Middleware1
- 1. Middleware
- 2. Table of contents Overview Famous organisation in middle ware IBM oracle Uses Types remote procedure call Message oriented middleware Object request broker Transaction Processing Examples Platforms My conclusion
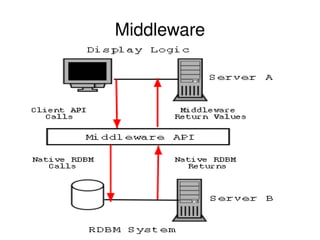
- 4. Consists of a set of enabling services
- 5. Allow multiple processes running on one or more machines to interact with each other
- 6. Middleware services are sets of distributed software
- 7. .
- 9. .
- 10. Cont... Middleware services provide a more functional set of API than OS and network services to allow an application to – Locate transparently across the network, providing interaction with other application or service Be independent from network services.
- 12. * IBM SOA Integration Services
- 13. * IBM IT Lifecycle Management and Governance Services
- 14. * IBM Information on Demand Infrastructure Services
- 15. * IBM Infrastructure Optimisation Services
- 16. B enefits # Increase business flexibility and decrease IT complexity # Reduce the costs of business integration # Simplify integration through IBM lifecycle methodologies and tool expertise # Improve the management of infrastructures
- 17. Cont... * Improve time to value and make the most of existing technology skills * Increase visibility and improve management and quality of IT services * Create an IT infrastructure designed to address regulatory requirements * Increase the value of existing IT investments * Enhance information availability, quality and value
- 18. Uses... Middleware services provide a more functional set of API to allow an application to: * Locate transparently across the network, thus providing interaction with another service or application * Be independent from network services * Be reliable and always available * Add complementary attributes like semantics
- 22. Transaction Processing (TP) monitors.
- 24. Allows a computer program to cause a subroutine or procedure to execute in another address space without the programmer
- 25. Explicitly coding the details for this remote interaction.
- 26. RPC 3/2/2008 Varun Arora @ SICSR M.Sc.(CA)2007-’09 T R A N S P O R T N E T W O R K N E T W O R K T R A N S P O R T RPC Stub RPC Stub Application Application Server Application specific procedure invocations and returns
- 28. sends a request message to a known remote server to execute a specified procedure with supplied parameters.
- 29. The remote server sends a response to the client,
- 30. the application continues its process.
- 31. Cont...
- 35. Reliability
- 37. The processing in a TPS must support an organization's operations
- 38. TP Monitors - Demonstration Database Processing Routines Client Client Client Client Client Transaction Processing Monitor
- 39. ORB It is a piece of middleware software that allows programmers to make program calls from one computer to another via a network.
- 40. ORB Client Application Remote Service (Object) ORB Locate service Activate service communicate Establish connection
- 42. Reduces complexity of applications spanning operating systems and network protocols by insulating them from un-necessary details.
- 44. Providing the directory, security, and administrative services required to support messaging.
- 45. MOM Queue MOM Provider Message Message Application A (Client A) Application B (Client B) A P P L I C A T I O N M O M A P I T R A N S P O R T N E T W O R K A P P L I C A T I O N M O M A P I T R A N S P O R T N E T W O R K
- 47. Flexible
- 48. Portability
- 49. Interoperability
- 52. Sonic MQ
- 53. MS MQ
- 55. MOM - Architecture Database Transaction J2EE Application Middle Layer Listener Listener Message Message Message Message Message Process C Process B Process A A P P L I C A T I O N 1 2 3 4 5 6 7 8 0 9 C B A Q1 Q2
- 57. Java’s database connectivity API : JDBC
- 58. Remote computation products - e.g ONC RPC, OSF RPC and RMI (Java Remote Method Invocation)
- 59. Distributed Computing Environment (DCE) products, Common Object Request Broker Architecture (CORBA), Distributed Component Object Model (DCOM)
- 60. TP - Monitors
- 61. Platforms * Enterprise JavaBeans (EJB) * Microsoft .NET * Microsoft .NET Micro Framework * CORBA
- 62. My conclusion Middleware is independent of network services While creating mashup we need to use app server for connecting the browser and client So there may be a chance of bottlenecks For this reason middleware is best for mashup techinques
