Advanced Computer Networking Guide
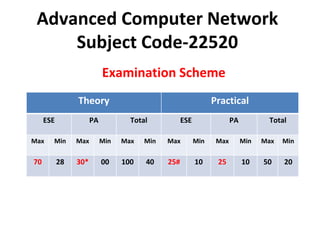
- 1. Advanced Computer Network Subject Code-22520 Examination Scheme Theory Practical ESE PA Total ESE PA Total Max Min Max Min Max Min Max Min Max Min Max Min 70 28 30* 00 100 40 25# 10 25 10 50 20
- 2. Syllabus Unit No. Unit Title Total Marks 1 Network Layer and Protocols 08 2 Next Generation IP 10 3 Unicast and Multicast Routing Protocols 14 4 Transport Layer Protocols 18 5 Application Layer Protocols 20
- 3. Unit -1: Network Layer and Protocols Total Marks-8 Topics and Sub-topics 1.1 IP Addressing : Address Space, Notations, Classfull addressing, Classless addressing, Network Address Translation (NAT). 1.2 Internet Protocol (IP): Datagram format, Fragmentation, Options. 1.3 ICMPv4 : Messages, Debugging Tools, ICMP Checksum. 1.4 Mobile IP: Addressing, Agents, Three Phases, Inefficiency in Mobile IP. 1.5 Virtual Private Network: VPN Technology.
- 4. . Revision • Network- A network is a set of devices (often referred to as nodes) connected by communication links. • A node can be a computer, printer, or any other device capable of sending and/or receiving data generated by other nodes on the network. A link can be a cable, air, optical fiber, or any medium which can transport a signal carrying information. • Network Criteria 1. Performance: Can be measured by transit time and response time. • Transit time is the amount of time required for a message to travel from one device to another. • Response time is the elapsed time between an inquiry and a response. • The performance of a network depends on the number of users, the type of transmission medium, the capacities of the connected hardware and the efficiency of the software. 2. Reliability: Is measured by the frequency of failures, the time it takes a link to recover from failure and the network robustness in a catastrophe. 3. Security: This refers to the ability to protect data from unauthorized access
- 5. . Protocols : • A protocol is synonymous with rule. It consists of a set of rules that govern data communications. It determines what is communicated, how it is communicated and when it is communicated. • Network Models: 1. OSI Reference Model 2. TCP/IP Model
- 7. . Network Layer • Position of Network Layer
- 8. • Duties/Functions of Network Layer
- 9. • Duties/Functions of Network Layer Continue… • Main responsibility of Network layer is to carry the data packets from the source to the destination without changing or using it. If the packets are too large for delivery, they are fragmented i.e., broken down into smaller packets. 1. Internetworking: It provides the logical connection between different types of the network. 2. Addressing: Addressing is help us to identify each device present on the internet uniquely. It is similar to a telephone system. The address used in the network layer should be uniquely and universally define the connection of a computer.
- 10. • Duties/Functions of Network Layer Continue…. 3. Routing: In a network, there are multiple routes available from a source to destination and one of them is to be chosen. The network layer decides, Which route to be taken. This is called routing. 4. Packetizing: The network layer encapsulates the packets received from upper-layer protocols and makes new packets. This is called Packetizing. It is done by a network layer protocol called IP (Internet Protocols). 5. Fragmenting: The sent datagram can travel through different networks. Each router decapsulates the IP datagram from the received frame. Then datagram is processed and encapsulated in another frame.
- 11. • Addressing Mechanism: • It is the prime responsibility of the network layer to assign unique addresses to different nodes in a network. • Four levels of addresses are used in an Internet employing TCP/IP Protocol: 1. Physical Address or Link Address (MAC Address): It is the address of a node defined by its LAN or WAN. A Media Access Control address is a hardware identifier that uniquely identifies each device on a network. Often found on a device’s NIC card. Physical address can be either unicast (one single recipient) , multicast (a group of recipient), or broadcast ( to be received by all systems in the network). 2. Logical Address : In the Internet a 32-bits or 128-bits address that can uniquely defined a host connected to the internet. The logical addresses can be either unicast, multicast or broadcast.
