RSA alogrithm
•Télécharger en tant que DOC, PDF•
0 j'aime•726 vues
Rivest, Shamir, Adleman (RSA) Algorithm coding procedure in the visual studio dotnet
Signaler
Partager
Signaler
Partager
Recommandé
Recommandé
Contenu connexe
Tendances
Tendances (20)
Web application security: Threats & Countermeasures

Web application security: Threats & Countermeasures
High Availability Asterisk and FreePBX on Microsoft Azure

High Availability Asterisk and FreePBX on Microsoft Azure
En vedette
En vedette (20)
Linux Mint System Components and Environmental Subsystems

Linux Mint System Components and Environmental Subsystems
Chapter 3: Block Ciphers and the Data Encryption Standard

Chapter 3: Block Ciphers and the Data Encryption Standard
Similaire à RSA alogrithm
Similaire à RSA alogrithm (20)
Rivest Shamir Adleman Algorithm and its variant : DRSA.pptx

Rivest Shamir Adleman Algorithm and its variant : DRSA.pptx
Principles of public key cryptography and its Uses

Principles of public key cryptography and its Uses
Information and data security public key cryptography and rsa

Information and data security public key cryptography and rsa
Image and text Encryption using RSA algorithm in java 

Image and text Encryption using RSA algorithm in java
Plus de Senthil Kanth
Plus de Senthil Kanth (20)
Wireless Communication and Networking by WilliamStallings Chap2

Wireless Communication and Networking by WilliamStallings Chap2
Introduction to wireless application protocol (wap)ogi

Introduction to wireless application protocol (wap)ogi
XML Programming WML by Dickson K.W. Chiu PhD, SMIEEE

XML Programming WML by Dickson K.W. Chiu PhD, SMIEEE
Dernier
Dernier (20)
Asian American Pacific Islander Month DDSD 2024.pptx

Asian American Pacific Islander Month DDSD 2024.pptx
Unit-V; Pricing (Pharma Marketing Management).pptx

Unit-V; Pricing (Pharma Marketing Management).pptx
ICT Role in 21st Century Education & its Challenges.pptx

ICT Role in 21st Century Education & its Challenges.pptx
On National Teacher Day, meet the 2024-25 Kenan Fellows

On National Teacher Day, meet the 2024-25 Kenan Fellows
Energy Resources. ( B. Pharmacy, 1st Year, Sem-II) Natural Resources

Energy Resources. ( B. Pharmacy, 1st Year, Sem-II) Natural Resources
Micro-Scholarship, What it is, How can it help me.pdf

Micro-Scholarship, What it is, How can it help me.pdf
Presentation by Andreas Schleicher Tackling the School Absenteeism Crisis 30 ...

Presentation by Andreas Schleicher Tackling the School Absenteeism Crisis 30 ...
Unit-IV; Professional Sales Representative (PSR).pptx

Unit-IV; Professional Sales Representative (PSR).pptx
Beyond the EU: DORA and NIS 2 Directive's Global Impact

