Handheld Devices & BYOD: Are Enterprises There Yet? - Management Information Systems And Technology
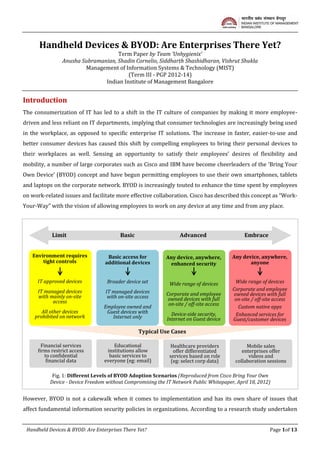
- 1. Handheld Devices & BYOD: Are Enterprises There Yet? Term Paper by Team ‘Unhygienix’ Anusha Subramanian, Shadin Cornelio, Siddharth Shashidharan, Vishrut Shukla Management of Information Systems & Technology (MIST) (Term III - PGP 2012-14) Indian Institute of Management Bangalore Introduction The consumerization of IT has led to a shift in the IT culture of companies by making it more employeedriven and less reliant on IT departments, implying that consumer technologies are increasingly being used in the workplace, as opposed to specific enterprise IT solutions. The increase in faster, easier-to-use and better consumer devices has caused this shift by compelling employees to bring their personal devices to their workplaces as well. Sensing an opportunity to satisfy their employees’ desires of flexibility and mobility, a number of large corporates such as Cisco and IBM have become cheerleaders of the ‘Bring Your Own Device’ (BYOD) concept and have begun permitting employees to use their own smartphones, tablets and laptops on the corporate network. BYOD is increasingly touted to enhance the time spent by employees on work-related issues and facilitate more effective collaboration. Cisco has described this concept as “WorkYour-Way” with the vision of allowing employees to work on any device at any time and from any place. Limit Basic Advanced Environment requires tight controls Basic access for additional devices Any device, anywhere, enhanced security Any device, anywhere, anyone IT approved devices Broader device set Wide range of devices IT managed devices with mainly on-site access IT managed devices with on-site access Corporate and employee owned devices with full on-site / off-site access Wide range of devices Corporate and employee owned devices with full on-site / off-site access Custom native apps Enhanced services for Guest/customer devices All other devices prohibited on network Employee owned and Guest devices with Internet only Device-side security, Internet on Guest device Embrace Typical Use Cases Financial services firms restrict access to confidential financial data Educational institutions allow basic services to everyone (eg: email) Healthcare providers offer differentiated services based on role (eg: select corp data) Mobile sales enterprises offer videos and collaboration sessions Fig. 1: Different Levels of BYOD Adoption Scenarios (Reproduced from Cisco Bring Your Own Device - Device Freedom without Compromising the IT Network Public Whitepaper, April 18, 2012) However, BYOD is not a cakewalk when it comes to implementation and has its own share of issues that affect fundamental information security policies in organizations. According to a research study undertaken Handheld Devices & BYOD: Are Enterprises There Yet? Page 1of 13
- 2. by Logicalis, around 17.7% of the employees surveyed claimed that their IT departments were uninformed of their usage of personal devices at the workplace, and 28.4% suggested that their IT departments preferred to actively ignore paying special attention to the IT consumerization trend despite being aware of it. This is set to change though as data security, featuring as the #1, #2 and #3 concern for top CIOs today has recently gained back the limelight thanks to high profile data breaches at firms like Yahoo! and LinkedIn. Unsurprisingly, more than 50% of the firms surveyed by Forrester Consulting reflect serious concerns about BYOD speculating whether adopting this phenomenon is a gateway to hell by opening a fatal can of worms for IT policy enforcers. There is however no doubt that BYOD is keeping everyone across the board busy and is a truly enterprisewide project engaging the engineering teams, application teams, security and compliance teams as well as executives and human resources personnel. Technical experts are busy ironing out the remaining wrinkles in the technology architecture. IT policy makers are debating about clear guidelines and best practices that they should adopt in order to prevent BYOD from slipping out of control. Business executives are weighing the predicted productivity improvements and revenue gains against the serious security challenges and careful change management to be undertaken when deciding to throw the switch in favour of BYOD. Notwithstanding, industry watchdogs and experts are busy debating whether BYOD is another one of those mere fads presently generating a lot of buzz at its peak of inflated expectation or whether it will persist and proliferate to change the way companies conduct business. Field Data For the purpose of gaining first-hand insights into the above mentioned topics, the authors studied world’s leading network equipment manufacturer Cisco Systems, Inc. - one of the early adopters and enthusiastic cheerleader of the BYOD trend. Cisco, which has applied the BYOD programme within its corporate organization for employees and is encouraging partners to follow suit as well, also offers BYOD solutions portfolio for clients under its ‘Borderless Network’ vision. The aim of the field research was to find out how mobile technologies fit into Cisco’s organizational philosophy, the current scale of handheld device usage/deployment in the organization, the design of the technology architecture, early signs of impact created by the adoption of tablets and BYOD in business terms, top management’s, IT policy makers’ and employees’ perspectives about the new trend, how the enterprise’s IT Policy has been modified to accommodate these changes, strategic and operational challenges being faced by the company in BYOD’s adoption and key takeaways for the future. Executive Perspective: To get deeper insights from the topmost decision-making level regarding BYOD adoption, the authors interviewed Mr. Johnson Jose, Senior Director, Cisco I.T. in detail. According to Mr. Jose, the product companies are set to gain the most by shifting to employee-owned devices as besides Handheld Devices & BYOD: Are Enterprises There Yet? Page 2of 13
- 3. saving IT support costs for the company, the boost in employee productivity translates into business profits without fail. The services companies that bill their clients based on the number of hours billed may see a contradiction with BYOD as tremendous increases in employee productivity may negatively impact the number of billed hours for such companies and hence, they may only support BYOD from the outset. Mr. Jose also mentioned that though the technology and security architectures are almost fully ironed out for a wide-scale BYOD deployment model, the biggest challenges of dealing with employee resistance to change and climbing a steep adoption curve still remain to be addressed as not all employees, especially at the senior level see value in changing the way they work daily with their devices. He stressed that consistency of user experience and alignment of changed policies with simple logical human behaviour will be critical to ensure the success. IT Policy Maker Perspective: As part of the detailed field research undertaken, the authors conducted a personal interview with Mr. Kiran S. Narayan, I.T. Manager at Cisco Systems about the implementation and future of BYOD at Cisco. According to Mr. Narayan, stage-wise rollouts of pilot BYOD programmes are well underway in different parts of the organization beginning with the support for smartphones and tablets. The choice of devices is explained by the fact that these are the most widely used categories in electronic media apart from PCs and laptops. Cisco currently has over 100,000 end points that include employees’ personal devices being used for a broad range of work-related tasks. Again, Mr. Narayan stresses on the fact that from the corporate point of view, the motivation for implementing and encouraging BYOD is increased productivity, enhanced user experience and more flexibility for users, rather than savings in cost. According to Mr. Kiran, it is interesting to note that the growth in BYOD mirrors the trend in two other important areas – data usage and virtualization. Data consumption around the world has seen an explosive growth in the recent past due to better network infrastructure and connectivity. Cisco uses a thin client known as Virtual Exchange Information (VXI), an interface based on virtualization to provide highly secure connectivity to the company network from anywhere and on any supported device. In 2010, Cisco introduced its popular AnyConnect VPN Client, a secure remote login software that creates an encrypted connection from the user’s end device into the company network. Before a foreign device is granted access to the company network, Cisco IT first checks if the device conforms to a prerequisite set of features, known as a ‘posture’. This comprises of some basic software such as anti-virus package, basic security agent equipped with screening intelligence to name a few. Thereafter, device identity is established and credentials are verified. As Mr. Kiran pointed out, this is done because the company needs to know what type of device is being granted or denied access in order to avoid compromising on security of the network. The company is currently experimenting with different user bases to identify the best way in which BYOD can be introduced on a larger scale beginning with the laptops segment. However, even within Cisco, BYOD cannot be implemented throughout the company because the sensitivity of work varies from one area to another. Another issue that IT policy Handheld Devices & BYOD: Are Enterprises There Yet? Page 3of 13