- 12. • Addressing Mechanism: Continue……. 3. Port Address: In the TCP/IP architecture, the label assigned to a process is called a port address. It is 16-bits in length. 4. Application Specific Addresses: they are designed for specific application such as e-mail addresses and the Universal Resource Locator(URL) e.g. www.msbte.com.
- 13. 1.1 IP Addressing • IP addressing is the method used to identify hosts and network devices. • Usually, computers communicate through the Internet. The packet(data) transmitted by the sender computer may pass through several LANs or WANs before reaching the destination computer. • For this level of communication, we need a global addressing scheme what we call logical addressing. • Two types of logical addresses are there: 1. IPv4 Addresses 2. IPv6 Addresses
- 14. 1.1.1 IP Address • An IP address is an address used to uniquely identify a device on a network. • An IP Address is 32-bit address consist of two parts: 1. Network ID- Identifies the network on which a host computer can be found. 2. Host ID- Identifies a specific device on the network indicated by the network ID. e.g. 145.25.10.100
- 15. • IPv4 Addresses : • An IPv4 address is a 32-bit address that uniquely and universally defines the connection of a device (for example, a computer or a router) to the Internet. • They are unique so that each address defines only one connection to the Internet. Two devices on the Internet can never have the same IPV4 address at the same time. • On the other hand, if a device operating at the network layer has m connections to the Internet, it needs to have m addresses, for example, a router. • The IPv4 addresses are universal in the sense that the addressing system must be accepted by any host that wants to be connected to the Internet. That means global addressing.
- 16. 1.1.2 Address Space • IPv4 has a certain address space. An address space is the total number of addresses used by the protocol. If a protocol uses N bits to define an address, the address space is 2N • IPv4 uses 32-bit address format, which means that the address space is 232 or 4,294,967,296 (more than 4 billion). 1.1.3.Notations There are three notations to show an IPv4 address: • Binary notation • Dotted decimal notation • Hexadecimal notation.
- 17. • IPv4 Addresses : (Continue…..) 1) Binary Notation(Base 2) • In binary notation, the IPv4 address is displayed as 32 bits. Each octet is often referred to as a byte. So it is common to hear an IPv4 address referred to a 4- byte address. The following is an example of an IPv4 address in binary notation: 01110111 10010101 00000001 00000011 2) Dotted-Decimal Notation(Base 256) • IPV4 addresses are usually written in decimal form with a decimal point (dot) separating the bytes since it’s more compatible. The following is an example: 119.149.1.3 (above one and this one is same just different notation) • Note: Each number in dotted-decimal notation is a value ranging from 0 to 255.
- 18. • IPv4 Addresses : (Continue…..) 3) Hexadecimal Notation(Base 16) • Each hexadecimal digit is equivalent to four bits. i.e. a 32 bit address has 8 hexadecimal digits. • This notation often used in network programming. • E.g. 77.95.01.03 (above one and this one is same just different notation)
- 19. Dotted-decimal notation and binary notation for an IPv4 address
- 20. Change the following IPv4 addresses from binary notation to dotted- decimal notation. Example 1.1 Solution We replace each group of 8 bits with its equivalent decimal number and add dots for separation.
- 21. Change the following IPv4 addresses from dotted-decimal notation to binary notation. Example 1.2 Solution We replace each decimal number with its binary equivalent.
- 22. Find the error, if any, in the following IPv4 addresses. Example 1.3 Solution a. There must be no leading zero (045). b. There can be no more than four numbers. c. Each number needs to be less than or equal to 255. d. A mixture of binary notation and dotted-decimal notation is not allowed.
- 23. 1.1.4 Classful Addressing: The 32 bit IP address is divided into five sub-classes. These are: • Class A • Class B • Class C • Class D • Class E • Each of these classes has a valid range of IP addresses. Classes D and E are reserved for multicast and experimental purposes respectively. The order of bits in the first octet determine the classes of IP address. • IPv4 address is divided into two parts: • Network ID • Host ID • The class of IP address is used to determine the bits used for network ID and host ID and the number of total networks and hosts possible in that particular class. Each ISP or network administrator assigns IP address to each device that is connected to its network.
- 24. • Classful Addressing: (Continued…) • Following figure shows the address space is divided into five classes.
- 25. Figure 3.2 Finding the classes in binary and dotted-decimal notation
- 26. • 1.2.1 IP Datagram format • Packets in network (Internet) layer are called datagrams. • A datagram is a variable length packet consisting of two parts namely, header and data. • The header is 20 to 60 bytes in length and contains information essential to routing and delivery.
- 27. • 1.2.2 IP Header format
- 28. • 1.2.2 IP Header format Continue…… 1. Version- • Version is a 4 bit field that indicates the IP version used. • The most popularly used IP versions are version-4 (IPv4) and version-6 (IPv6). • Only IPv4 uses the above header. • So, this field always contains the decimal value 4. 2. Header Length- • Header length is a 4 bit field that contains the length of the IP header. • It helps in knowing from where the actual data begins. • Minimum And Maximum Header Length- • The initial 5 rows of the IP header are always used. • So, minimum length of IP header = 5 x 4 bytes = 20 bytes. • The size of the 6th row representing the Options field vary.The size of Options field can go up to 40 bytes. So, maximum length of IP header = 20 bytes + 40 bytes = 60 bytes.
- 29. • 1.2.2 IP Header format Continue…… 3. Type Of Service- • Type of service is a 8 bit field that is used for Quality of Service (QoS). • 4 TOS bits and an unused bit that must be 0. The 4 TOS bits are: 1000 – Minimum delay 0100 – Maximum Throughput 0010 – Maximum Reliability 0001 – Minimize monetary cost 0000 – Normal service 4. Total Length- • Total length is a 16 bit field that contains the total length of the datagram (in bytes). • Total length = Header length + Payload length(Data Length)
- 30. • 1.2.2 IP Header format Continue…… 5. Identification- • Identification is a 16 bit field. • It is used for the identification of the fragments of an original IP datagram. • When an IP datagram is fragmented, Each fragmented datagram is assigned the same identification number. • This number is useful during the re assembly of fragmented datagrams. • It helps to identify to which IP datagram, the fragmented datagram belongs to. 6. Flags :The router fragment activity is controlled by following 3 flags: Sr. No. Flags Description 1 0 Reserved, must be zero 2 DF (Do not Fragment) 0 – Allow Fragmentation 1 – Do not Allow Fragmentation 3 MF (More Fragments) 0- this is the last fragment of datagram 1 – additional fragments will follow.
- 31. • 1.2.2 IP Header format Continue…… 7. Fragment Offset- • Fragment Offset is a 13 bit field. • It indicates the position of a fragmented datagram in the original unfragmented IP datagram. • The first fragmented datagram has a fragment offset of zero. • Fragment offset for a given fragmented datagram = Number of data bytes ahead of it in the original unfragmented datagram • Fragment offset field value = Fragment Offset / 8
- 32. • 1.2.2 IP Header format Continue…… 8. Time To Live- • Time to live (TTL) is a 8 bit field. • It indicates the maximum number of hops a datagram can take to reach the destination. • The main purpose of TTL is to prevent the IP datagrams from looping around forever in a routing loop. • The value of TTL is decremented by 1 when- Datagram takes a hop to any intermediate device having network layer. Datagram takes a hop to the destination. • If the value of TTL becomes zero before reaching the destination, then datagram is discarded. 9. Protocol- • Protocol is a 8 bit field. • It tells the network layer at the destination host to which protocol the IP datagram belongs to. • In other words, it tells the next level protocol to the network layer at the destination side. • Protocol number of ICMP is 1, IGMP is 2, TCP is 6 and UDP is 17.
- 33. • 1.2.2 IP Header format Continue…… 10. Header Checksum- • Header checksum is a 16 bit field. • It contains the checksum value of the entire header. • The checksum value is used for error checking of the header. • At each hop, The header checksum is compared with the value contained in this field. If header checksum is found to be mismatched, then the datagram is discarded. Router updates the checksum field whenever it modifies the datagram header. • The fields that may be modified are- TTL Options Datagram Length Header Length Fragment Offset
- 34. • 1.2.2 IP Header format Continue…… 11. Source IP Address- • Source IP Address is a 32 bit field. • It contains the logical address of the sender of the datagram. 12. Destination IP Address- • Destination IP Address is a 32 bit field. • It contains the logical address of the receiver of the datagram. 13. Options- • Options is a field whose size vary from 0 bytes to 40 bytes. • This field is used for several purposes such as- 1. Record route 2. Source routing 3. Padding
- 35. • 1.2.2 IP Header format Continue…… 1. Record Route- • A record route option is used to record the IP Address of the routers through which the datagram passes on its way. • When record route option is set in the options field, IP Address of the router gets recorded in the Options field. 2. Source Routing- • A source routing option is used to specify the route that the datagram must take to reach the destination. • This option is generally used to check whether a certain path is working fine or not. • Source routing may be loose or strict.
- 36. • 1.2.2 IP Header format Continue…… 3. Padding- • Addition of dummy data to fill up unused space in the transmission unit and make it conform to the standard size is called as padding. • Options field is used for padding. Example- • When header length is not a multiple of 4, extra zeroes are padded in the Options field. • By doing so, header length becomes a multiple of 4. • If header length = 30 bytes, 2 bytes of dummy data is added to the header. • This makes header length = 32 bytes. • Then, the value 32 / 4 = 8 is put in the header length field. • In worst case, 3 bytes of dummy data might have to be padded to make the header length a multiple of 4.
- 37. • 1.2.2 Fragmentation • IP Fragmentation is a process of dividing the datagram into fragments during its transmission. • It is done by intermediary devices such as routers at the destination host at network layer.
- 38. • 1.2.2 Fragmentation Continue………… • Need- • Each network has its maximum transmission unit (MTU). • It dictates the maximum size of the packet that can be transmitted through it. • Data packets of size greater than MTU can not be transmitted through the network. • So, datagrams are divided into fragments of size less than or equal to MTU. • Datagram Fragmentation- • When router receives a datagram to transmit further, it examines the following- 1. Size of the datagram 2. MTU of the destination network 3. DF bit value in the IP header
- 39. • 1.2.2 Fragmentation Continue………… Then, following cases are possible- Case-01: • Size of the datagram is found to be smaller than or equal to MTU. • In this case, router transmits the datagram without any fragmentation. Case-02: • Size of the datagram is found to be greater than MTU and DF bit set to 1. • In this case, router discards the datagram. Case-03: • Size of the datagram is found to be greater than MTU and DF bit set to 0. • In this case, router divides the datagram into fragments of size less than or equal to MTU. • Router attaches an IP header with each fragment making the following changes in it. • Then, router transmits all the fragments of the datagram.
- 40. • 1.2.2 Fragmentation Continue………… • Changes Made By Router- Router makes the following changes in IP header of each fragment- 1. It changes the value of total length field to the size of fragment. 2. It sets the MF bit to 1 for all the fragments except the last one. 3. For the last fragment, it sets the MF bit to 0. 4. It sets the fragment offset field value. 5. It recalculates the header checksum. • Reassembly of Fragments: • It takes place only at destination and not at routers since packets take independent path, so all may not meet at a router and hence need of fragmentation may arise again.
- 41. • 1.2.2 Fragmentation Continue………… • Reassembly Algorithm- Receiver applies the following steps for reassembly of all the fragments- 1. It identifies whether datagram is fragmented or not using MF bit and Fragment offset field. 2. It identifies all the fragments belonging to the same datagram using identification field. 3. It identifies the first fragment. Fragment with offset field value = 0 is the first fragment. 4. It identifies the subsequent fragments using total length, header length and fragment offset. 5. It repeats step-04 until MF bit = 0.
- 42. • 1.2.3 Options • The IP header has 2 parts namely , a fixed part and a variable part. • Fixed part is 20 byte long, and variable part is comprises the options, which can be maximum of 40 bytes. • It is not required for a datagram. They can be used for network testing and debugging. • Figure a shows format of option. 8 Bits 8 Bits Variable Length Type Length Value 1 (Copy) 2 (Class) 5 (Number)
- 43. • 1.2.3 Options Continue…. • The various fields in option format are as follows: 1. Type : • It is 8 bit long and contains three subfields namely copy, class and number. a) Copy (1 bit) b) Class (2 bits) c) Number (5 bits) a) Copy : Copy Meaning 0 Copy Option field only in first fragment. 1 Copy Option field in all fragments.
- 44. • 1.2.3 Options Continue…. b) Class : It is 2-bit subfield used to define purpose of option. Class Meaning 00 Datagram Control 01 Not defined or reserved 10 Debugging and management 11 Not defined or reserved
- 45. • 1.2.3 Options Continue…. c) Number : This is 5- bit subfield used for defining the type of option. • This subfield has 32 possible values but currently only 6 types are defined. Number Meaning 00000 End of option. 00001 No option. 00011 Loose source route. 00100 Timestamp. 00111 Record root. 01001 Strict source route.
- 46. • 1.2.3 Options Continue…. 2. Length: • This 8-bit field is used for defining the total length of option with the type field and length field included. • The length field will not be present in all the option types. 3. Value: • This is variable length field which contains the specific data which is required by that option. • The value field will not be present in all the option types.
- 47. 1.3 ICMPv4 • Internet Control Message Protocol (ICMP) works in the network layer of the OSI model and the internet layer of the TCP/IP model. • It is used to send control messages to network devices and hosts. • Routers and other network devices monitor the operation of the network. When an error occurs, these devices send a message using ICMP. • Messages that can be sent include "destination unreachable", "time exceeded", and "echo requests". • ICMP is a network layer protocol. • ICMP messages are not passed directly to the data link layer. The message is first encapsulated inside the IP datagram before going to the lower layer.
- 48. 1.3 ICMPv4 Continue…. 1.3.1 Functions of ICMP: 1. Announce Network Errors : Such as host or entire portion of the network being unreachable, due to some type of failure. 2. Announce Network Congestion : When router begins buffering too many packets, due to inability to transmit them as fast as they are being received, it will generate ICMP source quench messages. Directed at the sender, these messages should cause the rate of packet transmission to be slowed. 3. Announce Troubleshooting: ICMP supports Echo function, which just sends a packet on a roundtrip between two hosts. Ping tool will transmit a series of packets, measuring average round-trip times and computing loss percentages. 4. Announce Timeouts: If an IP packet’s TTL field drops to zero, the router discarding the packet will often generate an ICMP packet announcing this fact.
- 49. 1.3 ICMPv4 Continue…. 1.3.2 ICMP Message Encapsulation: • ICMP is a network layer protocol. • ICMP messages are not passed directly to the data link layer. The message is first encapsulated inside the IP datagram before going to the lower layer. • ICMP Message Format: Following figure shows the general ICMP message format.
- 50. 1.3 ICMPv4 Continue…. • Fields in message format of ICMPv4 are explained below: 1. Type − The type field identifies the type of the message. 2. Code − The code field in ICMP describes the purpose of the message. 3. Checksum − The checksum field is used to validate ICMP messages. 4. The Rest of header is specific for each message type. 5. Data in error messages carries information for finding original packet that had error. Data in query messages carries extra information based on type of query. 1.3.2.1 Types of ICMP Messages: • Error-reporting message − This message report problems that a router or a host (destination) may encounter when it processes an IP packet. • Query Message − The query messages, which occur in pairs, helps a host or a network manager to get specific information from a router or another host. • Following table lists the ICMP messages in each category.
- 51. 1.3 ICMPv4 Continue…. Sr. No. Message Type Description Error Reporting Messages: 1. Destination unreachable 3 Packet could not be delivered. 2. Source quench 4 Choke Packet 3. Redirect 5 Teach a router about geography. 4. Time exceeded 11 Time to live field hit 0. 5. Parameter Problem 12 Invalid header field. Query Messages: 1. Echo Request 8 or 0 Ask a machine if it is alive 2. Echo Reply 8 or 0 Yes, I am alive 3. Timestamp Request 13 or 14 Same as Echo request, but with timestamp. 4. Timestamp Reply 13 or 14 Same as Echo reply, but with timestamp.
