat Challenge with Deep Discovery

Countering the Advanced Persistent Threat Challenge with Deep Discovery
Where to Store the Cloud Encryption Keys - InterOp 2012

Where to Store the Cloud Encryption Keys - InterOp 2012
[Case Study ~ 2011] Baptist Hospitals of Southest Texas![[Case Study ~ 2011] Baptist Hospitals of Southest Texas](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[Case Study ~ 2011] Baptist Hospitals of Southest Texas](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
[Case Study ~ 2011] Baptist Hospitals of Southest Texas
Encryption in the Public Cloud: 16 Bits of Advice for Security Techniques

Encryption in the Public Cloud: 16 Bits of Advice for Security Techniques
Assuring regulatory compliance, ePHI protection, and secure healthcare delivery

Assuring regulatory compliance, ePHI protection, and secure healthcare delivery
Security Best Practices for Health Information Exchange

Security Best Practices for Health Information Exchange
Web Threat Spotlight Issue 66: Zero-Day Adobe Flash Player Exploits in a Flash

Web Threat Spotlight Issue 66: Zero-Day Adobe Flash Player Exploits in a Flash
Dernier
💉💊+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHABI}}+971581248768
+971581248768 Mtp-Kit (500MG) Prices » Dubai [(+971581248768**)] Abortion Pills For Sale In Dubai, UAE, Mifepristone and Misoprostol Tablets Available In Dubai, UAE CONTACT DR.Maya Whatsapp +971581248768 We Have Abortion Pills / Cytotec Tablets /Mifegest Kit Available in Dubai, Sharjah, Abudhabi, Ajman, Alain, Fujairah, Ras Al Khaimah, Umm Al Quwain, UAE, Buy cytotec in Dubai +971581248768''''Abortion Pills near me DUBAI | ABU DHABI|UAE. Price of Misoprostol, Cytotec” +971581248768' Dr.DEEM ''BUY ABORTION PILLS MIFEGEST KIT, MISOPROTONE, CYTOTEC PILLS IN DUBAI, ABU DHABI,UAE'' Contact me now via What's App…… abortion Pills Cytotec also available Oman Qatar Doha Saudi Arabia Bahrain Above all, Cytotec Abortion Pills are Available In Dubai / UAE, you will be very happy to do abortion in Dubai we are providing cytotec 200mg abortion pill in Dubai, UAE. Medication abortion offers an alternative to Surgical Abortion for women in the early weeks of pregnancy. We only offer abortion pills from 1 week-6 Months. We then advise you to use surgery if its beyond 6 months. Our Abu Dhabi, Ajman, Al Ain, Dubai, Fujairah, Ras Al Khaimah (RAK), Sharjah, Umm Al Quwain (UAQ) United Arab Emirates Abortion Clinic provides the safest and most advanced techniques for providing non-surgical, medical and surgical abortion methods for early through late second trimester, including the Abortion By Pill Procedure (RU 486, Mifeprex, Mifepristone, early options French Abortion Pill), Tamoxifen, Methotrexate and Cytotec (Misoprostol). The Abu Dhabi, United Arab Emirates Abortion Clinic performs Same Day Abortion Procedure using medications that are taken on the first day of the office visit and will cause the abortion to occur generally within 4 to 6 hours (as early as 30 minutes) for patients who are 3 to 12 weeks pregnant. When Mifepristone and Misoprostol are used, 50% of patients complete in 4 to 6 hours; 75% to 80% in 12 hours; and 90% in 24 hours. We use a regimen that allows for completion without the need for surgery 99% of the time. All advanced second trimester and late term pregnancies at our Tampa clinic (17 to 24 weeks or greater) can be completed within 24 hours or less 99% of the time without the need surgery. The procedure is completed with minimal to no complications. Our Women's Health Center located in Abu Dhabi, United Arab Emirates, uses the latest medications for medical abortions (RU-486, Mifeprex, Mifegyne, Mifepristone, early options French abortion pill), Methotrexate and Cytotec (Misoprostol). The safety standards of our Abu Dhabi, United Arab Emirates Abortion Doctors remain unparalleled. They consistently maintain the lowest complication rates throughout the nation. Our Physicians and staff are always available to answer questions and care for women in one of the most difficult times in their lives. The decision to have an abortion at the Abortion Cl+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...

