LTE_Cloud_RAN_MAC_HLD
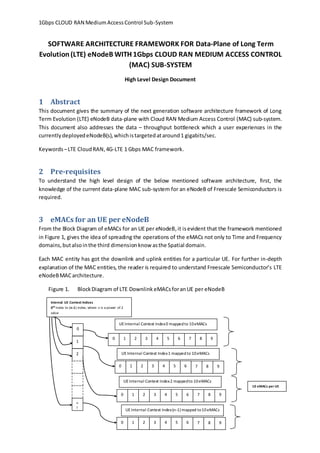
- 1. 1Gbps CLOUD RAN MediumAccessControl Sub-System SOFTWARE ARCHITECTURE FRAMEWORK FOR Data-Plane of Long Term Evolution(LTE) eNodeB WITH 1Gbps CLOUD RAN MEDIUM ACCESS CONTROL (MAC) SUB-SYSTEM High Level Design Document 1 Abstract This document gives the summary of the next generation software architecture framework of Long Term Evolution (LTE) eNodeB data-plane with Cloud RAN Medium Access Control (MAC) sub-system. This document also addresses the data – throughput bottleneck which a user experiences in the currentlydeployedeNodeB(s),whichistargetedataround1 gigabits/sec. Keywords–LTE CloudRAN,4G-LTE 1 Gbps MAC framework. 2 Pre-requisites To understand the high level design of the below mentioned software architecture, first, the knowledge of the current data-plane MAC sub-system for an eNodeB of Freescale Semiconductors is required. 3 eMACs for an UE per eNodeB From the Block Diagram of eMACs for an UE per eNodeB,it isevident that the framework mentioned in Figure 1, gives the idea of spreading the operations of the eMACs not only to Time and Frequency domains,butalsointhe third dimensionknow asthe Spatial domain. Each MAC entity has got the downlink and uplink entities for a particular UE. For further in-depth explanation of the MAC entities, the reader is required to understand Freescale Semiconductor’s LTE eNodeBMACarchitecture. Figure 1. BlockDiagram of LTE Downlink eMACsforanUE per eNodeB 0 1 2 n- 1 Internal UE Context Indices 0th index to (n-1) index; where n is a power of 2 value 0 1 2 3 4 5 6 7 8 9 10 eMACs per UE 0 1 2 3 4 5 6 7 8 9 0 1 2 3 4 5 6 7 8 9 UEInternal Context Index0 mappedto 10eMACs UEInternal Context Index1 mapped to 10eMACs UEInternal Context Index2 mappedto 10eMACs UEInternal Context Index(n-1) mapped to10eMACs 0 1 2 3 4 5 6 7 8 9
- 2. 1Gbps CLOUD RAN MediumAccessControl Sub-System 4 External C-RNTI to Internal UE Index mapping Note:Where ‘N’isany RNTIwithinthe range of 0 to 65535. Figure 2. Blockdiagramof External C-RNTItoInternal UE Index mapping In the above mentioned Figure 2, the block diagram of a particular C-RNTI mapped to a particular internal UE index of the eMACisprojected. 5 Downlink Hybrid Automatic Repeat request (HARQ) re- transmissionmemory model In the below mentioned Figure 3, the block diagram of the HARQ re-transmission memory model associatedwiththe variouskindsof UE(s) isshownbelow. 0 1 2 n- 1 1 0 1023 512 2 10 2 65535 65534 N 1 0 External UEC-RNTI Indices 0th index to 65535index Internal UE Context Indices 0th index to (n-1) index; where n is a power of 2 value; maximum value for ‘n’ is 65536
- 3. 1Gbps CLOUD RAN MediumAccessControl Sub-System HARQ re-transmission queuehead UE-ID #0 ; save the pointer to the HARQ –entity #0 and pointer to HARQ – entity #9 HARQ entity#4 HARQ process #0 HARQ process #N HARQ process #7 NULL NULL HARQ entity#5 HARQ process #0 HARQ process #N HARQ process #7 NULL NULL HARQ entity#6 HARQ process #0 HARQ process #N HARQ process #7 NULL NULL HARQ entity#7 HARQ process #0 HARQ process #N HARQ process #7 NULL NULL HARQ entity#2 HARQ process #0 HARQ process #N HARQ process #7 NULL NULL HARQ entity#3 HARQ process #0 HARQ process #N HARQ process #7 NULL NULL HARQ entity#1 HARQ process #0 HARQ process #N HARQ process #7 NULL NULL HARQ entity#0 HARQ process #0 HARQ process #N HARQ process #7 NULL NULL HARQ entity#8 HARQ entity#9 NULL NULL NULL A B NULL entity#0 NULL entity #0
- 4. 1Gbps CLOUD RAN MediumAccessControl Sub-System Note: Where ‘X’ is any value from 0 to “Maximum number of internal UE – indices which does not increase more than inclusive 65536” for MAC. Note:Where ‘N’isany value inthe range of “0 to7” for FDD MAC. Figure 3. Blockdiagramof the DL - HARQre-Transmission MemoryModel The HARQ memorymodel supportsa3-Tiersearch. First, it checks the availability of the UE entity, then secondly, it searches the HARQ eMAC entity database and, finally, it checks the availability of the HARQ process node in the re-tranmission queue. 6 Intended Audience 4G-LTE wirelessembeddedsoftware engineersand software architects. HARQ entity#0 HARQ process #0 HARQ process #N HARQ process #7 NULL NULL HARQ entity#3 HARQ process #0 HARQ process #N HARQ process #7 NULL NULL HARQ entity#6 HARQ process #0 HARQ process #N HARQ process #7 NULL NULL HARQ entity#8 HARQ process #0 HARQ process #N HARQ process #7 NULL NULL A B UE-ID # X; save the pointer to the HARQ –entity #0 and pointer to the last HARQ - entity # 8 NULL entity #0
- 5. 1Gbps CLOUD RAN MediumAccessControl Sub-System 7 Platform Statistics The Processor used is INTEL P2020 – 2.9 GHz with Microsoft Visual Studio C++ version 6 on Windows 7 – Professional (2009edition) It is evident from the performance that about 40 % of the CPU Usage on an average is occupied by the software framework. In the demonstration,amaximumof 5UE(s) have beenadmittedtothe system. 8 Author SubhankarSen