Download Full DevOps Survey Report
•
2 j'aime•670 vues
2017 DevSecOps Survey
Signaler
Partager
Signaler
Partager
Télécharger pour lire hors ligne
Recommandé
Contenu connexe
Tendances
Tendances (20)
DevOps vs Traditional IT Ops (DevOps Days ignite talk by Oliver White)

DevOps vs Traditional IT Ops (DevOps Days ignite talk by Oliver White)
Introduction To DevOps | Devops Tutorial For Beginners | DevOps Training For ...

Introduction To DevOps | Devops Tutorial For Beginners | DevOps Training For ...
Devops at SlideShare: Talk at Devopsdays Bangalore 2011

Devops at SlideShare: Talk at Devopsdays Bangalore 2011
Similaire à Download Full DevOps Survey Report
Similaire à Download Full DevOps Survey Report (20)
From Zero to DevSecOps: How to Implement Security at the Speed of DevOps 

From Zero to DevSecOps: How to Implement Security at the Speed of DevOps
From Zero to DevSecOps: How to Implement Security at the Speed of DevOps

From Zero to DevSecOps: How to Implement Security at the Speed of DevOps
Ericsson Technology Review: DevOps: fueling the evolution toward 5G networks

Ericsson Technology Review: DevOps: fueling the evolution toward 5G networks
Winning open source vulnerabilities without loosing your deveopers - Azure De...

Winning open source vulnerabilities without loosing your deveopers - Azure De...
Operationalize All the Network Things by Lori MacVittie

Operationalize All the Network Things by Lori MacVittie
The Illusion of Control: Seven Deadly Wastes in Your Devops Practice

The Illusion of Control: Seven Deadly Wastes in Your Devops Practice
Why DevSecOps Is Necessary For Your SDLC Pipeline?

Why DevSecOps Is Necessary For Your SDLC Pipeline?
DevSecOps Indonesia : Pain & Pleasure of doing AppSec in DevOps

DevSecOps Indonesia : Pain & Pleasure of doing AppSec in DevOps
Plus de Sonatype
Plus de Sonatype (20)
DevOps Friendly Doc Publishing for APIs & Microservices

DevOps Friendly Doc Publishing for APIs & Microservices
The Unrealized Role of Monitoring & Alerting w/ Jason Hand

The Unrealized Role of Monitoring & Alerting w/ Jason Hand
A Small Association's Journey to DevOps w/ Edward Ruiz

A Small Association's Journey to DevOps w/ Edward Ruiz
What's My Security Policy Doing to My Help Desk w/ Chris Swan

What's My Security Policy Doing to My Help Desk w/ Chris Swan
Characterizing and Contrasting Kuhn-tey-ner Awr-kuh-streyt-ors

Characterizing and Contrasting Kuhn-tey-ner Awr-kuh-streyt-ors
Static Analysis For Security and DevOps Happiness w/ Justin Collins

Static Analysis For Security and DevOps Happiness w/ Justin Collins
Automated Infrastructure Security: Monitoring using FOSS

Automated Infrastructure Security: Monitoring using FOSS
There is No Server: Immutable Infrastructure and Serverless Architecture

There is No Server: Immutable Infrastructure and Serverless Architecture
Continuous Everyone: Engaging People Across the Continuous Pipeline

Continuous Everyone: Engaging People Across the Continuous Pipeline
Dernier
Dernier (20)
The 7 Things I Know About Cyber Security After 25 Years | April 2024

The 7 Things I Know About Cyber Security After 25 Years | April 2024
Factors to Consider When Choosing Accounts Payable Services Providers.pptx

Factors to Consider When Choosing Accounts Payable Services Providers.pptx
Breaking the Kubernetes Kill Chain: Host Path Mount

Breaking the Kubernetes Kill Chain: Host Path Mount
Swan(sea) Song – personal research during my six years at Swansea ... and bey...

Swan(sea) Song – personal research during my six years at Swansea ... and bey...
Integration and Automation in Practice: CI/CD in Mule Integration and Automat...

Integration and Automation in Practice: CI/CD in Mule Integration and Automat...
Unblocking The Main Thread Solving ANRs and Frozen Frames

Unblocking The Main Thread Solving ANRs and Frozen Frames
Tech-Forward - Achieving Business Readiness For Copilot in Microsoft 365

Tech-Forward - Achieving Business Readiness For Copilot in Microsoft 365
WhatsApp 9892124323 ✓Call Girls In Kalyan ( Mumbai ) secure service

WhatsApp 9892124323 ✓Call Girls In Kalyan ( Mumbai ) secure service
FULL ENJOY 🔝 8264348440 🔝 Call Girls in Diplomatic Enclave | Delhi

FULL ENJOY 🔝 8264348440 🔝 Call Girls in Diplomatic Enclave | Delhi
Scaling API-first – The story of a global engineering organization

Scaling API-first – The story of a global engineering organization
Injustice - Developers Among Us (SciFiDevCon 2024)

Injustice - Developers Among Us (SciFiDevCon 2024)
08448380779 Call Girls In Civil Lines Women Seeking Men

08448380779 Call Girls In Civil Lines Women Seeking Men
08448380779 Call Girls In Friends Colony Women Seeking Men

08448380779 Call Girls In Friends Colony Women Seeking Men
Download Full DevOps Survey Report
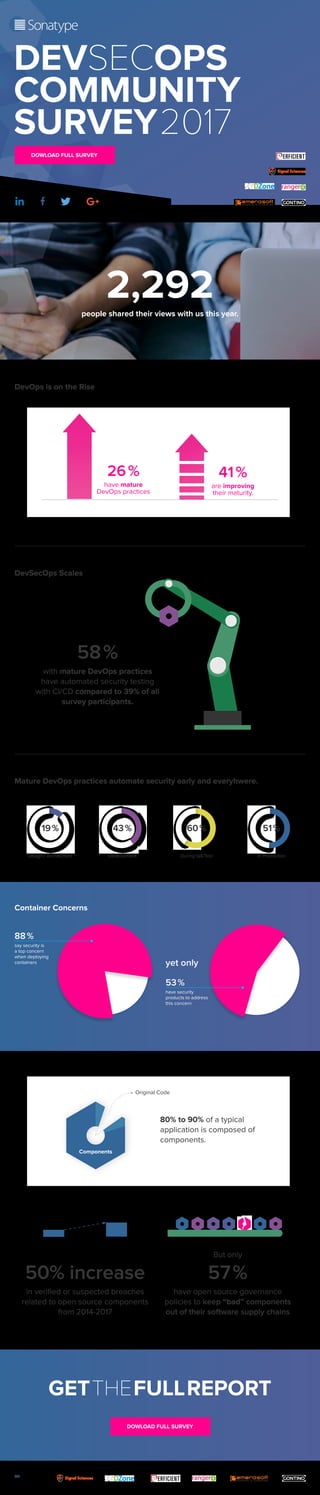
- 1. DOWLOAD FULL SURVEY DOWLOAD FULL SURVEY 41 % are improving their maturity. 26 % have mature DevOps practices 2,292people shared their views with us this year. 58 % with mature DevOps practices have automated security testing with CI/CD compared to 39% of all survey participants. Mature DevOps practices automate security early and everyhwere. Container Concerns DevSecOps Scales DevOps is on the Rise 19 % 43 % 51 %60 % Design / Architecture Development In ProductionDuring QA/Test 88 % say security is a top concern when deploying containers 53 % have security products to address this concern yet only 80% to 90% of a typical application is composed of components. But only 57 % have open source governance policies to keep “bad” components out of their software supply chains 50% increase in verified or suspected breaches related to open source components from 2014-2017