Beyond the EU: DORA and NIS 2 Directive's Global Impact
RSA alogrithm
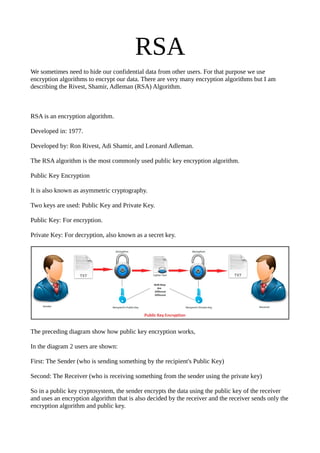
- 1. RSA We sometimes need to hide our confidential data from other users. For that purpose we use encryption algorithms to encrypt our data. There are very many encryption algorithms but I am describing the Rivest, Shamir, Adleman (RSA) Algorithm. RSA is an encryption algorithm. Developed in: 1977. Developed by: Ron Rivest, Adi Shamir, and Leonard Adleman. The RSA algorithm is the most commonly used public key encryption algorithm. Public Key Encryption It is also known as asymmetric cryptography. Two keys are used: Public Key and Private Key. Public Key: For encryption. Private Key: For decryption, also known as a secret key. The preceding diagram show how public key encryption works, In the diagram 2 users are shown: First: The Sender (who is sending something by the recipient's Public Key) Second: The Receiver (who is receiving something from the sender using the private key) So in a public key cryptosystem, the sender encrypts the data using the public key of the receiver and uses an encryption algorithm that is also decided by the receiver and the receiver sends only the encryption algorithm and public key.
- 2. But by using the public key, data can only be encrypted but not decrypted, and the data is only decrypted by the private key that only the receiver has. So no one can hack our data. In simple terms: Public Key: Shared with the public that wants to send us data. Private Key: Kept secret so that when someone sends us data encrypted by our Public Key, we can decrypt the data using the Private Key. HOW RSA WORKS Both users (sender and receiver) generates a public and private key. The following is the procedure for generating a public and private key (see flowchart). Generation of Public and Private key in RSA The flowcharts above shows how to generate a public and private key using RSA. After getting the public and private key the main thing is how to encrypt and decrypt using RSA. Encryption and Decryption in RSA
- 3. encrypt and decrypt.png Example of RSA: Here is an example of RSA encryption and decryption with generation of the public and private key. Generate public and private key: Encryption and Decryption
- 4. How to use the RSA Algorithm in a C# Windows Forms application 1. Open Visual Studio. 2. Select "File" -> "New" -> "Project..." or press "Ctrl +Shift +N". 3. Now select "Windows Forms application" from the Visual C# templates. 4. Now design the Windows Forms form such as follows: You need to make:
- 5. 3 TextBoxes for Plain Text, Encrypted Text and Decrypted Text and 2 Buttons. Now for the coding part. Coding 1. To use the RSA algorithm in C#, we need to add the following namespace: using System.Security.Cryptography; 2. Now make a function for Encryption. static public byte[] Encryption(byte[] Data, RSAParameters RSAKey, bool DoOAEPPadding) { try { byte[] encryptedData; using (RSACryptoServiceProvider RSA = new RSACryptoServiceProvider()) { RSA.ImportParameters(RSAKey); encryptedData = RSA.Encrypt(Data, DoOAEPPadding); } return encryptedData; } catch (CryptographicException e) { Console.WriteLine(e.Message); return null; } } 3. Now make a function for Decryption static public byte[] Decryption(byte[]Data, RSAParameters RSAKey, bool DoOAEPPadding) { try { byte[] decryptedData; using (RSACryptoServiceProvider RSA = new RSACryptoServiceProvider()) { RSA.ImportParameters(RSAKey); decryptedData = RSA.Decrypt(Data, DoOAEPPadding); } return decryptedData; } catch (CryptographicException e) { Console.WriteLine(e.ToString()); return null;
- 6. } } 4. Now make some variables into the class that are: UnicodeEncoding ByteConverter = new UnicodeEncoding(); RSACryptoServiceProvider RSA = new RSACryptoServiceProvider(); byte[] plaintext; byte[] encryptedtext; 5. Now handle the Click Event for the Encrypt Button with the following code: private void button1_Click(object sender, EventArgs e) { plaintext = ByteConverter.GetBytes(txtplain.Text); encryptedtext = Encryption(plaintext, RSA.ExportParameters(false), false); txtencrypt.Text = ByteConverter.GetString(encryptedtext); } 6. Now handle the Click Event for the Decrypt Button with the following code: private void button2_Click(object sender, EventArgs e) { byte[] decryptedtex = Decryption(encryptedtext, RSA.ExportParameters(true), false); txtdecrypt.Text = ByteConverter.GetString(decryptedtex); } Results
- 7. Plain Text: Encrypted Text: Decrypted Text:
