Signaler
Partager
Télécharger pour lire hors ligne
Recommandé
Contenu connexe
Similaire à Wireshark protocol analyzer
Similaire à Wireshark protocol analyzer (20)
VPN Monitoring Security Use Case Guide version 1.1 

VPN Monitoring Security Use Case Guide version 1.1
Anomalous Traffic Detection Security Use Case Guide 

Anomalous Traffic Detection Security Use Case Guide
Suspicious Outbound Traffic Monitoring Security Use Case Guide 

Suspicious Outbound Traffic Monitoring Security Use Case Guide
OSTU - Quickstart Guide for Wireshark (by Tony Fortunato)

OSTU - Quickstart Guide for Wireshark (by Tony Fortunato)
Dernier
Dernier (20)
The 7 Things I Know About Cyber Security After 25 Years | April 2024

The 7 Things I Know About Cyber Security After 25 Years | April 2024
[2024]Digital Global Overview Report 2024 Meltwater.pdf![[2024]Digital Global Overview Report 2024 Meltwater.pdf](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[2024]Digital Global Overview Report 2024 Meltwater.pdf](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
[2024]Digital Global Overview Report 2024 Meltwater.pdf
Raspberry Pi 5: Challenges and Solutions in Bringing up an OpenGL/Vulkan Driv...

Raspberry Pi 5: Challenges and Solutions in Bringing up an OpenGL/Vulkan Driv...
Workshop - Best of Both Worlds_ Combine KG and Vector search for enhanced R...

Workshop - Best of Both Worlds_ Combine KG and Vector search for enhanced R...
Automating Google Workspace (GWS) & more with Apps Script

Automating Google Workspace (GWS) & more with Apps Script
What Are The Drone Anti-jamming Systems Technology?

What Are The Drone Anti-jamming Systems Technology?
08448380779 Call Girls In Greater Kailash - I Women Seeking Men

08448380779 Call Girls In Greater Kailash - I Women Seeking Men
Apidays Singapore 2024 - Building Digital Trust in a Digital Economy by Veron...

Apidays Singapore 2024 - Building Digital Trust in a Digital Economy by Veron...
08448380779 Call Girls In Civil Lines Women Seeking Men

08448380779 Call Girls In Civil Lines Women Seeking Men
Strategize a Smooth Tenant-to-tenant Migration and Copilot Takeoff

Strategize a Smooth Tenant-to-tenant Migration and Copilot Takeoff
IAC 2024 - IA Fast Track to Search Focused AI Solutions

IAC 2024 - IA Fast Track to Search Focused AI Solutions
The Role of Taxonomy and Ontology in Semantic Layers - Heather Hedden.pdf

The Role of Taxonomy and Ontology in Semantic Layers - Heather Hedden.pdf
Powerful Google developer tools for immediate impact! (2023-24 C)

Powerful Google developer tools for immediate impact! (2023-24 C)
TrustArc Webinar - Stay Ahead of US State Data Privacy Law Developments

TrustArc Webinar - Stay Ahead of US State Data Privacy Law Developments
Strategies for Unlocking Knowledge Management in Microsoft 365 in the Copilot...

Strategies for Unlocking Knowledge Management in Microsoft 365 in the Copilot...
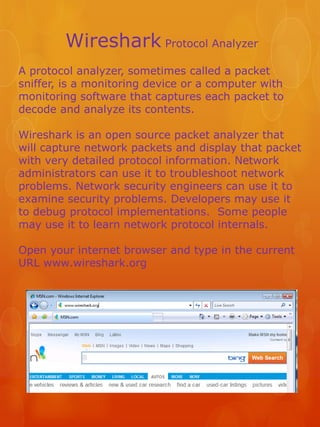
Wireshark protocol analyzer
- 1. Wireshark Protocol Analyzer A protocol analyzer, sometimes called a packet sniffer, is a monitoring device or a computer with monitoring software that captures each packet to decode and analyze its contents. Wireshark is an open source packet analyzer that will capture network packets and display that packet with very detailed protocol information. Network administrators can use it to troubleshoot network problems. Network security engineers can use it to examine security problems. Developers may use it to debug protocol implementations. Some people may use it to learn network protocol internals. Open your internet browser and type in the current URL www.wireshark.org
- 2. Click on Download Wireshark.
- 3. Click on Windows Installer (32 bit). Click on Save.
- 4. In the Save As dialog box, click Save to a location such as your desktop. Wait for the file to download.
- 5. After Download Complete appears, click Run. In the IE Security Warning window, click Run.
- 6. In the User Account Control window, click Allow. Close this window.
- 7. Click Next. Click I Agree.
- 8. Click Next. Click Next.
- 9. Choose your install location, click Next. Click Install.
- 11. Click I Agree. Click Next.
- 13. Place a checkmark next to Run Wireshark 1.8.0 (32-bit) then click Finish. Click the Capture menu, and select Interfaces.
- 14. Put a check in this box. Click Start. You will now see packets captured.
- 15. You can view usernames, passwords, and other information using Wireshark. Open an internet browser and enter the URL www.yahoo.com then search for the word treasure. Return to Wireshark and Click Edit and Find Packet
- 16. Click String, after Filter enter Treasure, click Find. Treasure is found on a page that was just visited.
- 17. Double-click on the highlighted packet for more information. Click the capture menu and select Stop.