- 52. 1.3 ICMPv4 Continue…. A. Error Reporting Messages: 1. Source Quench − It requests to decrease the traffic rate of message sending from source to destination. 2. Time Exceeded − When fragments are lost in a network the fragments hold by the router will be dropped and then ICMP will take the source IP from the discarded packet and inform the source, that datagram is discarded due to the time to live field reaches zero, by sending time exceeded message. 3. Destination Unreachable − This error message indicates that the destination host, network, or port number that is specified in the IP packet is unreachable. This may happen due to the destination host device is down, an intermediate router is unable to find a path to forward the packet, and a firewall is configured to block connections from the source of the packet. 4. Parameter Problem – indicates that an illegal values has been detected in the header field indicates a bug in the sending host’s IP software. 5. Redirect Message − A redirect error message is used when a router needs to tell a sender that it should use a different path for a specific destination. It occurs when the router knows a shorter path to the destination.
- 53. 1.3 ICMPv4 Continue…. B. Query Messages: • The query messages occur in pairs and provide specific information from the intermediate devices to the source device. 1. Echo-Request and Echo-Reply Message: These messages help resolve network diagnostic issues. 2. Timestamp Request and Reply: These time stamp requests and reply messages help determine the round trip time between the devices.
- 54. 1.3 ICMPv4 Continue…. 1.3.3 Debugging Tools: • 2 Tools are used. 1. Ping- • It sends out pings, also referred to as echo request messages -- and then measures the amount of time it takes the message to reach its destination and return to the source. • These replies are called echo reply messages. Pings are useful for gathering latency information about a specific device. Unlike traceroute, though, ping does not provide picture maps of the routing layout. • The ping can calculate the Round-trip time. Round-trip time(RTT) = Departure time of packet – Arrival time of packet e.g. ping google.com • It tells the number of packets received, the total time, and the RTT minimum, maximum and average.
- 55. 1.3 ICMPv4 Continue…. 2. Traceroute or Tracert : • From source to the destination to trace the path of packet in Unix, the traceroute command and in windows tracert command can be used. • The traceroute utility is used to display the physical routing path between two internet devices communicating with each other. • It maps out the journey from one router to another -- sometimes called a hop. • Using traceroute to diagnose network problems can help administrators locate the source of a network delay. • Traceroute uses two error messages namely, time exceeded and destination unreachable. • E.g. tracert google.com
- 56. 1.4 Mobile IP • Mobile IP is a communication protocol that enables a host to move from one network to another while still being connected to its home network. • Mobile IP allows a mobile host to communicate with the remote host being in a foreign network. • It is the extension of Internetworking Protocol (IP) that boosts mobile communication. • Why do we need Mobile IP? • Mobile IP is an advanced version of IP. • IP addresses were designed for the stationary host that always remains attached to one specific network. • The prefix of the IP address identifies the network to which the host belongs. The suffix of the IP address identifies the particular host in the corresponding network.
- 57. 1.4 Mobile IP Continue….. • What if the host moved to another network? Its IP address would no longer be valid and the host would not be able to communicate with any remote host. • Thus, we need to modify the structure of the IP address. The two proposed solutions to modify IP address are: 1. Changing the IP Address: • Changing the IP address each time the host enters a new network. • This attempt was not as successful as it has several drawbacks. • Every time the computer enters a new network it has to reboot. We have to keep revising the DNS table to let every host on the internet have knowledge about changes. Each time we have to change the configuration files. If the host moves to another network in-between the transmission of data, the data exchange would be interrupted.
- 58. 1.4 Mobile IP Continue….. 2. Two Addresses : • This solution is more feasible here, a mobile host will have two addresses: a) Home Address and b) Care of Address/Temporary address. • The home address is an original IP address of the mobile host, and the temporary address is called as the care of address. • A temporary address (care-of address) that would identify the host in the foreign network. The care-of address will keep on changing whenever the host will move to a new network. • The second solution contributes to the design of Mobile IP. It allows a host to move to another network by maintaining its original IP address and still is able to communicate with the remote hosts over the internet.
