Network Protocol Analyzer
•Télécharger en tant que PPTX, PDF•
0 j'aime•943 vues
Signaler
Partager
Signaler
Partager
Recommandé
Recommandé
Contenu connexe
Tendances
Tendances (20)
Prensentation on packet sniffer and injection tool

Prensentation on packet sniffer and injection tool
Similaire à Network Protocol Analyzer
Similaire à Network Protocol Analyzer (20)
Basic ccna interview questions and answers ~ sysnet notes

Basic ccna interview questions and answers ~ sysnet notes
Internets Manage Communication Procedure and Protection that Crash on Servers

Internets Manage Communication Procedure and Protection that Crash on Servers
Plus de Sourav Roy
Plus de Sourav Roy (13)
Dernier
APM Welcome
Tuesday 30 April 2024
APM North West Network Conference, Synergies Across Sectors
Presented by:
Professor Adam Boddison OBE, Chief Executive Officer, APM
Conference overview:
https://www.apm.org.uk/community/apm-north-west-branch-conference/
Content description:
APM welcome from CEO
The main conference objective was to promote the Project Management profession with interaction between project practitioners, APM Corporate members, current project management students, academia and all who have an interest in projects.APM Welcome, APM North West Network Conference, Synergies Across Sectors

APM Welcome, APM North West Network Conference, Synergies Across SectorsAssociation for Project Management
Dernier (20)
Measures of Central Tendency: Mean, Median and Mode

Measures of Central Tendency: Mean, Median and Mode
Unit-IV; Professional Sales Representative (PSR).pptx

Unit-IV; Professional Sales Representative (PSR).pptx
Measures of Dispersion and Variability: Range, QD, AD and SD

Measures of Dispersion and Variability: Range, QD, AD and SD
Ecological Succession. ( ECOSYSTEM, B. Pharmacy, 1st Year, Sem-II, Environmen...

Ecological Succession. ( ECOSYSTEM, B. Pharmacy, 1st Year, Sem-II, Environmen...
Web & Social Media Analytics Previous Year Question Paper.pdf

Web & Social Media Analytics Previous Year Question Paper.pdf
APM Welcome, APM North West Network Conference, Synergies Across Sectors

APM Welcome, APM North West Network Conference, Synergies Across Sectors
Beyond the EU: DORA and NIS 2 Directive's Global Impact

Beyond the EU: DORA and NIS 2 Directive's Global Impact
Network Protocol Analyzer
- 8. Detecting ARP attack AS an easy and popular network attack,ARP attack may cause damages to the entire network,so before it brings losses we need to solve ARP attack as earliest time possible.(1)
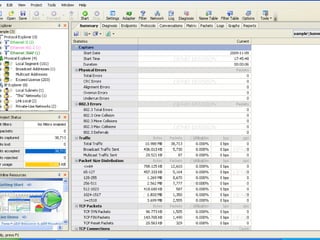
- 10. Monitor Network Utilization It is the ratio of the current network traffic to the maximum traffic that the port can handle,it indicates network bandwidth so we can understand whether network is busy,normal or idel.(3)
- 11. How To Get Top 10 Traffic Local Host When the network is getting slow we need to find out that who is using our bandwidth.(4)
- 12. Track down bittorrent If somebody in our local network is downloading files using bitTorrent,it will consume large amount of bandwidth,so we need to track down who is using bittorrent and recover normal network condition in time.(5)