+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...?#DUbAI#??##{{(☎️+971_581248768%)**%*]'#abortion pills for sale in dubai@
Dernier (20)
Elevate Developer Efficiency & build GenAI Application with Amazon Q

Elevate Developer Efficiency & build GenAI Application with Amazon Q
Finding Java's Hidden Performance Traps @ DevoxxUK 2024

Finding Java's Hidden Performance Traps @ DevoxxUK 2024
Emergent Methods: Multi-lingual narrative tracking in the news - real-time ex...

Emergent Methods: Multi-lingual narrative tracking in the news - real-time ex...
CNIC Information System with Pakdata Cf In Pakistan

CNIC Information System with Pakdata Cf In Pakistan
EMPOWERMENT TECHNOLOGY GRADE 11 QUARTER 2 REVIEWER

EMPOWERMENT TECHNOLOGY GRADE 11 QUARTER 2 REVIEWER
Boost Fertility New Invention Ups Success Rates.pdf

Boost Fertility New Invention Ups Success Rates.pdf
+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...

+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...
Cloud Frontiers: A Deep Dive into Serverless Spatial Data and FME

Cloud Frontiers: A Deep Dive into Serverless Spatial Data and FME
Apidays New York 2024 - The Good, the Bad and the Governed by David O'Neill, ...

Apidays New York 2024 - The Good, the Bad and the Governed by David O'Neill, ...
Cloud Frontiers: A Deep Dive into Serverless Spatial Data and FME

Cloud Frontiers: A Deep Dive into Serverless Spatial Data and FME
Repurposing LNG terminals for Hydrogen Ammonia: Feasibility and Cost Saving

Repurposing LNG terminals for Hydrogen Ammonia: Feasibility and Cost Saving
Polkadot JAM Slides - Token2049 - By Dr. Gavin Wood

Polkadot JAM Slides - Token2049 - By Dr. Gavin Wood
"I see eyes in my soup": How Delivery Hero implemented the safety system for ...

"I see eyes in my soup": How Delivery Hero implemented the safety system for ...
Apidays New York 2024 - The value of a flexible API Management solution for O...

Apidays New York 2024 - The value of a flexible API Management solution for O...
Strategize a Smooth Tenant-to-tenant Migration and Copilot Takeoff

Strategize a Smooth Tenant-to-tenant Migration and Copilot Takeoff
Navigating the Deluge_ Dubai Floods and the Resilience of Dubai International...

Navigating the Deluge_ Dubai Floods and the Resilience of Dubai International...
Strategies for Landing an Oracle DBA Job as a Fresher