- 4. makers in Cisco are grappling with is the stark difference in the architecture and development cycles of different platforms running on handhelds such as iOS, Android and Windows. Mr. Kiran is quick in pointing out that while Apple has a relatively longer development period for each updated version of its iOS, Android versioning is much more rapid. Windows for the mobile platform is pretty nascent and faces several stability issues. This is demanding scaled up efforts from Cisco IT teams who are tasked with making access to company network available on these devices in a secure and consistent manner. Analysis of BYOD in Enterprises Drivers of the BYOD Phenomenon Devices Lead BYOD’s Promise of Delivering ‘Beyond the Buzz’: The truth is that the BYOD trend does much more than only addressing some of operational issues which it is mostly perceived to resolve. It is about end users being able to use the computing and communication devices of their own choice whether purchased by the employer, purchased by the employee, or both. The fact that multiple devices exist today for multiple needs (refer to Fig. 1 for device sales) is widely believed to ultimately make way for a single device which will be used for all their computing and communication needs. However, most experts seem to disagree as there will be different devices best suited to some particular uses for example Fig. 2: PC & Non-PC Sales 2011 (in millions) (Source: Deloitte, 2011) laptops have larger screens, faster performance and support more applications which tablets and smartphones cannot deliver. The United States and India are already leading other countries in the percentage of knowledge workers using mobile devices (at nearly 70 %), and countries like China and Mexico are not far behind. This finding feeds positively into the BYOD phenomenon as it indicates that people are using multiple mobile devices, such as laptops, smartphones, and tablet computers, to help them accomplish their tasks. Supporting the above claim with some relevant numbers here, it is estimated that by the end of 2013, the number of mobile-connected devices will exceed earth’s population; whereas by 2017 the world will see over 10 billion mobile-connected devices i.e. nearly 1.4 mobile devices per person. Out of these, 86% will be handheld or personal mobile-ready devices and not surprisingly, the biggest gain in traffic share will come primarily from two areas: a) machine-to-machine (M2M) usage, fuelled by the emergence of the ‘Internet of Things’ and explosion of ‘big data’ (5% of all mobile connections in 2012, 17% in 2017); b) smartphones (16 % in 2012, 27% in 2017). The highest growth area will be handheld tablets growing at a CAGR of 46% followed by M2M at a CAGR of 36%. From an enterprise perspective, on an average, IT leaders expect the number of computing devices to rise from 2.3 per employee in 2012 to Handheld Devices & BYOD: Are Enterprises There Yet? Page 4of 13
- 5. 2.8 in 2014. Table 1 lists the increase in device units and Type of Device Growth in Devices, 2012-2017 CAGR Growth in Mobile Data Traffic, 20122017 CAGR above estimates, one can argue that BYOD, presently climbing Smartphone 20% 81% up its technology lifecycle curve, will continue to stay at the Tablet 46% 113% Laptop 11% 31% M2M Module 36% 89% corresponding increase in the mobile data traffic on these devices. Based on the promising outlook established via the ‘peak of inflated expectations’ for quite some time, before dipping down to the ‘trough of disillusionment’ point, if at all in future. Cisco’s IBSG survey results confirm this as well since according to the survey, 42% of smartphones and 38% of Fig 3: Global Device Units and Mobile Data Traffic Growth (Source: Cisco VNI Mobile Forecast 2013) laptops used in workplaces are now employee-owned thus showing that BYOD, far from being an emerging trend, is already quite entrenched in enterprises. Highly Collaborative Applications & ‘Network as a Platform’: The latest published Cisco Visual Networking Index (VNI) 2013 provides interesting insights about increasing IP traffic in the world. Global mobile data traffic grew 70% in year 2012 and reached 885 petabytes per month at the end of 2012, up from 520 petabytes per month at