Features of AWS - IAM
•
0 j'aime•383 vues
Why cloud hacks will keep happening? Unless you learn AWS IAM - you run the risk of running AWS resources insecurely! You can learn Learn How To Avoid Any Costly Security Breaches Which Can Affect Your Business In As Little As In 3 Hours Or Less" in this course Aws IAM the-cloud-engineer-secure-cloud-handbook "90% OFF" here - http://rite.ly/wTKL About Website: https://courses.tetranoodle.com/ Facebook: https://www.facebook.com/tetranoodletech Twitter: https://twitter.com/TETRANOODLE Linkedin: https://www.linkedin.com/company/tetranoodle/ YouTube: https://www.youtube.com/channel/UCAiIK20nDamhq70NMnLG8wA Instagram: https://www.instagram.com/tetranoodle/ Udemy: https://www.udemy.com/user/manujaggarwal
Signaler
Partager
Signaler
Partager
Télécharger pour lire hors ligne
Recommandé
Recommandé
Contenu connexe
Tendances
Tendances (20)
Foundations - Understanding the Critical Building Blocks of AWS Identity & Go...

Foundations - Understanding the Critical Building Blocks of AWS Identity & Go...
Identity and Access Management: The First Step in AWS Security

Identity and Access Management: The First Step in AWS Security
Introduction to Identity and Access Management (IAM)

Introduction to Identity and Access Management (IAM)
The 1%: Identity and Governance Patterns from the Most Advanced AWS Customers...

The 1%: Identity and Governance Patterns from the Most Advanced AWS Customers...
How to Implement a Well-Architected Security Solution.pdf

How to Implement a Well-Architected Security Solution.pdf
Plus de Manuj Aggarwal
Plus de Manuj Aggarwal (7)
IaaS Cloud Computing With OpenStack - Master Class (Handout)

IaaS Cloud Computing With OpenStack - Master Class (Handout)
Dernier
Mehran University Newsletter is a Quarterly Publication from Public Relations OfficeMehran University Newsletter Vol-X, Issue-I, 2024

Mehran University Newsletter Vol-X, Issue-I, 2024Mehran University of Engineering & Technology, Jamshoro
https://app.box.com/s/7hlvjxjalkrik7fb082xx3jk7xd7liz3TỔNG ÔN TẬP THI VÀO LỚP 10 MÔN TIẾNG ANH NĂM HỌC 2023 - 2024 CÓ ĐÁP ÁN (NGỮ Â...

TỔNG ÔN TẬP THI VÀO LỚP 10 MÔN TIẾNG ANH NĂM HỌC 2023 - 2024 CÓ ĐÁP ÁN (NGỮ Â...Nguyen Thanh Tu Collection
Dernier (20)
Ecological Succession. ( ECOSYSTEM, B. Pharmacy, 1st Year, Sem-II, Environmen...

Ecological Succession. ( ECOSYSTEM, B. Pharmacy, 1st Year, Sem-II, Environmen...
ICT Role in 21st Century Education & its Challenges.pptx

ICT Role in 21st Century Education & its Challenges.pptx
Measures of Central Tendency: Mean, Median and Mode

Measures of Central Tendency: Mean, Median and Mode
Beyond the EU: DORA and NIS 2 Directive's Global Impact

Beyond the EU: DORA and NIS 2 Directive's Global Impact
This PowerPoint helps students to consider the concept of infinity.

This PowerPoint helps students to consider the concept of infinity.
Asian American Pacific Islander Month DDSD 2024.pptx

Asian American Pacific Islander Month DDSD 2024.pptx
Food Chain and Food Web (Ecosystem) EVS, B. Pharmacy 1st Year, Sem-II

Food Chain and Food Web (Ecosystem) EVS, B. Pharmacy 1st Year, Sem-II
Measures of Dispersion and Variability: Range, QD, AD and SD

Measures of Dispersion and Variability: Range, QD, AD and SD
TỔNG ÔN TẬP THI VÀO LỚP 10 MÔN TIẾNG ANH NĂM HỌC 2023 - 2024 CÓ ĐÁP ÁN (NGỮ Â...

TỔNG ÔN TẬP THI VÀO LỚP 10 MÔN TIẾNG ANH NĂM HỌC 2023 - 2024 CÓ ĐÁP ÁN (NGỮ Â...
Features of AWS - IAM
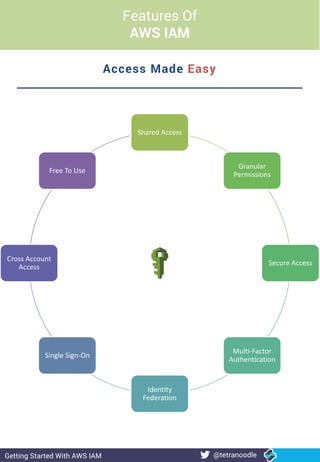
- 1. Shared Access Granular Permissions Secure Access Multi-Factor Authentication Identity Federation Single Sign-On Cross Account Access Free To Use Access Made Easy @tetranoodle Features Of AWS IAM Getting Started With AWS IAM
- 2. @tetranoodle AWS IAM Identities AWS IAM Identities IAM Users IAM Groups IAM Roles Root Account Temporary Credentials
- 3. @tetranoodle AWS IAM Policy Design AWS IAM Access Management Policy A Policy B Group A Group B Group C Policy C
- 4. @tetranoodle Securing AWS Resources AWS IAM Securing AWS Resources Multi Factor Authentication Web Identity Federation Key Encryption Management Password Policies Policy Simulator AWS Provides the following to secure resources :