- 59. 1.4 Mobile IP Continue….. • Entities of Mobile IP - The functional entities in the Mobile IP protocol are: 1. Home Network is a network to which the mobile host actually belongs. It is a permanent network of the mobile host. 2. Foreign Network is a new network into which the mobile host has moved. 3. Remote Network is a network which is neither the home network nor the foreign network. 4. Mobile Host is a host of the home network which has moved to the foreign network. 5. Remote Host is a host in a remote network. 6. Home Agent is a router attached to the home network that allows the mobile host to send and receive data from the remote host over the internet. 7. Foreign Agent is a router attached to the foreign network that allows a mobile host to send and receive data from a remote host over the internet. 8. Care-of address is a temporary IP address provided by the foreign agent to the mobile host till it is in the foreign network. 9. Home Address is the address of the mobile host in its home network.
- 60. 1.4 Mobile IP Continue….. • Working • Mobile IP communication protocol allows the mobile host to communicate with the remote host even if it is in a network other than its home network. If a mobile host wants to communicate with the remote host being itself in the foreign network, then it has to go through three phases: 1. Phase I : Agent Discovery (Step 1 to 4) • Agent discovery is the first phase and requires the involvement of a mobile host, a home agent and a foreign agent. This phase also has two sub-phases as described below: • The mobile host has to discover the home agent’s address before it moves away from the home network (step 1 and 2) • As the mobile host moves to a new network (foreign network), it has to discover the foreign agent’s address and also the care-of address (step 3 and 4).
- 62. 1.4 Mobile IP Continue….. • The agent discovery phase includes two types of messages: agent advertisement and agent solicitation. a) Agent Advertisement • A simple router advertises its existence on the network with the ‘ICMP router advertisement’ packet. If the router is playing the role of an agent, it ‘appends’ the agent advertisement message to the ICMP advertisement packet. • If the advertisement is done by a foreign agent, then it sends a ‘list of addresses’ available as care-of addresses. From this list of addresses, the mobile host has to choose one. The announcement of the care-of address chosen by the mobile host is done in the registration request.
- 63. 1.4 Mobile IP Continue….. b) Agent Solicitation • In case, if a host in the network doesn’t receive the ‘router ICMP advertisement’ packet. The host can initiate itself by sending the ‘router ICMP solicitation packet’. If a mobile host has not received the ‘agent advertisement’, it can use the ‘router ICMP solicitation packet’ to send the ‘agent solicitation’ message. 2. Phase-II : Registration (steps 5 to 8): • This is the second phase of mobile communication. The mobile host first moves to the foreign network and discovers the foreign agent ( Phase-I). • After this is must go to registration phase, which corresponds to steps 5 to 8. • The four aspects of registration are as follows: i. Registration of mobile host with foreign agent (step 5). ii. Registration of mobile host with its home agent. This is normally done by the foreign agent on behalf of mobile host (step 6).
- 64. 1.4 Mobile IP Continue….. iii. The reply packet is sent from the ‘home agent’ to the ‘mobile host’ via a ‘foreign agent’. This registration reply has the confirmation of whether the request is accepted or denied. (step 7 and 8). • The mobile host has to renew its registration if it has expired. While returning back to the home network the mobile host has to cancel or deregister its registration. 3. Phase-III : Data Transfer: • Now finally, after the agent discovery and registration process, the mobile host is in the foreign network and can communicate with the remote host. i. From Remote Host to Home Agent : • Consider that the ‘remote host’ wants to send a data packet to the ‘mobile host’ unaware that the mobile host is not in its home network. • The remote host would definitely send the packet with its own address in the source address field and the mobile host’s home address in the destination address field of the packet.