the end of 2011. To put things into perspective, global mobile data traffic in 2012 (885 petabytes per month) was nearly 12 times greater than the total global Internet traffic in 2000 (75 petabytes per month) and for the first time, mobile video traffic exceeded 50% of the entire traffic in 2012. Cisco further forecasts 11.2 exabytes per month of mobile data traffic by the year 2017 and these figures appear conservative by all estimates since they do not reflect the tablet and smartphone traffic that has largely remained on fixed corporate networks such as office WiFi’s etc. The concept of ‘Network as a Platform’ has already gained momentum in enterprises as work applications, pervasive mobility and new collaboration tools all use rich media, driving a large increase in the amount of video and multimedia traffic traversing the network. In addition to this, as more and more enterprise applications get exported to cloud-based infrastructure, network data traffic can only move in one direction, that of exploding growth. Exabytes per month Fig. 4: Worldwide Mobile Data Traffic Forecast (2010-2017) (Source: Cisco VNI Mobile Forecast 2013) Interestingly, a 2012 research conducted by Cisco points out that 47% of employees in 66% CAGR 2012-17 companies under the study were officially designated “mobile workers”, however a staggering 60% of employees actually use a mobile device for work. In India alone, the corresponding proportions are 51% and 69% respectively. Handheld Devices & BYOD: Are Enterprises There Yet? Page 5of 13
- 6. Overlap between Work and Personal Fuels into the User’s Motivation: Most enterprises are openly recognizing the fact that contrary to the prevalent view about work being a place where people go to, it is actually an activity which people do. Extended connectivity through secure mobile and remote access to the corporate network allows employees tremendous flexibility and increased productivity by blurring the line between designated personal and work time. Mobility allows friends, family, and colleagues to reach them at any time. Thus as employees often end up interweaving work and personal tasks, they probably do not want to carry and switch between personal and work devices and rather use the same device currently held in their hands to attend to all kinds of tasks including corporate work as well. In brief, today’s knowledge worker is never really “out of the office”. BYOD is attractive because strict lines of demarcation over what content can be accessed, downloaded, or used on a company-owned device are blurred on a device owned by the employee giving them great control by design. A major caveat to this, and a pretty serious one, however is that co-mingled data on the user devices may lead to security and privacy challenges, which will be explored further in the following discussions. Management keeps productivity gains in mind and not cost savings: From primary discussions the authors have had with executives in corporates and based on the secondary literature already available on BYOD, it has been established that executives are seldom adopting this trend keeping only the resulting cost reductions in mind. As Deliotte’s CIO Matt Peers puts it succinctly, executives must never subscribe to that point of view by allowing themselves into a short-sighted, cost reduction mentality which, apart from being quite counterproductive, can be outright dangerous as well. While it may seem contrary to what BYOD was perceived to be – another one of the cost cutting measures by large corporates, it is found that while the cost of procuring, customizing, maintaining, servicing and disposing company-owned devices will definitely go down with this policy being around, the expense of application security, access authentication, backend infrastructure and regulatory compliance tends to increase. Realizing this trend, the top-of-the-mind return that corporate management is expecting from BYOD rollouts in their organizations is a boost in employee productivity (and therefore revenues) due to the choice and flexibility enabled by this policy. There are, however, mixed empirical results with respect to productivity gains caused by BYOD. A recent study conducted by business communications expert Sam H. DeKay concludes that the research does not convincingly demonstrate that BYOD improves the productivity of employee communications and other computing functions in an organization on its own. On the other hand, a 2012 survey of 202 BYOD decision-makers in enterprises conducted by Forrester Consulting in the United Kingdom, United States, France and Germany found that more than 80% of Handheld Devices & BYOD: Are Enterprises There Yet? Page 6of 13