Strategies for Landing an Oracle DBA Job as a Fresher
Web Threat Spotlight: IRS Spam Conceals Backdoor Component (Jan 18, 2010)
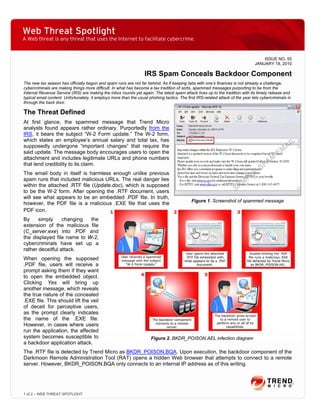
- 1. Web Threat Spotlight A Web threat is any threat that uses the Internet to facilitate cybercrime. ISSUE NO. 55 JANUARY 18, 2010 IRS Spam Conceals Backdoor Component The new tax season has officially begun and spam runs are not far behind. As if keeping tabs with one’s finances is not already a challenge, cybercriminals are making things more difficult. In what has become a tax tradition of sorts, spammed messages purporting to be from the Internal Revenue Service (IRS) are making the inbox rounds yet again. The latest spam attack lives up to the tradition with its timely release and typical email content. Unfortunately, it employs more than the usual phishing tactics. The first IRS-related attack of the year lets cybercriminals in through the back door. The Threat Defined At first glance, the spammed message that Trend Micro analysts found appears rather ordinary. Purportedly from the IRS, it bears the subject “W-2 Form update.” The W-2 form, which states an employee’s annual salary and total tax, has supposedly undergone “important changes” that require the said update. The message body encourages users to open the attachment and includes legitimate URLs and phone numbers that lend credibility to its claim. The email body in itself is harmless enough unlike previous spam runs that included malicious URLs. The real danger lies within the attached .RTF file (Update.doc), which is supposed to be the W-2 form. After opening the .RTF document, users will see what appears to be an embedded .PDF file. In truth, Figure 1. Screenshot of spammed message however, the PDF file is a malicious .EXE file that uses the PDF icon. By simply changing the extension of the malicious file (C_server.exe) into .PDF and the displayed file name to W-2, cybercriminals have set up a rather deceitful attack. When opening the supposed .PDF file, users will receive a prompt asking them if they want to open the embedded object. Clicking Yes will bring up another message, which reveals the true nature of the concealed .EXE file. This should lift the veil of deceit for perceptive users, as the prompt clearly indicates the name of the .EXE file. However, in cases where users run the application, the affected system becomes susceptible to Figure 2. BKDR_POISON.AEL infection diagram a backdoor application attack. The .RTF file is detected by Trend Micro as BKDR_POISON.BQA. Upon execution, the backdoor component of the Darkmoon Remote Administration Tool (RAT) opens a hidden Web browser that attempts to connect to a remote server. However, BKDR_POISON.BQA only connects to an internal IP address as of this writing. 1 of 2 – WEB THREAT SPOTLIGHT
- 2. Web Threat Spotlight A Web threat is any threat that uses the Internet to facilitate cybercrime. Trend Micro analysts found another sample of the spammed IRS message, which appears to be another version of the previous sample. Detected as BKDR_POISON.AEL, the malicious .EXE file concealed in the .RTF attachment successfully connects to a remote server and grants access to the affected system. Establishing a connection allows a cybercriminal to perform any of the following backdoor routines: Capture screenshots, webcam transmissions, and audio clips Delete or search for and upload files Log keystrokes and active windows Modify and search for registry entries Perform a shell command Send system information (IP address, computer name, user name, OS) Update/Uninstall malware View and terminate active windows and ports User Risks and Exposure As previously mentioned, timing is an important factor for IRS-related spam. These messages usually make an appearance when an important IRS deadline is near. The latest attack is no exemption with February 1 just weeks away. A notable difference, however, is that past IRS-related spam attacks have generally been phishing related in nature. They used anything from bogus forms, fake websites, and ZBOT variants to steal personally identifiable records. The data stealing likewise focused on selected information such as bank account and credit card credentials, which cybercriminals use for their own profit. The new attack is different in that it not only facilitates information theft, it also leaves the affected user vulnerable to malicious attacks from a remote user. While there has been an IRS-related attack with a backdoor application for its related malware, the BKDR_POISON malware family has been more commonly seen in vulnerability exploit attacks as of late. Examples include TROJ_PIDIEF.WIA and TROJ_PIDIEF.ABA, which both drop BKDR_POISON variants. As such, the new IRS spam and BKDR_POISON tandem is not a familiar scenario. This could signal a tactical change not just for IRS-related spam but for spammed messages in general. As such, users need to be more vigilant in filtering their email messages, especially if they are using unprotected systems. Trend Micro Solutions and Recommendations Trend Micro™ Smart Protection Network™ infrastructure delivers security that is smarter than conventional approaches. Leveraged across Trend Micro’s solutions and services, Smart Protection Network combines unique in-the-cloud reputation technologies with patent-pending threat correlation technology to immediately and automatically protect your information wherever you connect. In this attack, Smart Protection Network’s email reputation service blocks all emails related to this spam run. File reputation service detects and prevents the download of malicious files detected as BKDR_POISON.BQA and BKDR_POISON.AEL. Web reputation service prevents access to the malicious remote server. The following post at the TrendLabs Malware Blog discusses this threat: http://blog.trendmicro.com/bogus-irs-w-2-form-leads-to-malware/ The virus reports are found here: http://threatinfo.trendmicro.com/vinfo/virusencyclo/default5.asp?VName=BKDR_POISON.BQA http://threatinfo.trendmicro.com/vinfo/virusencyclo/default5.asp?VName=BKDR_POISON.AEL http://threatinfo.trendmicro.com/vinfo/virusencyclo/default5.asp?VName=TROJ_PIDIEF.WIA http://threatinfo.trendmicro.com/vinfo/virusencyclo/default5.asp?VName=TROJ_PIDIEF.ABA Other related posts are found here: http://blog.trendmicro.com/phishers-hit-multiple-banks-with-one-stone/ http://blog.trendmicro.com/tax-season-is-phishing-season/ http://blog.trendmicro.com/fake-form-w-8ben-used-in-irs-tax-scams/ http://blog.trendmicro.com/social-engineering-watch-another-irs-scam/ 2 of 2 – WEB THREAT SPOTLIGHT