- 65. 1.4 Mobile IP Continue….. • As the mobile host is not it’s the home network, the packet sent by the remote host is received by the home agent on behalf of the mobile host. • the mobile communication between the remote host and home agent has been marked by a thick path as “1” in fig. • Figure :Data transfer from remote host to home agent
- 66. 1.4 Mobile IP Continue….. ii. From Home to Foreign Agent : • The ‘home agent’ encapsulates the received IP datagram into another IP datagram (with the home agent’s address in the source address field and the foreign agent address in the destination address field) and relays it to the foreign agent as shown by the thick path marked by “2” in above fig. iii. From Foreign Agent to Mobile Host : • The foreign agent receives the packet, removes the encapsulation and sees the home address of the mobile host in the destination address field of the original packet sent by the remote host. • The foreign agent reviews its registry table, observes which care-of address has been registered to the corresponding home address, and then forwards the corresponding mobile host packet as shown by the thick path marked by “3” in above fig.
- 67. 1.4 Mobile IP Continue….. iv. From Mobile Host to Remote Host : • if a mobile host being in the foreign network wants to reply or communicate with the remote host, it simply prepares a packet and puts its home address in the source address field of the packet and the remote host’s address in the destination address field of the packet. The mobile host then directly sends the packet from the foreign network to the remote host as shown by thick path “4” in fig. • Transparency : • The movement of a mobile host from one network to another is transparent to the entire internet as the internet is totally unaware of the movements of the host.
- 68. 1.4 Mobile IP Continue….. • Advantages and Disadvantages of Mobile IP • Advantages 1. A user with its network devices can move to any other network without losing its connection with its home address. 2. Mobile IP provides transparency while the data transfer process. It hides the fact that the mobile host is not in its home network and is communicating from a foreign network. • Disadvantages 1. When the ‘remote host’ and ‘mobile host’ both are in a foreign network and still the data transfer is occurring through the ‘home agent’ then the data packet has to travel more distance though both the host are in the same network. 2. As we have seen above, if the mobile host in the foreign network wants to send the data packet to the remote host it sends it directly from the foreign network with its home address as the source and the remote host address in the destination. But, if a remote host wants to send a packet to a mobile host in a foreign network, the data packet has to travel to the mobile host via its home agent. So, here it has to travel the extra distance.
- 69. 1.4 Mobile IP Continue….. • Inefficiency in Mobile IP: • The communication done with the help of mobile IP can be moderately and severely inefficient. • The case of moderate inefficiency is called as the Triangle Routing, or Dog Leg Routing whereas the case of severe inefficiency called as Double Crossing or 2X. 1. Double Crossing or 2X : • Consider a situation in which a remote host wants to communicates with a mobile host that has moved to the same network as the remote host as shown in fig. • A mobile host can send a packet directly to the remote host. Therefore there is no efficiency; the communication is local. • But if the remote host sends a packet to the mobile host then it cannot do so directly (via the dotted direct path in fig. 1.4.3)
- 70. 1.4 Mobile IP Continue….. • Instead the remote host has to send the packet first home agent (path 1) and home agent will route the packet to the mobile host(path 2). • In this case the packet crosses the Internet twice. Thus resources are used twice unnecessarily in this communication which reduces the efficiency severely. • Hence the double cross case is called as the case of severe efficiency. Figure 1.4.3 Double Crossing or 2X.
- 71. 1.4 Mobile IP Continue….. 2. Triangle Routing or Dog Leg Routing: • It is a case of moderate inefficiency. • Occurs when the remote host wants to send a packet to the mobile host that is not attached to the same network as the mobile host as shown in fig. • When the mobile host sends a packet to the remote host it can do so directly. There is no efficiency . • But when the remote host sends a packet to the mobile host the packet goes from the remote host to the home agent and then to the mobile host as shown in fig. 1.4.4. • Thus the packet has to travel along the two sides of a triangle instead of only one which is the direct path shown by dotted line in fig.
- 72. 1.4 Mobile IP Continue….. Figure 1.4.4 Triangle Routing • Solution : • The remote host must know the mobile host’ s care-of address. • Send packet using the mobile host’ s care-of address. • The home agent can tell the remote host about this information by the update binding packet. • However, when the mobile host moves, its care-of address may be changed n The home agent needs to send a warning packet to the remote host to inform it.