- 7. employees reported an increase in productivity due to BYOD as they could communicate more frequently with co-workers from anywhere. Therefore, corporate decision-makers should give careful thought to adopting a BYOD implementation if their primary rationale is to enhance workforce productivity. Additionally, there will always be certain industries like investment banking and defence, where the very nature of work will discourage the adoption of BYOD, primarily driven by the need for absolute security of data. Typical Use Cases for BYOD & Order of Effects Home Workers / Telecommuters are, by default, prime BYOD candidates, especially if they belong to the contract workforce. The freedom to use their own personal device can lead to increased productivity. Device level and network security needs special attention in case of telecommuters. Mobile Workers who travel most or all the time, often to client sites will be benefited if permitted to use their personal mobile devices or employer-provided devices at the client location. The most secure option for many of these workers is typically an encrypted VPNconnected secure device that accesses the virtual corporate Fig. 5: First-Order, Second-Order and Third-Order Effects of BYOD network of their employer. Ensuring a ‘no local data stored’ approach i.e. all data is fetched on-demand from the corporate server and is flushed out when the connectivity gets lost, leads to peace of mind for IT policy enforcers as a lost laptop or a smartphone does not post a security threat to the enterprise. Sales Professionals will largely benefit from BYOD as they can access data about the customers and transaction history via the corporate CRM on their handheld device anytime in the field. Permanent Employees who commute daily to office at times choose to take work home. Since they work at night, on weekends, during holidays, while on flights and in airport lounges, most such users prefer a handheld device they are familiar with. Here, BYOD comes to their rescue by allowing them to use their new breed of smartphones and tablets to connect securely to the company network. Since companyprovided devices though more expensive, are more secure and easier to remotely manage, BYOD’s successful implementation in each of the above use cases hinge heavily on addressing security and privacy concerns. Challenges and Risks with BYOD Adoption Experts and IT policy enforcers across the board believe that while many of the benefits of BYOD, such as letting users exercise their choice of using any device anywhere and anytime are accepted to add to employees’ satisfaction, productivity and business revenues, they are somewhat antithetical to the Handheld Devices & BYOD: Are Enterprises There Yet? Page 7of 13
- 8. traditional IT requirements for strict security, device service and support. Some of the key challenges that may potentially turn BYOD into ‘Bring Your Own Demise’ are identified as follows: Providing Device Choice and Support to Users: Traditionally, the IT team in organizations maintained a pre-determined list of approved workplace devices which employees could choose from, typically a standardized desktop, laptop, and perhaps even a small, standardized set of mobile phones and smartphones for sales workers and mobile workforce. The BYOD adoption mandates IT to essentially support all kinds of user devices but keeping practicality in mind, it is a tough problem to solve. Handheld consumer devices are evolving so rapidly that it is impractical to pre-approve each and every brand and form factor. It is also somewhat impractical to expect IT organizations to have the same level of support for each and every device that employees may bring to the workplace. The policy designers are struggling to find a mid-way to keep supporting the BYOD vision to the farthest extent possible within the constraints of the practical limitations of IT support and implementation. Presently, most IT decision-makers have established, at a macro level, the types of devices they will support on their network based their decision on unacceptable security readiness or other user experience factors. However, the support for newer devices keeps getting added from time to time. As far as servicing the user devices are concerned, most organizations have uniformly favoured the adoption of self-support models with very limited or no specific device-level support from corporate IT’s side. Maintaining Secure Access to Corporate Network: The primary success criteria of any BYOD implementation is to ensure security is not sacrificed. IT teams are struggling to establish the minimum security baseline that any device must meet to be used on the corporate network, including WiFi security, VPN access and perhaps add-on software to protect against malware. In addition, due to the wide range of devices, it is critical to be able to identify each device connecting to the network and authenticate both the device and the person using it. IT department needs to minimize the risk of data loss or incursion. Securing corporate data, applications, and systems is essential for any BYOD strategy. On-Boarding of New Devices: Bringing in a new user device onto the network for the first time should ideally be simple, self-service with minimal or zero IT intervention and should be clientless i.e. without the requirement of any pre-installed software on the new device. All IT should be able to do is push updates to the on-boarded devices as the policy mandates. Enforcing Company Usage Policies: Adoption of BYOD must provide a way to enforce policies in line with explicit business requirements as well as regulatory compliance needs depending upon the industry. This can be challenging on a wide flavour of consumer devices like tablets and smartphones. For example, access to the Internet, peer-to-peer file sharing and the usage of specific applications may Handheld Devices & BYOD: Are Enterprises There Yet? Page 8of 13
- 9. be subject to different policies depending on whether the users are on their personal time and network or whether they are accessing the corporate network during work hours. The growing usage of unapproved collaboration tools on user devices for corporate work is a serious concern as well. Protection of Data and Loss Prevention: In industries bounded by strict regulations, the IT department needs to show compliance is possible with BYOD adoption, which can be more challenging, compared to when corporate-owned and managed devices were involved. Cloudbased file sharing and storage services may be convenient for personal data of employees, but can be potential sources of leakage and information breaches for confidential corporate data. Mobile device management (MDM) products and services often come across as the obvious, reflexive response to the need for more secure mobile computing, but a growing number of experts now agree that the answer to BYOD is not to control the device (which was the case for company-owned devices), but to control the data. Mobile Application Management (MAM) and software-based authentication is the preferred approach among IT departments now. Device Management and Visibility on the Network: Many of the handheld devices support multiple connectivity modes ranging from wired and wireless Ethernet (Wf-Fi) to 3G/4G mobile networks. Switching between these different modes during a session is common and IT needs to ensure visibility of all the devices on the corporate network and beyond taking this into account. Ability to Revoke Access Privileges for Devices: Under unexpected circumstances during the lifecycle of a device or employee, it may become necessary to terminate access to the corporate network and data from the user’s device. This becomes a common concern in case of a lost or stolen device, employee termination or even an employee changing roles within the company. Using MAM, IT department needs to ensure they have the ability to immediately revoke access granted to any device and possibly wipe some or all of the data and applications remotely from the device, if the situation demands so. Managing the Increase in Connected Devices: The increasing number of devices connected to the network, most likely with each employee having more than one device simultaneously connected, can lead to IP address starvation as most legacy IP address plans were created under the assumption of fewer devices. This will demand that the IT department hastens the need for IPv6 deployments both inside the enterprise network and at the network edge via to allow secure remote connections. Handheld Devices & BYOD: Are Enterprises There Yet? Page 9of 13
- 10. Keeping the Implementation Simple and Accessible for Users: Different brands and form factors of devices may require different steps for on-boarding and getting connected to the network. The security policies differ depending upon how and where the user is trying to connect. For example, corporate WiFi may require only credentials, whereas connecting through a public wireless hotspot may mandate the use of a VPN connection and increased security steps. A BYOD solution needs to be as simple as possible for users, should be able to provide a consistent experience across device no matter where and when users are connecting from. IT must ensure critical tasks such as mobile printing should be supported from each of the wide range of user devices to guarantee a seamless experience. Policy Prescriptions and Best Practices for BYOD Adoption To address the challenges and complexities identified above, the authors prescribe the following IT policy design and approach for BYOD rollout in any organization: deployments are easy with users who only need low levels of IT support, possibly using self-support communities to share best practices. Deployments may be more difficult with users who have high mobility needs but also require high support levels, such as executives. Conducting such an analysis will help in understanding the entitlement policies and support models and may prevent cost overruns in the IT budget. Low Need for Support High Understanding User Segments & Needs: BYOD Admin/Clerical Call Center/Support Finance Executives Sales Reps Healthcare Worker IT Support Educator/Trainer Technical Support Engineers IT Staff Technical Sales Low Need for Mobility High Fig. 6: User Segments & Needs (Reproduced from Cisco Whitepaper) Selecting a BYOD Adoption Strategy: The IT decision-makers need to select one out of the four levels of adoption strategies as described in Fig. 1 earlier based on their business requirements and risk profile of exposing users to BYOD policies. Lost or Stolen Device Policy: The IT policy must choose one out of the different solutions with varying degrees of capabilities to reach out to a device remotely and destroy data or applications to ensure they remain confidential. Choosing the Right Application & Data Strategy: Adopting the right approach towards serving data and content on the wide array of user devices under BYOD is perhaps the most critical decision the IT has to make. The current architecture allows the choice from among the following options: Handheld Devices & BYOD: Are Enterprises There Yet? Page 10of 13
- 11. Native Application Native Application Data Centre HTML Layer Native Application Data Centre Web Browser Desktop Virtualization Client Native Application Desktop Virtualization Client Native - Local data on device - Maximum performance - Native device experience - Offline possible Browser - Local data on device - Portable to many devices - Browser experience - Always connectivity required Virtual - No local data on device - Maximum security - Translated experience - Always connectivity required Data Centre Fig. 7: Application & Data Mode Choices in a Typical BYOD Deployment (Reproduced from Cisco Bring Your Own Device - Device Freedom without Compromising the IT Network Public Whitepaper, April 18, 2012) The Human Factor - User Cooperation & Change Management: Under BYOD, where the real benefit for the employee comes into play is the concept of working your way (WYW) as Cisco calls it, but often there are cultural and generational mindsets that make it difficult for employees to see value in this change. CEOs, CIOs and executives in organizations need to dig deeper to find out if their employees are culturally ready and mature enough to adopt the WYW life for success. The change leaders need to understand and communicate the benefits of BYOD clearly: a) great place to work; b) work-life balance; c) reputation; d) employee loyalty and turnover and e) long term socio-economic impact of adopting a more flexible work style. Change management needs to be carried out in a careful manner to avoid alienation of older employees who may not see much value in moving away from the current model of work owing to a variety of reasons like loss of dedicated space, disturbances from family, out-of-pocket costs, socializing nature vs isolation, productivity, change in management style and company culture. Handheld Devices & BYOD: Are Enterprises There Yet? Page 11of 13
- 12. Conclusion Old Wine in a New Bottle? The authors conclude that BYOD is not a new concept altogether. For years now, there have been a minority of disgruntled users, employees who cannot abide by company-prescribed devices. Mac users, for example, have always fought against the predominance of Windows laptops at work, claiming they hinder productivity. For an entire generation, now in their thirties and beyond, the primary means of content consumption was the PC/Mac, followed by the laptop. Naturally, these evolved to be fullfledged productivity enhancing devices, to the point where the idea of doing any work without a laptop became inconceivable. However, a paradigm shift has been observed in the way the next generation of employees are perceiving handhelds. For this new generation, the idea of demarcating work and their private life seems unnecessary and therefore, they expect to be able to surf the web, play games, connect to their office workstations, text, chat and e-mail on any and all of their devices. This is the demographic that is primarily going to drive BYOD adoption in companies, as they try to engage with employees and provide them with a flexible work environment. BYOD as a Source of Competitive Advantage: In a stark difference when compared to the previous cycle of smartphone adoption by enterprises, this time, the CIOs across the board are thinking long-term by talking about BYOD as a source competitive advantage - in enabling retention of the best talent and employee satisfaction and in higher productivity, allowing work from anywhere, on any device. In this endeavour, many companies are actively developing apps and endpoint protection services for tablets and smartphones. Some companies are also trying to pre-empt new releases of phones (like the iPhone 5), so that users can have a seamless transition. In public forums and site meetings, CIOs are making all the right noises about empowering employees and reduced controls, banking on improved productivity to pay off their investments in this early adoption of this new trend. This optimism surrounding BYOD, however, needs to be supported wholeheartedly by IT departments by finding ways to efficiently provide secure connectivity and consistent user experience across the ever-growing pool of devices with different form factors and brands. How will the Future Evolve? On a final note, the authors speculate tthe road ahead and what BYOD can make possible in the long term. Globally, 89% of IT leaders from both enterprises and midsize companies support BYOD in some form and 69 % view BYOD “somewhat” or “extremely” positively. Companies are slowly developing a vision for BYOD in the workplace which ties into their long term strategy, of which telecommuting may become a habit for a majority of employees. The world could be at the cusp of a breakthrough – one where companies break out of cubicles and mostly fixed office hours to become truly ‘virtual enterprises’. The transformative benefit of BYOD lies in employee-driven innovation — by allowing employees to decide how, when, and with which tools work is done, adopters of BYOD can potentially unlock the next wave of value. Rather than rushing in for an unplanned deployment in their organization, by fostering BYOD with proper management policies and strong governance model, companies can harness a latent and potent source of gaining competitive advantage over others in the business arena. Handheld Devices & BYOD: Are Enterprises There Yet? Page 12of 13
- 13. References 1. 2. 3. 4. 5. 6. 7. 8. 9. 10. 11. 12. 13. 14. 15. 16. 17. 18. 19. 20. Mobile-Friendly Workplaces, Lev-Ram, Michal, Fortune; 8/13/2012, Vol. 166 Issue 3 Gartner: Enterprises Must Adopt Tablets Early, Channel Insider; 4/6/2011 Business Embraces Tablets - With Caution, Nicholas Kolakowski, eWeek, 10/3/2011 BYOD Finds Increasing Support Among Businesses, Nathan Eddy, eWeek, 1/9/2013 Cisco ConnectedWorld Technology Report, Published by Cisco Systems Inc., 2011 BYOD: Enabling The Chaos, Gordon Thomson, Cisco Security EMEA Article The iPass Global Mobile Workforce Report (Q4 2012), iPass Inc. 2012 BYOD: OMG! or A-OK?, SC Magazine: For IT Security Professionals, Sept/Oct 2012 Are you ready for the BYOD yet?, David Raths, T.H.E. Journal, May 2012 Study: IT Saying Yes To BYOD, ‘the network’ - Cisco’s Technology News Site, 5/16/2012 IT Consumerization: When Gadgets Turn Into Enterprise IT Tools, MIS Quarterly Executive, Sept. ’12 It Shift to Tablets – Have You Prepared?, Puneesh Chaudhry, SiliconIndia, July 2012 Visual Networking Index – IP Traffic Chart, Cisco Visual Networking Index BYOD: A Global Perspective - Harnessing Employee-Led Innovation, Cisco Internet Business Solutions Group Horizons (Survey Report), Joseph Bradley, Jeff Loucks, James Macaulay, Richard Medcalf, Lauren Buckalew, 2012 For BYOD Best Practices, Secure Data, Not Devices, Thor Olavsrud, ComputerWorld Article BYOD (Bring Your Own Device) Policies Affect Everyone, Peter S. Vogel, 5/18/2012, Link Enterprise Security Challenges in the Emerging BYOD Era, CMR Research, Link Cisco Visual Networking Index: Global Mobile Data Traffic Forecast Update, 2012–2017, Link Bring Your Own Device – Agility Through Consistent Delivery, PWC Advisory Services Report Cisco Bring Your Own Device - Device Freedom without Compromising the IT Network Public Whitepaper, 4/18/2012 Handheld Devices & BYOD: Are Enterprises There Yet? Page 13of 13
